The types of digital fraud threats that businesses face in 2024 are becoming increasingly sophisticated. For example, deep fakes can spoof a user’s ID and gain access to sensitive data.
For businesses, fraud and identity theft can cause severe damage to their finances and reputations. The financial risks are clear. According to the University of Portsmouth, in 2021, fraud cost the world economy more than $5.4 trillion.
For customers, identity theft and identity fraud can have devastating consequences, as well. To effectively combat fraud, it is crucial to understand the issues and their impact on your customers fully.
For example, according to the Identity Theft Resource Center (ITRC), the effects of identity theft can go on for years. Nearly one-third (32%) of the victims had money-related problems.
It has never been more crucial for businesses to be vigilant and aware of potential fraud threats, know best practices, and implement the best identity verification solutions. Businesses should follow these practices to keep customers secure and fight against digital identity fraud.
Types of Digital (Online) Fraud
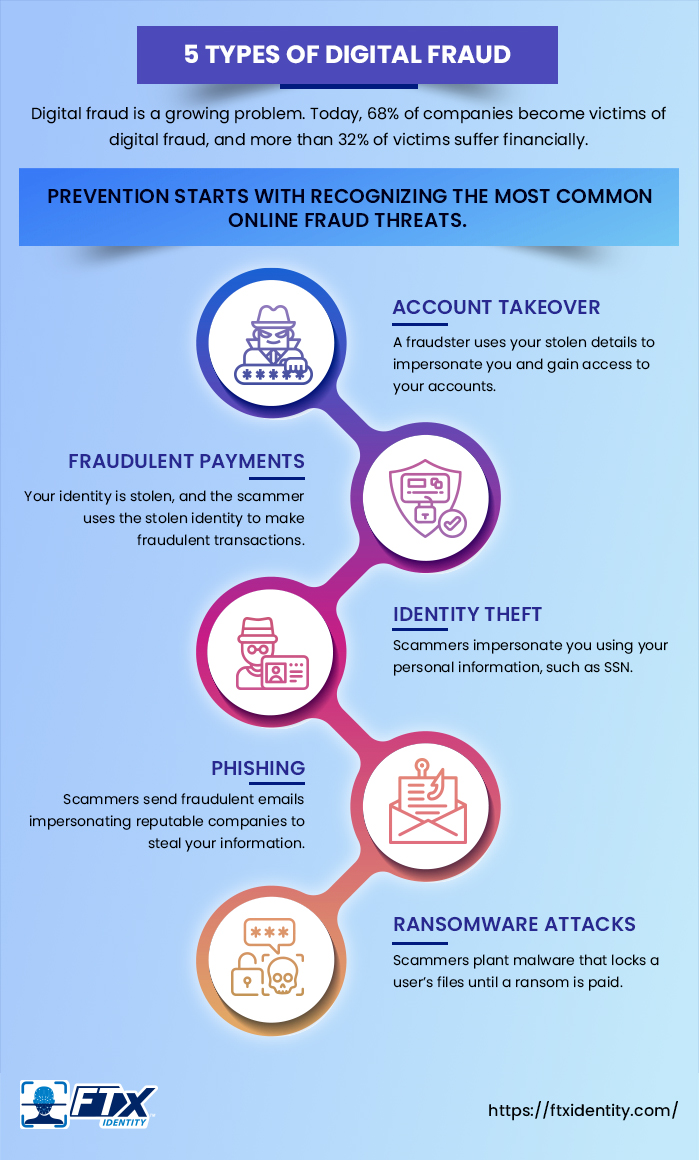
The last couple of years have seen a surprisingly high growth of online fraud. For instance, reported online theft cases grew from 3.2 million to 5.2 million between 2018 and 2022. Similarly, the FTC reported 805,000 cases in just the first three quarters of 2023.
These numbers are constantly increasing. The need for digital identity software has never been greater.
Step 1 in prevention is recognizing the most common online fraud threats. Here are five to watch for in 2024:
1. Account Takeover
Account takeover occurs when an unauthorized individual gains access to a user’s account. Once they gain access, scammers can impersonate you using your details, steal money, make unauthorized transactions, and misuse your card details.
Methods:
The scammers lure you into disclosing your credentials or personal information by various methods, such as:
- Stealing your passwords and breaching your security questions
- Making fake phone calls claiming to be bank executives
- Sending fake bank messages, for example, ‘Your account information is incomplete, please contact us to avoid account closure’
- Emailing fake website links that hack all the information once clicked or logged in
2. Fraudulent Payments
This refers to financial fraud, where scammers have made fraudulent financial transactions.
Statistics:
- Online payment fraud reached $41 million in 2022
- Nearly 65% of the organizations were victims of payment fraud in 2022
- A study conducted by Juniper Research predicts a global online payment fraud exceeding $343 billion between 2023 and 2027
Method:
Scammers can gain access to accounts and make fraudulent payments by:
- Using the stolen credit card information
- Issuing new credit cards and making transactions
- Issuing fake checks
- Making online fund transfers
3. Identity Theft
A type of online crime where a scammer tries to impersonate you by using your personal information, such as name, social security number, etc., for unauthorized acquisitions, such as financial gain.
Warning signs:
- Check for unauthorized purchases
- Scan your bills before making payments for any items you did not buy
- If you received a call confirming the purchase of a new credit card
- New logins in your social media apps from unknown locations (you can find them in settings)
- New loan accounts created on your account name
Methods of ID theft:
- Data breaches
- Weak passwords
- Scooping trash bins for account information
- Impersonating as a financial officer to gain account details
- Fake lottery winning, job placement forms, or online forms
- Rig the devices at ATMs
4. Phishing
Cybercriminals have used this old but highly effective (and still widely used) technique for ages, sending deceptive emails or messages impersonating reputable companies to obtain personal information.
Statistics:
- Anti-Phishing Working Group (APWG) recorded 4.7 million phishing attacks in 2022
- It was observed by the same group that there is a 150% growth per year in phishing attacks
- Financial institutes were the most targeted industry, with 27.7% of phishing attacks
Methods:
- Spear Phishing – You receive a malicious email. For example, a security alert emails, such as, ‘Your account has been compromised.’
- Email Phishing – You receive fake emails asking you to complete an action like a fake invoice scam, a message from the HR team to fill a job document, or a taxing department to click on a link to avoid tax.
- Vishing – Vishing is short for ‘Voice Phishing’ that involves defrauding people by pretending to be a person of high authority. For instance, a law enforcement officer asking for your personal details or a fraud investigator asking for account details.
- Link Manipulation – This type of phishing involves scammers sending viruses through links or retracting account information by sending wrong links.
5. Ransomware Attacks
Ransomware attacks are malicious malware that attack the user’s personal files and locks them out unless a ransom is paid. This type of attack generally targets influential individuals or big conglomerates. Once the ransom is paid, these cyber criminals give back access (but in most cases, they damage the files even after the ransom is paid).
How it works?
- Cybercriminals create malware software
- The malware infiltrates the victim’s system, further encrypting the files
- The criminals demand ransom in exchange for the decryption key
- Once the ransom is paid, they grant the victim access to all the files and data
2023 Ransomware Attacks:
- Cybercriminals launched a ransomware attack on the Los Angeles Unified School District (LAUSD), and when they refused to pay the ransom, the hackers released 500 GB of data on the dark web.
- The City of Dallas faced a ransomware attack in which nearly 26,000 people were affected, and many have already started reporting identity theft.
- The ransomware attack on MOVEit is still talk-of-the-town, with nearly 600 organizations and 40 million people affected.
What Is Fraud Detection and Prevention?
Fraud detection and prevention refers to strategies and technologies constantly fighting to identify and mitigate fraudulent activities. The most targeted industries are banking, finance and insurance, e-commerce, public or government companies, retail, etc. The key components of real-time fraud detection and prevention:
1. Monitoring and Analysis
2. Multi-Factor Authentication (MFA)
3. Identity Verification
4. Real-time Fraud Alerts
5. Machine Learning and AI
6. Transaction Monitoring
7. Employee Training and Awareness
8. Collaborative Efforts and Information Sharing
Digital Fraud Prevention Techniques (Strategies to Use)
Here are some of the most reliable digital fraud strategies:
1. Stop Relying on Passwords
Passwords are no longer necessary. It is now a matter of when corporations will stop using passwords in favor of emerging technology like biometrics, with many, if not most, businesses moving away from them soon.
Users find passwords annoying, and they need to be a more secure solution. Although they have always been used online, passwords have become misused.
For example, they are increasingly used as identification documents when signing contracts or conducting business. In this instance, a stolen password allows someone to sign on your behalf. Even one-time passwords (OTPs) used as a multi-factor authentication (MFA) component are susceptible to incidents like SIM swapping and scammers pressing victims for codes.
2. Use Two-Factor Authentication
Two-factor authentication (2FA) adds an extra security layer to businesses and is relatively easy to implement.
Here’s how it works: When users log in, they first enter their password. That’s step one. For step two, they need to provide another proof of identity. This could be a code sent to their phone or an app. So, even if someone steals the password, they can’t get in without the second factor.
Businesses can use 2FA to protect sensitive data like customer information or financial records. It’s easy to set up. Many online services offer 2FA as a feature. Just be sure to train your employees in how to use it. Remember, 2FA is not foolproof. But it makes it much harder for hackers to steal sensitive data. It’s a simple, effective way to boost your business’s security.
For more on authentication, see our guide Authentication vs Verification.
3. Transition to Biometrics
Biometric authentication boosts security for businesses. It uses unique features like fingerprints or facial recognition, which are nearly impossible to steal, unlike passwords.
Another advantage: Biometrics are user-friendly. They don’t need to be remembered or updated. This reduces the risk of data leaks and security breaches, and it also gets rid of password fatigue. Users often reuse or choose weak passwords. Biometrics doesn’t have this problem. They also work faster than passwords and make things more efficient.
However, using biometric authentication does have its challenges. These include privacy issues and the risk of physical theft. If biometric data is compromised, it’s hard to change. So, a balanced approach with multiple security layers is best.
4. Use Secure Networks
Secure and trusted networks are essential for businesses when conducting online transactions. Here’s why:
Secure networks encrypt data: The information sent and received is encrypted when businesses use secure networks. This makes it difficult for cybercriminals to intercept and misuse the data.
Trustworthy networks reduce risk: Trusted networks have security measures to protect against malware or phishing attacks. Using these networks minimizes the risk of such attacks.
Customer confidence: Customers want assurance that their sensitive information, like credit card details, is safe. Using secure networks for transactions boosts customer confidence and trust in the business.
Regulatory compliance: Many industries have regulations requiring secure networks for transactions. Compliance helps avoid penalties and maintains a business’s reputation.
In summary, using secure and trusted networks for online transactions is vital to a business’s cybersecurity strategy. It protects the company and its customers, enhancing trust and compliance with regulations.
5. Focus on Data Transparency
Data transparency is the first step in easing consumer adoption of biometrics. Companies must be transparent about the types of customer information they collect and how they plan to use it. Additionally, they must offer a way for individuals to express their permission to use that biometric and the option to change their minds at any time.
Consumers want to feel surer and more confident about biometrics used by the government, companies, AI, or friends. To establish trust, assisting customers and educating them about new regulations is crucial
For example, the AI Bill of Rights, which safeguards personal information and biometrics.
Consumers can feel secure committing their digital security to biometric-based authentication solutions with this knowledge and unambiguous communication from a reliable service provider. The decision to employ biometrics ultimately rests with the customer, who must be well-informed to make the best choice
6. Build Customer Trust
You must build trust with your customers as you transition to new processes. You are responsible for informing customers of what new platforms entail. Businesses must, after all, serve as the first line of defense in the fight against digital fraud.
Nowadays, the consumer employs unique and non-transferable values when using biometrics on mobile devices, eliminating the inconveniences of forgetting passwords, attempted fraud, and missing coverage.
If the person knows this, they can guarantee security and excellent user experience. Creating easy-to-use, safe, clear, and highly secure biometrics will encourage customers to use them instead of passwords.
To further improve customer security, businesses should educate customers on safeguarding their personal data and identity online.
Companies could share easy victories with their customers, such as securing your home network with strong passwords and encryption, turning off or locking your work computer when you’re not using it, and being cautious when clicking links in emails.
7. Educate Your Customers
Businesses must notify customers about fraud schemes that pose a threat and educate them about securing their identity and employing biometrics for added security. As an example, the use of voice calls by fraudsters to obtain information or persuade victims to give them access to their money is on the rise.
They pose as banks or governmental agencies while knowing just enough about the customer to convince them there is a problem with their account and trick them into disclosing account information, resulting in digital banking fraud.
Customers’ personal information is frequently used by fraudsters in account takeover (ATO) operations. They call customer service centers to take over the account and pose as the customer. However, in these situations, the customer could prevent this kind of attack if they had voice biometrics set up.
8. Real-Time Monitoring
Continuous monitoring helps businesses identify suspicious behavior and potential threats. It’s also commonly used for identity verification in fintech. It involves real-time system observation to detect anomalies and potential threats. For example, this is a powerful tactic to catch synthetic identity fraud. Here’s how it works:
- Businesses install monitoring systems to track activities across their networks.
- These systems continuously scan for unusual behavior, repeated verification failures, or suspicious patterns.
- If an anomaly is detected, alerts are triggered for immediate action.
- This allows businesses to respond to threats before they cause harm.
- This is one of the best ways to find and address threats quickly, and it’s widely used to monitor customer and employee data.
This is one of the best ways to find and address threats quickly, and it’s widely used to monitor customer and employee data.
How Does FTx Identity Help Prevent Online Fraud
It’s crucial to remember that fraudsters are constantly looking for new technology to adopt and use. When preparing their defenses and assisting customers with digital fraud protection, businesses must keep these things in mind. The best method to safeguard customers against fraud is to switch to a biometric-first strategy and inform them of its benefits.
Ready to fight digital fraud with FTx Identity? Get in touch with us today to set up a consultation and experience a demo. Looking for more info? See our latest 9 Identity Verification Methods for 2023.
