It is becoming more challenging to create trust in the virtual world with the rise of cyber threats. Identity verification needs to be a main priority in protecting both customer privacy and business assets.
The stakes are high. It is estimated that cybercrimes will cause businesses to suffer devastating losses of approximately $10.5 trillion by 2025. That breaks down to an astonishing average of $20 million per minute.
Ignoring this reality is no longer an option.
Knowledge is the best way to avoid cyber crime. That’s why we’re exploring the top cybersecurity trends for 2024.
Keep reading for advice on navigating the ever-shifting threat landscape. We cover different types of cyberattacks and their profound economic impact, helping you build a proactive security strategy.
Top Cybersecurity Trends for 2025
The biggest trend in cybersecurity is the use of technology. Using advanced technology can help safeguard both your business and customers.
Here are the top trends you should be focusing on:
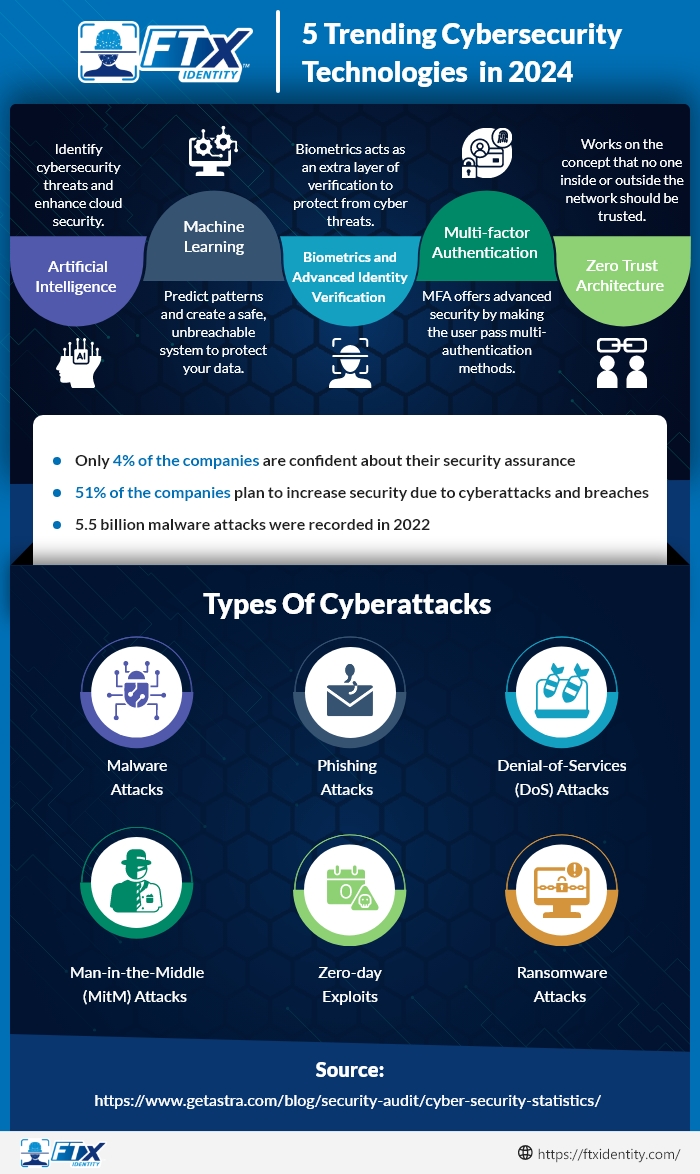
Artificial Intelligence and Machine Learning in Cybersecurity
Artificial intelligence (AI) has the potential to enhance cloud security by using advanced algorithms to quickly analyze large datasets and identify emerging threats. Additionally, AI can predict attack patterns, strengthening proactive defense measures.
Biometrics and Advanced Identity Verification
We are past the days of using passwords to access platforms. Biometrics like fingerprints and facial recognition are becoming one of the big cybersecurity trends.
Behavioral biometrics are also making their way into businesses. They can now analyze typing patterns, voice patterns, and even mouse movements to provide an extra layer of verification.
Multi-factor Authentication
Multi-factor authentication provides an extra layer of security by requiring users to provide multiple forms of authentication before accessing a platform. This extra security measure serves as a strong defense against cyberattacks since attackers would need to have multiple pieces of information to gain unauthorized access.
Zero Trust Architecture
Zero trust is built on the principle that nobody, whether they are inside or outside the network, should be considered trustworthy without undergoing a comprehensive identification process.
This is achieved through various technologies, such as multi-factor authentication and ongoing monitoring and logging.
What Is a Cyberattack?
A cyberattack is any digital crime in which a fraudster tries to deliberately gain unauthorized access to a computer system, network, or digital device. This includes obtaining sensitive information, such as personal and financial data.
Criminals use various tactics like malware attacks and social engineering scams to gain unauthorized entry into their desired systems.
Types of Cyberattacks
Cyberattacks come in various types, each using different methods to achieve specific goals.
Below are several examples:
Malware Attacks
Malicious software is called malware. It is considered an umbrella term for any form of malware. Examples include MITM attacks, phishing, and ransomware.
An attack causes damage or harm to a computer, server, or computer network to steal data or money. Malware can either infect multiple devices or stay dormant within a single device, harming only the device it occupies.
Phishing Attacks
“Phishing” involves attempting to gain access to personal information, like usernames, passwords, and bank account details, with the intention of either using or selling the acquired data.
The attacker uses a deceitful tactic, presenting themselves as a reputable source, to entice and deceive the victim.
An example would be sending an email to a victim saying that they won a gift card and to provide sensitive information to claim it.
Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks
A Denial of Service (DoS) attack occurs when a criminal floods a specific host or network with excessive traffic, rendering it unable to respond or causing it to crash. This results in the denial of access to legitimate users.
Similarly, a Distributed Denial of Service (DDoS) attack aims to exhaust the resources of a system. However, in a DDoS attack, the attacker controls many malware-infected host machines.
These attacks are named “denial of service” because they prevent the victim’s site from providing services to those seeking access to it.
Man-in-the-Middle (MitM) Attacks
An attacker places themselves between two parties who believe they are communicating directly, allowing the attacker to intercept and change the data being transmitted.
This poses a major risk to online security as it allows the attacker to obtain and manipulate sensitive information in real-time, such as login information and credit card details.
Zero-day Exploits
The technique involves exploiting a software vulnerability that is not yet known to the developer or security researchers.
Due to the recent discovery of the vulnerability, there are currently no immediate security measures in place. There was no time to address and fix the vulnerability.
These attacks pose a challenge in cybersecurity as they allow criminals to infiltrate networks without being detected.
Ransomware Attacks
These attacks involve holding a user’s or business’s files hostage and demanding money until payment is made. Once it is paid, the victim is provided with instructions on how to regain access to their files that have been encrypted.
During an attack, the ransomware is downloaded by the victim, either from a website or through an email attachment. This malware targets unaddressed vulnerabilities in the system that have been overlooked by both the manufacturer and the IT team.
The Economic Impact of Cyberattacks
The economy can experience major setbacks as cyberattacks become more common in the ever-changing digital landscape, including in the following ways:
Financial Losses
Cyberattacks can result in financial blows for businesses.
These attacks can jeopardize valuable assets such as credit card information and intellectual property, which can be traded illicitly. This results in major financial harm to both businesses and customers alike.
They can also result in a delay in regular business operations, which can lead to missing deadlines and losing relationships with customers.
Reputational Damage
The aftermath of a cyberattack can result in a loss of trust from customers, inventors, and partners, causing them to distance themselves from a business.
Additionally, when a cyberattack receives a lot of media coverage, a business may be seen as unsafe and untrustworthy, which can result in damaging its reputation.
Insurance and Recovery Costs
Businesses are growing more concerned than ever about the threat of cyberattacks. However, the cost of insurance policies has significantly increased due to the rising number and severity of these attacks.
Insurers are more selective in determining who and what qualifies for coverage due to the unpredictable nature of future risks.
Bringing in cyberattack experts to fix the damage caused can also be extremely costly, between containing the attack and collecting evidence.
The process of fixing compromised systems, recovering lost data, and repairing damaged infrastructure can lead to significant expenses for hardware, software, and specialist services.
Job Losses and Economic Slowdown
Cyberattacks can have severe consequences for businesses, including operational disruptions and financial losses. As a result, downsizing may be a possibility, leading to job losses for employees.
Attacks targeting critical infrastructure or major corporations can cause significant damage to the global supply chain. Disruptions in the supply chain can result in shortages and increased prices for goods and services.
Wrapping Up
It is clear that cybersecurity is an ever-evolving field, and staying informed about the latest trends and threats is crucial for individuals and organizations alike.
From the rise of cyberattacks through social engineering to the increased use of artificial intelligence in detecting and preventing breaches, there are numerous developments shaping the landscape of cybersecurity.
It is important to continue to educate ourselves and invest in cutting-edge technologies to effectively combat these ever-growing threats. As we navigate this digital age, it’s important to remember that our actions also play a role in maintaining our online safety.
To learn more about how FTx Identity can help your business, be sure to reach out to us today to schedule a consultation and check out a demo!
