In 2021, the average data breach cost was $4.24 million per incident. The highest level in almost 20 years, according to a report by IBM and the Ponemon Institute. These facts highlight the necessity for financial service providers to have a proactive approach to safeguarding data.
Knowing the key differences between criminal identity theft vs identity fraud is particularly important for protecting consumers from these crimes.
Although often used interchangeably, fraud and theft are two distinct crimes with varying impacts on your consumers and business.
Here’s a short definition: Identity theft occurs when personal data is stolen. Theft becomes identity fraud when that stolen data is used to commit fraud.
Ultimately, businesses can best protect themselves by understanding the differences between theft and fraud and the techniques criminals use for each tactic. Once you know the difference, you’ll be best suited to stop digital fraud from happening.
What is Identity Theft?
Identity theft is when someone steals an individual’s personally identifiable information.
For example, a criminal might steal someone’s social security number to open new bank accounts in their name. Ultimately, stolen identity data is often sold online.
Identity theft causes serious harm to a victim’s financial reputation and credit score. Also, scammers can open bank accounts, credit cards, and loans in the victim’s name.
After stealing as much as possible, the criminal moves on to another breach before getting caught.
Recovering from the damage caused by identity theft can take years. That’s why businesses must protect individual’s private details.
What Constitutes Personal Identifying Information (PII)?
Personal Identifying Information (PII) includes various data elements that can be used to identify an individual uniquely. A few of the examples are:
- Social Security number
- Date of birth
- Home address
- Driver’s License
- Passport number
- Biometrics data (fingerprint, facial recognition, etc.)
- Bank and card details (bank account number, credit card number, etc.)
- Medical information
PII contains an individual’s sensitive data, and companies must handle PII with care. Ensure you don’t mishandle or expose the data and prevent unauthorized access of the same.
Common Identity Theft Methods Used to Steal PII
Identity theft techniques are advancing, and criminals often use technology to steal sensitive information. The most common tactics for committing identity theft include:
1. Database Attacks
Cybercriminals frequently target businesses that deal with sensitive and private data, such as financial institutions. Criminals may get around a company’s security measures and steal personal and financial credentials. This mainly happens if the security protocols are inadequate or contain gaps.
2. Card Skimming
Some criminals will connect a scanner that copies bank card information to ATMs. Additionally, these devices have a covert camera that can read pin codes, making it simple for them to obtain your information.
3. Credentials Purchased on the Dark Web
A cybercriminal can search the dark web to determine if someone sells certain personal information. They do this to steal accounts and make illegal transfers.
4. Phishing Schemes
Phishing schemes use fraudulent email to get access to personal information. Identity thieves pretend to be banks or credit providers and ask for passwords and account numbers.
Using the same security questions for your bank account and social media can result in financial identity theft. This can happen through social media phishing.
5. Public Network Interference
Since public Wi-Fi typically has weak security, hackers can use it to listen in on other connected devices. A scammer might be able to intercept and steal the entered credentials if someone conducts a banking transaction.
6. Malware Attacks
Once a link is clicked, malicious software will be installed via scripts or programs that criminals have created. The malicious software is capable of keylogging your passwords or engaging in more intrusive monitoring of your computer usage.
7. Wallet, Document, and Mail Theft
Physically stealing your personal documents gives a criminal access to your information in the most direct way possible. In addition to stealing mail, some could even rummage through dumpsters and trash cans to find someone’s information.
This tactic is commonly used to create synthetic identities for fraud.
8.Fraud with Deepfakes
Deepfake identity theft is becoming increasingly common. Criminals use AI-created fake photos to cheat and access secure image-based verification systems.
The Different Types of Identity Theft
Here are a few ways that scammers can steal your information:
1. Financial Identity Theft
Financial identity theft is the unauthorized access to an individual’s financial accounts or personal information to make fraudulent transactions. This may include stealing:
- Credit card information
- Bank account details
- Social security number
With the stolen data, scammers try to:
- Apply for heavy loans (where the victim ends up paying)
- Transfer money to their bank accounts
- Make unauthorized purchases through credit cards
- Issue new credit cards
Damage it causes:
- Impacts the credibility of the victim
- Affects their credit score
- Financial loss
- Emotional and mental strain
2. Medical Identity Theft
Medical ID theft occurs when someone uses another person’s personal information to obtain:
- Illegal medical services
- Prescription drugs
- File false medical claims
Damage it causes:
- Falsifying the victim’s medical records
- Leads to incorrect diagnosis
- Can receive inappropriate treatments based on the records
- Financial liability as it impacts health insurance and long medical bills
3. Tax Identity Theft
Tax identity theft involves using someone else’s personal information, such as Social Security numbers, to file fraudulent tax returns or claim tax refunds illegally.
4. Synthetic Identity Theft
Synthetic identity theft involves creating completely new identities that are fake by combining real and fabricated personal information.
Synthetic identity theft occurs when a synthetic identity comprises forged documents and is not connected to a real person.
An identity thief can use a valid social security number and fraudulent personally identifiable information to construct synthetic identities.
What is Identity Fraud?
Identity theft is the act of stealing personal information. On the other hand, identity fraud is using that information to commit fraud.
Cybercriminals can exploit your account. They can also create a new bank account or commit card fraud. Moreover, they can make fake IDs. Lastly, they can use false information to apply for or withdraw money.
Fraudsters can steal identities and create fake identities to use in fraudulent transactions.
Common Types of Identity Fraud
Once sensitive information has been stolen, criminals can use this data to commit identity fraud in numerous ways. Some of the most common strategies for committing identity fraud include:
1. Fake IDs
Criminals use an individual’s personal data to generate a fake ID. Often, fake IDs pass scans. In addition to reputational harm, a victim of identity theft may be held accountable for crimes they did not commit. Synthetic identities can be created using social security numbers that have been stolen.
2. First-Party Fraud
This happens when a customer intentionally defrauds a financial institution by taking out a credit line or loan without intending to pay it back.
3. Fraud on Credit Cards and Lines of Credit
A fraudster uses stolen personal information to start a new credit line or use all available credit on an existing one. Sometimes, fraudsters use a “Frankenstein” identity to pull a long con.
To do this, they create a phony credit card account and make payments over a long period to raise the credit score. They max out the account and never pay it back after obtaining a higher spending cap and unsecured loans from a financial institution.
4. Fraudulent Use of Government Benefits
Criminals may use a person’s personal information to apply for benefits from the government. Since the start of the pandemic, this has happened more frequently, costing taxpayers billions of dollars in theft.
5. Home Title Fraud
This happens when a fraudster takes control of a person’s property title. In addition to having access to financial and personal information, they assume ownership. Scammers can obtain sizable loans in the victim’s name by using the equity in their property as security.
6. Account Takeover
This occurs when an unauthorized person obtains full control of a person’s financial accounts. By altering the login information, they exclude the original user before stealing money and disclosing recorded data. Additionally, scammers might apply for phony ATM cards and take money repeatedly over time.
The Potential Impacts of Identity Fraud on Businesses and Financial Institutions
The potential impacts of identity fraud on businesses and financial institutions are significant and affect various aspects of operations. Here are some potential impacts:
a. Financial Loss
Unauthorized financial transactions, identity thefts, or illegal withdrawals can directly impact the revenue and monetary inflow. Many businesses that lost massive amounts must hire investigators and deploy fraud prevention measures, incurring additional expenses.
b. Reputational Damage
Identity fraud can damage the reputation of businesses and financial institutions, losing trust among customers, investors, and partners.
c. Operational Disruption
Identity fraud can cause significant disruptions to regular business operations, leading to order fulfillment delays and increased internal and external costs.
Additionally, identity fraud can negatively impact business efficiency, such as customer service, employee productivity, etc.
d. Legal and Regulatory Compliance
Identity fraud seriously threatens businesses and financial institutions, putting them at risk of legal and regulatory consequences. Companies must adhere to data protection laws, consumer protection regulations, and fraud prevention compliances.
Failure to comply with these regulations can result in legal implications, fines, license cancellation, or penalties.
Warning Signs of Identity Fraud
If you can catch them early, you can often contain the fallout of a breach of personal information. In particular, it’s helpful to be aware of these warning signs of identity theft:
1. Unexplained Withdrawals from Your Bank Account
If you notice transactions you don’t recognize or can’t explain, it is mostly because a scammer has accessed your bank account.
2. Missing Bills or Other Mail
Identity thieves change your mailing address linked to bank accounts to hide unauthorized charges so that you won’t notice them.
3. Merchants Refuse Your Checks
If merchants refuse your checks, it could be a sign that an identity thief is writing bad checks in your name.
4. Debt Collectors Call About Debts That Aren’t Yours
Receiving calls from debt collectors about dues you don’t recognize can signify identity theft. Thieves may have opened new accounts in your name and charged significant charges.
5. Unfamiliar Accounts or Charges on Your Credit Report
Regularly review your credit report for unfamiliar accounts or charges. Identity thieves often open new accounts or make charges on existing accounts.
6. Medical Providers Bill You for Services You Didn’t Use
If you receive bills for medical services you didn’t use, an identity thief may use your health insurance information to receive treatment.
What to do. If you suspect identity theft, immediately report it to your bank, credit card companies, and credit bureaus.
Change your passwords and PINs. File a report with your local police and the Federal Trade Commission. Monitor your accounts and credit reports closely for further suspicious activity.
Difference Between Synthetic Identity Fraud and Traditional Identity Fraud
| Parameters | Synthetic Identity Fraud | Traditional Identity Fraud |
|---|---|---|
| Definition | Creates fictitious identities by mixing real and fabricated personal information. | Uses someone else’s personal information without their consent. |
| How is it done? | Combines real and fake information to create entirely new identities. | Uses an individual’s stolen personal information (e.g., Bank account number, Social Security, driver’s license). |
| Impact on Credit Profiles | Builds credit profiles from scratch using a mix of real and fabricated information. | Directly damages the victims’ credit profiles by making unauthorized transactions and purchases. |
| Financial Impact | Businesses and financial institutions can come under scrutiny due to fraudulent account openings, defaults, etc. | In this case, people or individuals become victims through stolen IDs, unauthorized transactions, fraudulent loans, etc. |
Identity Theft vs Identity Fraud: A Comparative Approach
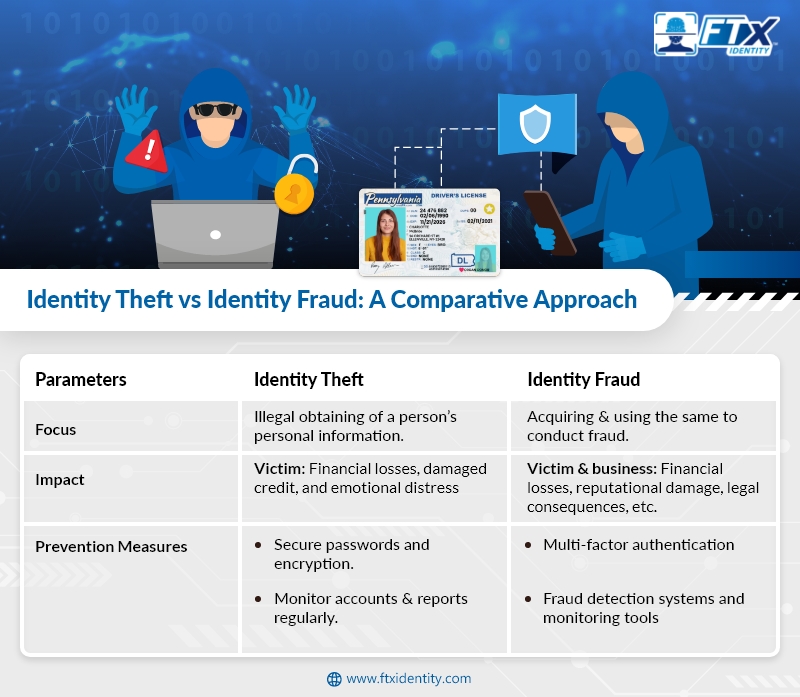
| Parameters | Identity Theft | Identity Fraud |
|---|---|---|
| Focus | Unauthorized acquisition of an individual’s personal information. | Unauthorized acquisition and use of personal information for fraudulent activities. |
| Impact | Can result in financial losses, damaged credit, and emotional distress for victims. | Can lead to financial losses, reputational damage, legal consequences, etc. for victims and affected businesses. |
| Prevention Measures |
|
|
Tips For Preventing Identity Theft
a. Secure online practices
b. Monitoring financial statements
c. Safeguarding personal information
Tips For Preventing Identity Fraud
a. Implementing strong authentication measures
b. Regularly checking credit reports
c. Being cautious with personal information sharing
The Demand for Identity Proofing
Organizations should be very concerned about theft and fraud protection. Criminals can easily commit fraud using outdated regulations and weak infrastructure in digital identity procedures.
An attack can jeopardize a business’s ability to maintain its finances and reputation, as well as the security of its customers. These results underline the significance of identity proofing.
Implementing multi-factor authentication and biometric IDV security systems will ensure only verified people can carry out transactions, access systems, and manage sensitive information.
Utilizing various strategies to stop fraud is essential because there are many ways to conduct it.
Ready to get started with FTx Identity? Get in touch with us today to schedule a consultation and demo to learn more about how we can serve as an identity guard. For security tips, see identity verification vs authentication.
