Biometric security has become an important tool in protecting against the growing risks of security breaches and identity theft. Biometric security is every business’s ally.
With the global biometric system market set to skyrocket to $84.5 billion by 2029, according to MarketsandMarkets, it’s clear that this technology is pushing the boundaries of security.
Face verification, a part of biometric security, is quickly becoming an essential tool for businesses to accurately and efficiently verify identities.
But what is face verification, and why is it becoming so popular?
This deep dive will explore how facial verification works, its benefits, and its different applications in various industries. By the end, you’ll have a clear understanding of how this technology can transform your business.
What Is Face Verification?

Face verification is a biometric method used to confirm an individual’s identity by analyzing and comparing their facial features against a stored template. Unlike facial recognition, which identifies who someone is from a database, face identification simply checks if the person is who they claim to be.
What Is Facial Recognition?
Facial recognition refers to a technology capable of identifying or verifying a person from a digital image or video frame. It works by analyzing unique facial features – such as the distance between the eyes, the shape of the cheekbones, or the contours of the jawline – and creating a mathematical representation, or “faceprint.” This faceprint is then compared against a database of known faces to find a match. While technology has seen amazing developments, its application and ethical implications often spark public debate, particularly concerning surveillance and large-scale identification without consent.
Key Differences: Facial Recognition vs. Face Verification
Often used interchangeably, facial recognition and face verification serve fundamentally different purposes and operate with distinct methodologies. Understanding this distinction is crucial for businesses aiming to implement secure and ethical identity solutions.
- Purpose: Facial recognition (also known as “face identification”) is about identifying an unknown individual by searching a large database of faces (a one-to-many match). It asks: “Who is this person?” Face verification, on the other hand, is about authenticating a claimed identity (a one-to-one match). It asks: “Is this person who they claim to be?”
- Matching Type: With facial recognition, an image of a person is compared against potentially millions of faces in a database to find a match. For face verification, a live capture or submitted image is compared against a single, pre-enrolled image of the person claiming that identity.

- Use Cases: Facial recognition is typically employed in law enforcement for suspect identification or in large-scale public surveillance. Face verification is used for secure logins, digital onboarding (like opening a bank account), face scan age verification for restricted goods, or confirming identity for online transactions.
- Accuracy Requirements: Both demand high accuracy, but face verification often has a stricter requirement for confirming a positive match to prevent fraud, while facial recognition might prioritize casting a wider net for potential leads.
- Data Privacy Concerns: This is where the distinction is most pronounced. Facial recognition raises significant privacy concerns due to its potential for mass surveillance and the creation of extensive personal databases without individual consent. Face verification, conversely, is generally consent-based and identity-specific.
How Does Face ID Verification Work?
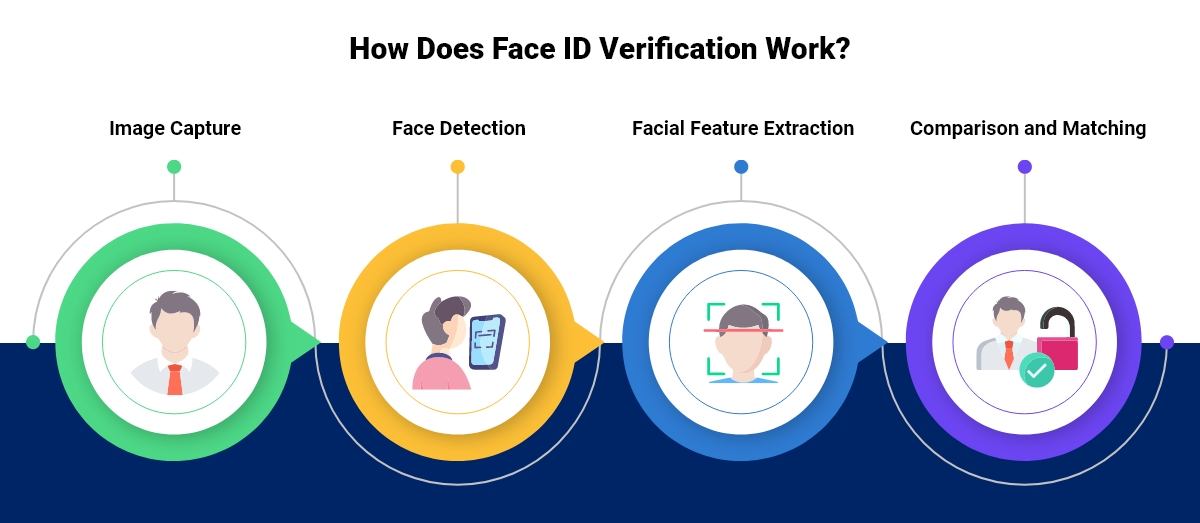
Face ID checks typically involve the following:
1. Image Capture
The process begins with capturing an image of the user’s face using a camera. This image serves as the input for the verification system.
2. Face Detection
Once the image is captured, the system detects the face within the image. This involves identifying the location and boundaries of the face to isolate it from the background.
3. Facial Feature Extraction
Next, the system extracts unique facial features such as the distance between the eyes, the shape of the nose, and the contour of the lips. These features are converted into a numerical representation called a template.
4. Comparison and Matching
The extracted template is compared to a stored template of the same person. If the match score is above a set threshold, the verification is successful; if not, it fails.
Top Benefits of Face Authentication
Face authentication comes with plenty of perks – here are some of the standout benefits:

- Security that Adapts: Face biometric verification leverages an individual’s truly unique biological blueprint, creating a formidable barrier against fraud and unauthorized access. It protects your operations in a way traditional methods simply can’t.
- Convenience & Efficiency: Face authentication keeps the user journeys simple and effective, transforming verification into a swift, intuitive glance.
- Facial Extraction: Face authentication eliminates friction and boosts satisfaction. When identity verification is this easy and fast, users don’t just tolerate it – they appreciate it, implementing deeper engagement and loyalty.
- Comparison & Matching: Face verification is about reducing human error and strengthening your defense against stubborn digital threats.
Use Cases of Face Authentication
Here are some of the industries and applications where face verification is already making a significant impact:
1. Online Banking
Performing face verification online provides an extra layer of security for online banking. Customers can log in to their accounts by simply looking at their device, ensuring secure and quick access.
Payments
Secure payments are made easier with face identification. It replaces traditional methods like PINs and passwords, reducing the risk of fraud.
Identity Verification
Banks and financial institutions use face authentication to comply with KYC regulations, ensuring that the person opening an account is who they claim to be.
2. Retail
In retail, face authentication revolutionizes the shopping experience, from swift checkouts to crucial age verification. It builds deeper customer loyalty while ensuring seamless, compliant transaction

Checkout Processes
Facial verification can speed up checkout processes. Customers can authorize payments using facial recognition, reducing wait times and enhancing the shopping experience.
Age Verification
Retailers selling age-restricted products can use face verification to automatically verify a customer’s age, ensuring compliance with legal requirements.
Loyalty Programs
Facial matching systems can personalize the customer experience by identifying loyal customers and offering them tailored rewards and promotions.
3. Travel and Hospitality
For travel and hospitality, face verification streamlines every touchpoint, from accelerating airport security to enabling contactless hotel check-ins. It delivers enhanced safety and a superior guest journey.
Airport Security
Airports around the world verify faces for security checks. This technology doesn’t just enhance security but also speeds up the boarding process.
Hotel Check-Ins
There’s no need to worry about long queues at hotel reception desks. Facial verification enables quick and contactless check-ins, improving the guest experience.
Access Control
Hotels and resorts use face verification to control access to restricted areas, ensuring that only authorized guests can enter.
4. Healthcare
In healthcare, face authentication ensures unparalleled patient safety and operational accuracy, from precise patient identification to secure drug dispensing. It safeguards sensitive data and critical access points.
Patient Identification
Face verification ensures that patients receive the correct treatment by accurately identifying them. This reduces the risk of medical errors.
Access Control
Hospitals use face-matching software to control access to sensitive areas, ensuring that only authorized personnel can enter.
Drug Dispensing
Automated dispensaries use face verification to ensure that prescribed medications are given to the right patient, minimizing the risk of drug-related errors.

5. Government and Law Enforcement
For government and law enforcement, face authentication enhances public safety and national security, from expediting border control to securing critical facilities. It provides robust tools for crime prevention and efficient operations.
Border Control
Face verification streamlines the immigration process by quickly verifying the identity of travelers, reducing wait times at border crossings.
Crime Prevention
Law enforcement agencies use face matching to identify suspects and prevent criminal activities. This technology is particularly useful in surveillance and investigation.
Access Control
Government buildings and facilities use face screening to control access, ensuring that only authorized individuals can enter sensitive areas.
Face Verification Technology Breakdown
The power behind modern face verification software lies in sophisticated technologies that differentiate real users from fraudsters, even the most cunning ones.
- 2D vs 3D Face Maps: Early systems relied on 2D images, easily fooled by photographs. Today, advanced 3D face verification creates a comprehensive, multi-dimensional map of a user’s face. This 3D data captures depth and contours, making it incredibly difficult to spoof and providing a far more robust layer of security than flat 2D images.
- Liveness Detection vs. Static Spoofing: One of the biggest threats to face verification security is spoofing – using a fake representation of a person’s face. Liveness detection is crucial here. It’s the technology’s ability to discern if the person presenting their face is a live, physical presence. This goes beyond static image analysis, detecting subtle movements, textures, and even pupil dilation to differentiate a real person from a photo, video, or 3D mask. This combats fake face verification attempts head-on.
- Role of AI/ML Models: Artificial Intelligence (AI) and Machine Learning (ML) models are trained on massive datasets of faces to identify unique patterns and variations. Deep learning algorithms enable the system to learn and adapt, making it increasingly accurate in recognizing faces across different angles, lighting conditions, and even over time as a person ages or changes appearance.
- Data Security and Privacy Compliance: Implementing face verification demands rigorous attention to face verification compliance and data security. Reputable solutions employ robust encryption for biometric data, secure storage protocols, and strict access controls. Compliance with global privacy regulations like the General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA) and industry-specific mandates (like KYC/ML for financial services) is non-negotiable. This ensures that while identities are verified, personal data remains protected and private.
Common Buyer Concerns & How They Can Be Solved
As businesses consider integrating face verification, legitimate concerns often arise. Here’s how an effective solution addresses them, building trust and demonstrating expertise, experience, authoritativeness, and trustworthiness (EEAT).

- How secure is face verification? You’re right to ask about face verification security. Top-tier systems utilize multi-layered security protocols, including 3D liveness detection, advanced encryption, and continuous monitoring to detect and prevent fraud attempts. This provides a highly secure method of identity authentication that significantly outperforms traditional methods.
- Can it be bypassed? The industry is dedicated to combating efforts to bypass face verification systems. Sophisticated face verification software employs cutting-edge liveness detection, anti-spoofing measures, and continuous updates to stay ahead of fraudulent techniques. This makes bypassing the system incredibly difficult for all but the most determined and technologically advanced attackers.
- Pricing transparency: Understanding face verification pricing is crucial for budget planning. Reputable providers offer clear, tiered pricing models based on usage volume, features, and specific business needs. This ensures you can scale your solution cost-effectively without hidden fees.
- Legal & regulatory compliance (KYC, AML, GDPR, COPPA): Navigating the alphabet soup of regulations can be daunting. A leading face verification solution will be built with compliance baked in. This includes adherence to KYC (Know Your Customer) and AML (Anti-Money Laundering) guidelines for financial sectors, GDPR for data protection in Europe, and the Children’s Online Privacy Protection Act (COPPA) for protecting children’s online privacy, ensuring your operations remain lawful and ethical.
Future Trends in Face Verification
Driven by advancements in AI and a growing demand for secure, user-friendly digital interactions, the future is bright for businesses that will stay up to date with the latest trends and utilize face verification solutions to give their customers peace of mind.
1. Emotion & Expression Recognition
Future systems will increasingly analyze nuanced facial expressions and emotions. This could enhance security by detecting duress or provide valuable insights into customer experience during online interactions, though it also opens new discussions around data use and ethics.
2. Edge AI & On-Device Processing
Moving away from cloud-dependent processing, edge AI means face verification computations happen directly on the user’s device (smartphone, laptop, etc.). This significantly boosts speed, reduces latency, and enhances privacy by minimizing data transfer, making real-time verification even more seamless and secure.
3. Decentralized Identity
Decentralized identity (DID) leverages blockchain technology to give individuals more control over their personal data. Face verification would play a crucial role here, acting as the biometric key that unlocks access to these self-sovereign digital identities, putting users firmly in charge of their verification process.
FTx Identity – Because Your Business Needs a Smart Choice
At FTx Identity, safeguarding identities is our top priority. Our advanced face verification software is designed to address the unique challenges of modern businesses, turning potential security risks into dependable opportunities for growth.
Our Features:
- Instant Verification with 99.99% Accuracy: Our powerful AI face verification solution delivers near-perfect accuracy, providing instant identity confirmation in seconds.
- Advanced 3D Liveness Detection: We leverage state-of-the-art 3D face verification and liveness detection to thwart sophisticated spoofing attempts, ensuring the person verifying is real and present.

- Flexible API + SDK Availability: Integrate our face verification Application Programming Interface (API) and Software Development Kit (SDK) seamlessly into your existing applications, websites, and platforms, ensuring smooth deployment.
- Intelligent Face Re-Verification Flows: Our system supports dynamic face ID re-verification flows, adding an extra layer of security for high-value transactions or suspicious activity without disrupting legitimate users.
- Universal Platform Compatibility: Our solution works on all platforms – whether your customers are on mobile, desktop, or interacting through your ecommerce site, the experience is consistent and secure.
Wrapping Up
The time for strong, reliable identity verification is now. Don’t let fraud, compliance complexity, or clunky user experiences hold your business back. Going with an all-inclusive solution is the right decision. Let FTx Identity be a part of that decision to protect your assets, delight your customers, and propel your growth.
