Knowledge-based authentication (KBA) has been around for decades, and it’s the primary way that websites verify identities. If you’ve been asked “your mother’s maiden name” by a website, this is an example of KBA authentication.
Although KBA can help to deter identity theft, it’s becoming increasingly insecure. This is due in a big part to data breaches and theft, making KBA information more accessible than ever.
Fortunately, for website operators, a number of KBA alternatives are emerging, each offering enhanced security for businesses and users.
Wondering what the best alternatives to knowledge-based authentication are? First, we’ll explain exactly what KBA is, why it needs to be updated, and cover the best alternatives for KBA on the market today.
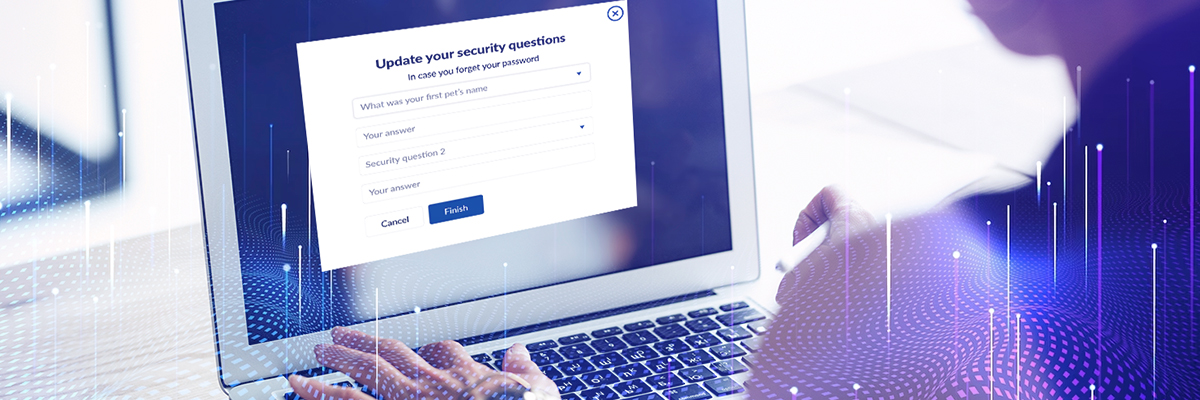
What Is KBA Identity Verification?
Knowledge-Based Authentication (KBA) is a way to prove who you are online.
Common examples include questions like, “What was the name of your first pet?” or “In which city were you born?” Examples include:
- Challenge Questions or Security Questions
- Shared Secrets
- Out-of-Wallet Questions
- Biographical Data Verification
- PIN-Based Verification
- One-Time Passwords (OTP)
- Social Media Verification
While KBA has seen widespread use for years, several challenges are rendering it less effective in today’s digital environment.
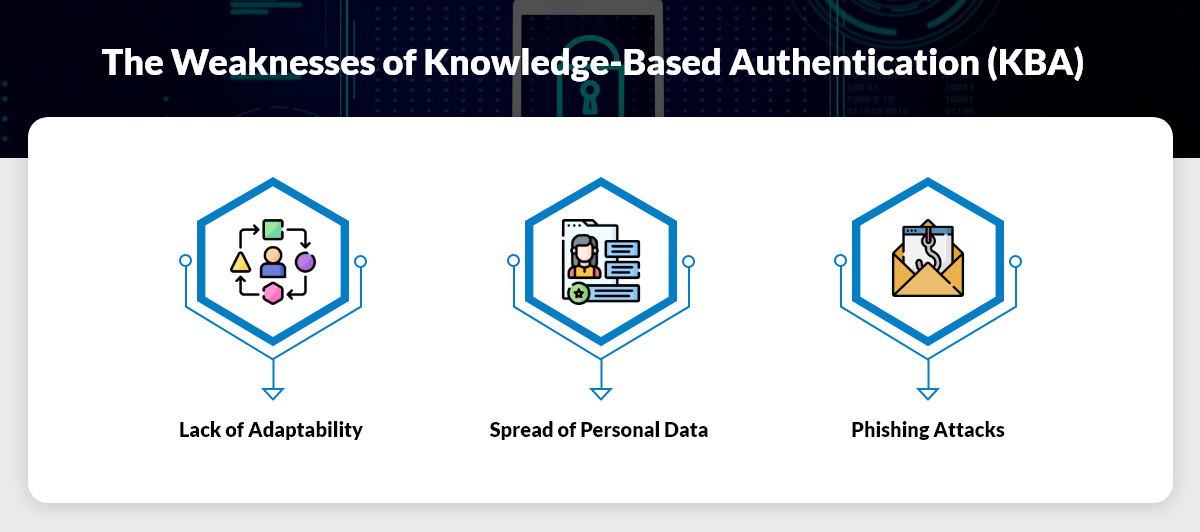
While KBA has seen widespread use for years, several challenges are rendering it less effective in today’s digital environment.
The Weaknesses of Knowledge-Based Authentication (KBA)
1. Spread of Personal Data
In the digital age, a wealth of personal information is available online, often in the public domain or on various social media platforms. This information includes details such as names of family members, birthdates, places of residence, and even answers to common KBA questions like “What was your first pet’s name?” or “Where did you go to high school?”
The sheer volume of personal data that can be accessed easily poses a significant challenge for KBA. Malicious actors can collect this data from various sources and use it to impersonate individuals, rendering KBA less effective. It’s as if the keys to your security are readily available to anyone with the means to search.
2. Phishing Attacks
In a phishing attack, cybercriminals impersonate trusted entities or individuals to deceive users into revealing sensitive information, including KBA answers. They craft convincing emails, messages, or websites that appear legitimate, tricking users into thinking they are interacting with a trusted source.
Victims unknowingly provide answers to KBA questions, assuming they are communicating with a friend, business or family member.
This social engineering tactic exploits the human element of trust, highlighting the vulnerability of KBA. It’s akin to someone pretending to be a friend or authority figure, gaining access to your secrets through deception.
3. Lack of Adaptability
KBA is static and unchanging by nature. The same set of questions and answers remains consistent over time, making it an inflexible method of authentication.
This lack of adaptability poses a severe limitation, particularly in a rapidly evolving threat landscape. Cybercriminals continually develop new techniques and tactics, rendering traditional KBA defenseless against emerging threats.
KBA cannot adjust to the changing nature of these challenges, making it increasingly susceptible to fraud. It’s akin to having a security system that remains static while the threat landscape evolves.
5 Best KBA Alternatives
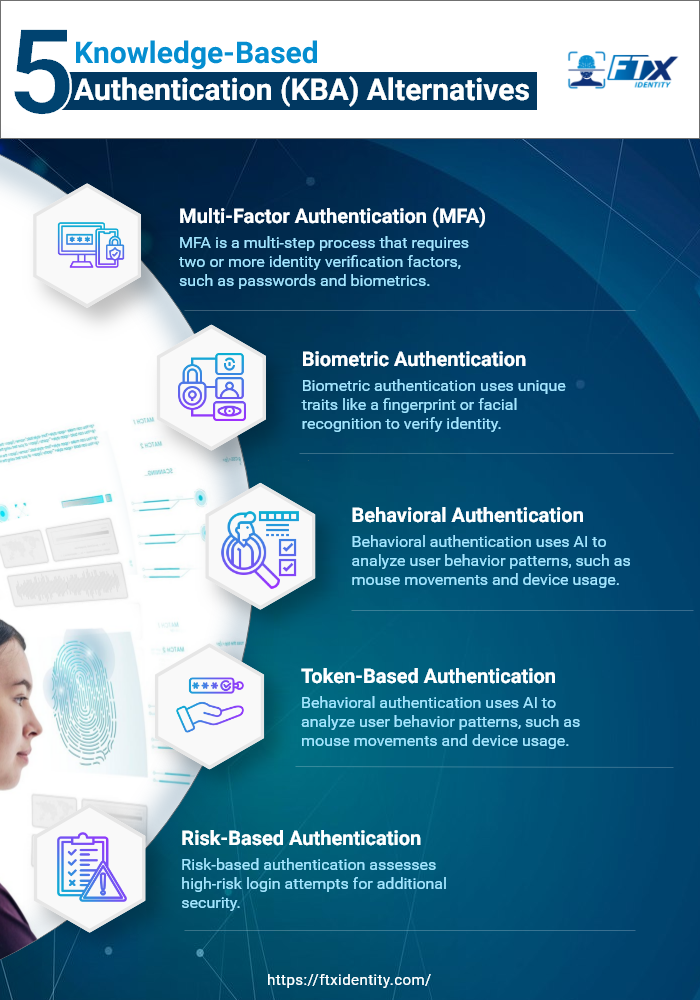
Given these issues, let’s explore the KBA replacement options that can enhance digital security:
1. Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) is a robust alternative to KBA that is gaining rapid adoption due to its enhanced security features.
MFA combines two or more independent factors for identity verification. This typically includes something the user knows (password), something the user has (a mobile device or smart card), and something the user is (biometrics like fingerprints or facial recognition).
By adding these additional layers of security, MFA significantly reduces the risk of unauthorized access.
2. Biometric Authentication
Biometric authentication is a cutting-edge alternative to KBA that leverages unique physical or behavioral traits for identity verification. Biometric data includes fingerprints, facial recognition, voice recognition, and iris scans.
Biometric ID verification is highly secure because it is incredibly challenging to replicate or spoof biometric data.
3. Behavioral Authentication
Behavioral authentication utilizes machine learning and artificial intelligence to analyze user behavior. It assesses patterns in how users interact with systems and applications, such as keystroke dynamics, mouse movements, and device usage.
If a user’s behavior deviates significantly from their typical patterns, it can trigger alerts for potential unauthorized access. Behavioral analytics systems are commonly used in AI verification platforms, for example.
4. Token-Based Authentication
Token-based authentication provides users with a physical or digital token that generates a one-time code or PIN for each login session. The dynamic code enhances security by continually changing, making it nearly impossible for attackers to predict or replicate. Common forms of token-based authentication include hardware tokens and Time-Based One-Time Passwords (TOTP) generated by mobile apps.
5. Risk-Based Authentication
Risk-based authentication is a dynamic alternative that evaluates the risk associated with a specific login attempt. Factors considered may include the user’s location, the device used, and recent activity.
The system may prompt for additional authentication if it deems the risk level to be high based on this assessment. This approach offers a proactive way to adapt to changing threats and provides robust security.

Enhanced Digital Security with KBA Alternatives
As the threat landscape for digital security continues to evolve, it’s crucial to move beyond traditional KBA verification. Alternatives, including MFA, biometric authentication, behavioral authentication, token-based authentication, and risk-based authentication, offer more robust and adaptable security solutions.
- Enhanced Security: KBA alternatives provide improved security compared to traditional KBA methods. Methods like biometrics and token-based systems are more resistant to fraud and identity theft, reducing the risk of unauthorized access.
- Reduced Vulnerability to Social Engineering: KBA alternatives are less susceptible to social engineering attacks because they do not rely on easily discoverable personal information. This enhances protection against phishing and other socially engineered attacks.
- Convenience and User Experience: KBA alternatives often offer a more convenient and user-friendly authentication process. Users appreciate the ease of biometric recognition or token-based systems, which can lead to higher user satisfaction.
- Lower Reset Costs: KBA alternatives typically reduce the need for costly password resets and customer support interactions. Biometrics and token-based systems decrease the reliance on manual account recovery processes, saving time and resources.
Wrapping Up
As the digital world advances, so do the threats to online security. The limitations and weaknesses of Knowledge-Based Authentication (KBA) are becoming increasingly evident, necessitating the exploration of more robust alternatives.
Multi-factor authentication, biometric authentication, behavioral authentication, token-based authentication, and risk-based authentication are emerging as promising KBA replacements. In an era where online security is paramount, these KBA alternatives provide a path towards enhanced protection and peace of mind.
And with innovative solutions like FTx Identity on the horizon, the future of digital security looks even more promising. FTx Identity, armed with cutting-edge technology and a commitment to safeguarding your online presence, stands poised to become a pivotal player in the ongoing quest to strengthen our digital defenses.
Contact us today to schedule a consultation and demo and get started!
