We live in an era of fractured digital identities, where control is a trickster and surveillance is a partner. But what if there was a fundamental shift? What if you held the keys to your digital self, deciding who sees what, when, and why?
Enter Decentralized Identity (DID) – not just another buzzword floating in the blockchain ether, but a paradigm shift in how we conceive and manage our digital existence. This isn’t about incremental improvements; it’s about a foundational reimagining of trust and ownership in the digital realm.
Over the next few scrolls, we’ll dissect this transformative concept. We’ll address the pivotal question: Is embracing decentralized identity on blockchain technology a worthwhile leap or just another fleeting trend? Join us as we demystify the potential and the practicalities of a future where you are truly sovereign over your digital identity.
Understanding Identity in the Digital World

Before we delve into the decentralized revolution, it’s crucial to establish a clear understanding of what constitutes “digital identity.” It extends far beyond the simple username and password combinations we use to log into countless platforms.
What is a digital identity? At its core, a digital identity is the collection of data that uniquely identifies an individual, organization, or device in the digital realm. This encompasses a broad spectrum of information, from basic profile details (name, email, date of birth) to more sensitive attributes like financial records, medical history, and online behavior. It’s the digital representation of our real-world selves and our interactions within the digital ecosystem.
Types of Digital Identity
Currently, we navigate a landscape dominated by two primary models, with a third, decentralized model emerging as a compelling alternative:
1. Centralized Identity: This is the most prevalent model, where a single authority (e.g., a social media platform, a bank, or a government agency) stores and manages user identities and their associated data. When you log into a service using your credentials for that specific platform, you’re interacting with a centralized identity system.
2. Federated Identity: This model allows users to use a single set of credentials managed by one trusted provider (like Google or Facebook) to access multiple independent services. While it offers some convenience, the underlying control over the core identity still rests with the federated identity provider.
3. Decentralized Identity: In stark contrast, this model empowers individuals with direct control over their identity data. Instead of relying on central authorities, users own and manage their identity credentials, storing them securely in their own digital wallets. Trust is established through cryptographic proofs and distributed ledger technologies like blockchain.
What Is Decentralized Identity?
Decentralized identity is the method of identifying and authenticating users without a centralized system.
Generally, your data (sometimes referred to as identifiers or attributes) are stored in a centralized location. When you create a bank account or create an online account on a company website, the data is stored in the bank and company, respectively. In this case, you don’t have control over your information because it is stored elsewhere.
So, how does decentralized identity control your data? Wait for it.
*Drumrolls*
It doesn’t. You control it. After all, it’s your data.
How Does Decentralized Identity Work?
Decentralized identity stores your data in a digital format that cannot be stolen, duplicated, or manipulated. Data storage is designed so that only you can control it.
When we talk about decentralized identity, some key players in the ecosystem play a significant role.
1. Issuer
2. Verifier
The issuer is your third-party organization that issues your records. For example, the government is issuing you your driver’s license.
The verifier is the third party you’re trying to contact (for example, the car agency that needs legitimate proof that you can drive the car or not).
Both the issuer and verifier are disengaged from your identity. In crypto’s world it’s called decoupling.

- Decentralized Existence: This architecture ensures the decoupling of your identity’s existence from both the issuing authority and the specific service you intend to use.
- Unbreachable Security: Thanks to robust cryptography, even in its digital form, your ID remains protected from duplication, theft, or any form of tampering.
- Self-Sovereign Identity: This facilitates a sharing mechanism that carefully decouples the necessary information from excessive disclosure to service providers.
There are two key technologies and ideas behind SSIs: blockchain, verifiable credentials, and decentralized identifiers.
Blockchain provides a secure, transparent, and immutable record of transactions.
- Verifiable Credentials (VCs) are digital equivalents of physical credentials. They are cryptographically secure and can be presented for verification.
- Decentralized Identifiers (DIDs) are unique identifiers that users create and control. They contain no personally identifiable information, enhancing privacy.
Therefore, with digital identity, an issuer (like a university or state licensing organization) would issue a VC to the holder. This credential would be signed with the issuer’s private key and recorded on the blockchain. Whenever the VC is presented, a verifier (e.g., an employer or law enforcement) can verify the authenticity by finding the document on the blockchain.
Quick Fact:
Despite the strong security level blockchains have gained as distributed ledgers, they are not completely impenetrable. Their security level is a direct outcome of their programming, meaning coding vulnerabilities could be a point of exploitation.
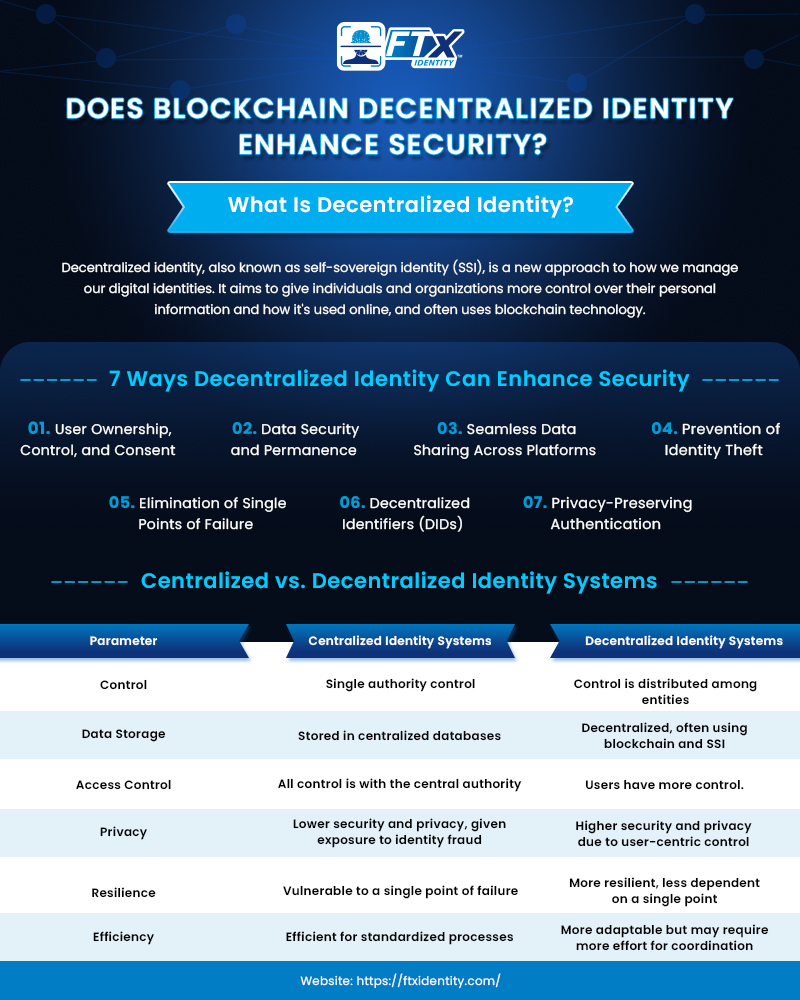
Decentralized Identity vs. Centralized Identity
When talking about how centralized identity systems are different from decentralized ID systems, here’s the best way to portray them:
| Feature | Decentralized Identity | Centralized Identity |
|---|---|---|
| Privacy | User controls what data is shared and with whom. | User data is mainly controlled by the central authority. |
| Security | Data is stored in users’ wallets; less prone to mass breaches. | Data is aggregated in central databases, a prime target for attacks. |
| Portability | Identity is portable across different platforms and services. | It is often tied to specific platforms. |
| Control | Users have direct ownership and control over their data. | Central authority dictates the management and use of identity data. |
| Revocability | Users can revoke access or control over specific credentials. | Revocation often depends on the central authority’s policies. |
Benefits of Decentralized Identity
The shift towards decentralized identity offers significant advantages for various stakeholders:
For Individuals:
- Total Data Ownership: You are the ultimate custodian of your digital identity. You decide what information to share, with whom, and for how long. This empowers you with greater control over your digital footprint.
- Less Friction in Authentication: Break free from usernames and passwords. Authenticate seamlessly with secure proofs via your digital wallet, making online interactions effortless.
- Reduced Identity Theft: By minimizing the storage of sensitive personal data in centralized databases, DID significantly reduces the attack surface for identity thieves. You control your data; it’s not a honeypot waiting to be compromised.

For Businesses:
- Faster Onboarding (KYC): Verifiable Credentials can streamline Know Your Customer (KYC) and Anti-Money Laundering (AML) processes. Once a user has been verified by a trusted authority, they can present that credential to other service providers, reducing redundant verification steps and accelerating onboarding.
- Reduced Fraud and Compliance Costs: Tamper-proof verifiable credentials enhance the reliability of identity information, helping to reduce fraud and the associated costs. Furthermore, the user-centric nature of DID can simplify compliance with data privacy regulations.
- Competitive Advantage in Web3 Ecosystem: As the Web3 ecosystem evolves, embracing decentralized identity will be crucial for interoperability and user experience within decentralized applications and services. Businesses that adopt DID early can position themselves as leaders in this emerging space.
For Governments and Institutions:
- Cross-Border Identity Verification: DID can facilitate secure and interoperable identity verification across national borders, streamlining processes like travel and international commerce.
- Data Sovereignty: DID aligns with principles of data sovereignty, allowing governments to empower their citizens with control over their digital identities while maintaining regulatory oversight.
- Streamlined Citizen Services: Decentralized identity can simplify access to government services, reduce bureaucratic hurdles, and enhance the security and privacy of citizen data.
Why Is Decentralized Identity Important for Business?
The importance of decentralized identity for businesses extends beyond mere efficiency gains.
In an increasingly privacy-conscious and digitally interconnected world, DID offers a pathway to building stronger trust with customers, reducing operational risks, and unlocking new opportunities within the burgeoning Web3 landscape. By empowering users with control over their data, businesses can foster greater transparency and build more ethical data practices.
Also, the interoperability facilitated by DID can lead to more seamless integrations with other services and platforms, fostering innovation and creating new business models. Businesses that ignore the potential of DID risk being left behind in the evolution of the digital economy.
Blockchain Technology and Decentralized Identity
Blockchain technology is a foundational pillar supporting the vision of decentralized identity, although, as mentioned earlier, it’s primarily used for anchoring trust rather than storing vast amounts of personal data.
Key Features of Blockchain Technology:
1. Security
Blockchain’s cryptographic hashing and distributed nature make it extremely difficult to tamper with or alter recorded data. Each block is linked to the previous one, creating a chain of immutable records secured by cryptographic algorithms.
2. Tamper-Resistance
Once data is recorded on a blockchain, it is virtually impossible to change it without the consensus of the network participants. This immutability ensures the integrity and trustworthiness of the information stored.
3. Decentralized
Blockchain networks are distributed across multiple computers (nodes), eliminating a single point of failure and making them highly resilient to censorship and downtime. No single entity controls the network.
4. Transparency
While the identities of participants in a public blockchain can be pseudonymous, the transactions and data recorded on the ledger are typically transparent and auditable by anyone on the network. This fosters trust and accountability.
5. Trustless
Blockchain enables trustless interactions, meaning participants can transact and exchange information without necessarily needing to trust each other directly. Trust is established by the underlying technology and the consensus mechanisms of the network.
Quick Fact:
What is Cryptography?
As IBM says, “Cryptography is the practice of developing and using coded algorithms to protect and obscure transmitted information so that it may only be read by those with the permission and ability to decrypt it.”
Its most common applications are:
-Cryptocurrencies
How Can Blockchain Technology Help Decentralized Identity Enhance Security?
Blockchain’s inherent security features directly contribute to the robustness of decentralized identity systems.
By anchoring DIDs and the public keys associated with them on a blockchain, a publicly verifiable and tamper-proof record is created. This allows relying parties to confidently verify the authenticity of a DID.
The cryptographic links within Verifiable Credentials (VCs), while the credential data itself might be stored off-chain, can be verified against the public key associated with the issuer’s DID, which is anchored on the blockchain. This ensures the integrity and provenance of the credential.
Furthermore, the decentralized nature of blockchain makes the DID infrastructure more resilient to attacks and single points of failure compared to traditional centralized identity registries.
Real-World Use Cases & Implementation Scenarios
The potential applications of decentralized identity span across various sectors:
- Healthcare: Patients can have secure and portable digital health records, granting access to authorized healthcare providers while maintaining control over their sensitive information. This facilitates seamless data sharing and improves patient care.
- Finance: Streamlined and reusable KYC processes can reduce onboarding times and costs for financial institutions while enhancing security and compliance. Users can present verified identity credentials across different financial services without repeatedly undergoing verification.
- Education: Educational institutions can issue tamper-proof digital diplomas and transcripts that individuals can easily share with employers or other institutions, eliminating the need for cumbersome verification processes.
- DAO Voting & Reputation Systems: DID can provide a secure and transparent mechanism for verifying the identity of participants in Decentralized Autonomous Organizations (DAOs), enabling fair and secure voting. It can also underpin decentralized reputation systems, where users build and control their online reputation.
- Supply Chain Identities for Products: DID can be used to create unique digital identities for products, enabling transparent tracking of their origin, provenance, and journey through the supply chain, enhancing accountability and combating counterfeiting.
Current Challenges and Limitations of Blockchain

Despite its immense potential, the widespread adoption of blockchain-based decentralized identity faces several challenges:
- UX and Adoption Curve: The technology underlying DID can be complex, and user-friendly interfaces and intuitive digital wallets are crucial for mainstream adoption. Educating users about the benefits and how to manage their decentralized identities is also essential.
- Scalability of Blockchain Networks: Some blockchain networks face scalability limitations, which could impact the performance and cost-effectiveness of large-scale DID deployments. Ongoing research and development are addressing these challenges.
- Interoperability Between DID Methods: Different blockchain platforms and DID methods are emerging, and ensuring interoperability between these systems is crucial for seamless cross-platform identity management. Standardization efforts are underway.
- Regulatory Uncertainties (GDPR, KYC, AML): The legal and regulatory landscape surrounding decentralized identity is still evolving. Clarity is needed on how existing regulations like the General Data Protection Regulation (GDPR), KYC, and AML apply to DID systems.
- ZKPs (Zero-Knowledge Proofs) for Privacy — Still Evolving: While promising for enhancing privacy within DID systems by allowing users to prove claims without revealing the underlying data, zero-knowledge proof technologies are still maturing and require further development for widespread implementation.
The Future of Identity: What’s Next?
The evolution of digital identity is far from over, and several exciting trends point towards the future of DID:
- Integration with AI and Smart Contracts: AI could play a role in assisting users with managing their digital identities and verifying credentials. Smart contracts could automate certain identity-related processes and enforce predefined rules for data sharing.
- Sybil Resistance and Reputation Scoring: DID can be leveraged to build more robust Sybil resistance mechanisms in decentralized systems, preventing malicious actors from creating multiple fake identities. Decentralized reputation scoring systems, linked to DIDs, could provide valuable context about the trustworthiness of individuals and entities.
- Cross-Chain Identity Protocols: Efforts are underway to develop cross-chain identity protocols that will enable seamless portability and interoperability of DIDs and verifiable credentials across different blockchain networks.
