Identity verification lies at the heart of secure digital transactions and regulatory compliance. However, verifying identities manually is not only slow; it’s also susceptible to human error, fraud, and inefficiencies.
Enter automated identity verification, a revolutionary approach powered by AI that offers real-time, accurate, and scalable solutions for businesses in today’s fast-paced digital landscape.
This blog post explores the ins and outs of automated identity verification, its critical role in today’s world, the technology behind it, and how solutions like FTx Identity help businesses stay ahead.
What Is Automated Identity Verification?
Automated identity verification is a process where advanced AI and machine learning technologies authenticate a person’s identity in real-time using digital methods like biometrics, liveness detection, and document validation. Automated verification outshines traditional methods by delivering fast, accurate, and scalable results while eliminating the risk of human error.
How Automated Identity Verification Works

An automated verification system replaces slow, manual checks with a streamlined, secure process.
It’s not a single action but a sequenced workflow where each step builds upon the last to confirm an individual’s identity with high assurance. This automated identity process transforms a physical document and a person’s biometrics into a verified, risk-assessed digital profile in seconds.
1. Data Capture
The process begins when a user submits their information. This typically involves using a smartphone or camera to capture an image of a government-issued ID (like a driver’s license or passport) and a live selfie or video.
This stage is about collecting high-quality, usable data for the automated ID system to analyze. A blurry image or poor lighting here can stall the entire process, so user guidance is key.
2. Authentication
Here, the system determines if the submitted ID document is genuine. Using AI-driven verification, it examines hundreds of security features—from holograms and micro-prints to font consistency and document structure.
It compares the document against known templates for that issuing authority. This step answers the question: “Is this a real, unaltered document or sophisticated forgery?”
3. Biometric Verification
This step proves that the person presenting the document is its legitimate holder.
The system uses the live selfie or video to perform a biometric verification. Advanced algorithms compare the facial features in the selfie against the photo on the ID document.
Crucially, liveness detection ensures the selfie is from a living, present person—not a photo, mask, or screen replay—which is a core automated identity verification method for preventing spoofing.
4. Data Extraction & Validation
Once the document and selfie are verified, the automated verification system extracts the printed data (name, date of birth, ID number, expiration date) from the document using optical character recognition (OCR). It then validates this data for logical consistency (e.g., does the calculated age match the date of birth? Is the document expired?) and can cross-check it against trusted third-party databases or watchlists in real-time.
5. Risk Analysis & Decisioning
In this final stage, all the collected data points—document authenticity, biometric match score, liveness confidence, and database checks—are fed into a rules-based engine or a machine learning model.
This engine performs a comprehensive risk analysis, weighing the evidence to render a final decision: approve, deny, or flag for manual review. This AI-driven verification step enables the automation of identity checks at scale, applying consistent, auditable policies to every single verification attempt.
Why Is Automated Identity Verification Important?
This process is indispensable in today’s digital landscape, where businesses and individuals face constant threats and evolving regulatory demands.
Here’s why it matters:
- Preventing Identity Theft and Fraud: Automated verification systems instantly validate user identities, making it harder for fraudsters to impersonate others.
- Streamlining Regulatory Compliance: Industries like banking and healthcare must adhere to compliance standards like KYC (know your customer) and AML (anti-money laundering), which automated identity verification simplifies.
- Improving Customer Experience: Effortless, real-time verification enhances user satisfaction and reduces onboarding friction for customers.
Types of Automated Identity Verification
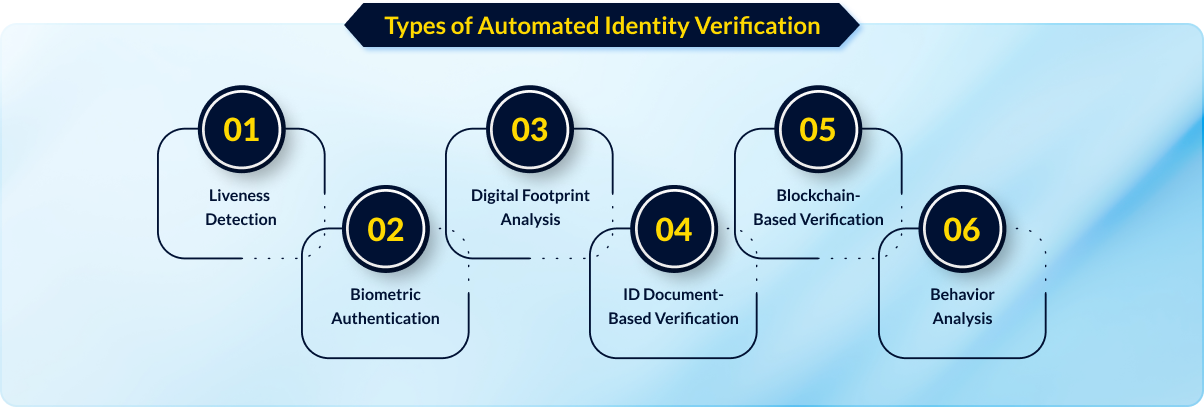
Over the years, identity verification has expanded with new and innovative options:
1. Liveness Detection
This method ensures a live person is interacting with the system, not a static image or video. Using AI, it detects facial movement and 3D depth features that confirm user presence.
2. Biometric Authentication
Biometric systems recognize unique physical traits like fingerprints, iris scans, or facial features. They provide unmatched security and are difficult to forge.
3. Digital Footprint Analysis
Analyzing online activity, including social media presence and digital behavior, verifies a user’s identity without needing extensive documentation.
4. ID Document-Based Verification
Users upload government-issued IDs (e.g., passports, driver’s licenses), which are validated using optical character recognition (OCR) and other technologies.
5. Blockchain-Based Verification
By leveraging blockchain, identities remain immutable and verifiable on decentralized networks, ensuring privacy and enhanced security.
6. Behavior Analysis
AI tracks user behavior patterns—such as typing speed or online habits—to verify authenticity and detect discrepancies indicative of fraud.
Automated Identity Verification vs. Manual Verification: Key Differences
Choosing how to verify a customer’s identity is a critical business decision. While manual checks rely on human scrutiny, automated identity verification leverages technology to create a faster, more secure, and scalable standard.
The gap between these two approaches isn’t minor; it represents the difference between a reactive, error-prone process and a proactive, strategic asset. The core advantages of an automated verification system are most clear when directly compared to traditional methods across five key business aspects.
| Aspect | Automated Identity Verification | Manual Verification |
|---|---|---|
| Speed | Processes occur in seconds. An automated ID system provides near-instantaneous results, enabling real-time onboarding and seamless transactions. | Can take minutes to days, involving physical document handling, emails, and waiting for staff availability, creating significant friction. |
| Accuracy | AI-driven verification reduces human error by consistently applying algorithms to check thousands of data points and security features without fatigue or bias. | Highly prone to human error. Fatigue, distraction, and varying levels of staff training lead to inconsistent and unreliable results. |
| Cost | Lower operational cost over time. Automating identity checks reduces the labor hours dedicated to manual review and scales effortlessly without proportional cost increases. | Higher long-term cost. Requires continuous investment in trained personnel and management and is inherently difficult and expensive to scale. |
| Fraud Detection | Superior at detecting sophisticated fraud. Uses automated identity verification methods like liveness detection, biometric matching, and forensic document analysis to spot forgeries humans miss. | Limited to visible, known fraud patterns. Relies on a clerk’s memory of security features, making it vulnerable to high-quality forgeries and synthetic IDs. |
| User Experience | Frictionless and modern. Users can verify from anywhere, at any time, using their smartphone. This seamless process is a competitive advantage in customer onboarding. | Cumbersome and inconvenient. Often requires in-person visits, photocopies, and waiting periods, leading to customer drop-off and frustration. |
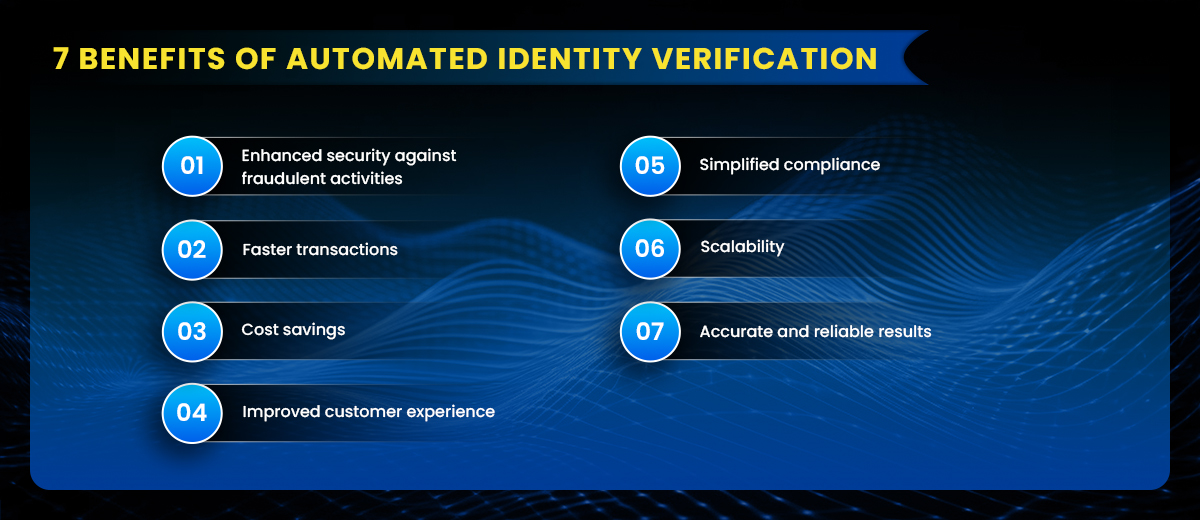
7 Benefits of Automated Identity Verification
Automated identity verification offers several benefits, including:
1. Enhanced Security Against Fraudulent Activities
AI-powered verification identifies and neutralizes potential fraud attempts, leveraging real-time alerts and anomaly detection.
2. Faster Transactions
Traditional manual verifications are time-consuming. Automated systems reduce processing time drastically, allowing for seamless transactions.
3. Cost Savings
By replacing manual processes, organizations reduce overhead costs while boosting productivity. Automation eliminates human errors, further driving savings.
4. Improved Customer Experience
Streamlined procedures ensure customers have smooth onboarding and transaction experiences, enhancing brand loyalty.
5. Simplified Compliance
Automated identity verification simplifies adhering to international compliance standards like KYC and AML, reducing the risk of administrative penalties.
6. Scalability
Advanced platforms easily handle high transaction volumes without compromising speed or security, making them ideal for growing businesses.
7. Accurate and Reliable Results
By leveraging AI-driven technology, these systems reduce errors caused by manual data entry and validation.

Common Use Cases of Automated Identity Verification
Automated identity verification is a versatile tool that can be applied across a wide range of industries, enhancing security and efficiency:
- Retail & Ecommerce: In this sector, automated verification is crucial for preventing fraud during online and in-store transactions. It ensures secure user onboarding, reducing the risk of identity theft and fraudulent activities. By verifying identities quickly and accurately, retailers can provide customers with a seamless shopping experience while protecting their sensitive information.
- Financial Services: Financial institutions, including banks, cryptocurrency exchanges, and lending platforms, rely on automated verification to comply with strict regulatory requirements. This process helps in verifying customer identities to prevent money laundering and other financial crimes, ensuring the integrity of financial transactions and safeguarding the institution’s reputation.
- Healthcare: In the healthcare industry, protecting sensitive medical records and ensuring only verified patients access services is crucial. Automated ID verification can prevent unauthorized access to medical data, thus maintaining patient privacy. It also streamlines patient check-ins, making the process more efficient and reducing wait times in healthcare facilities.
- Travel & Hospitality: Automated verification plays a significant role in streamlining check-ins for travelers, whether at airports or hotels. By using secure verification processes, these industries can reduce wait times and improve the customer experience. It ensures that travelers’ identities are accurately confirmed, enhancing security and efficiency.
- Government & Public Services: Automated verification is essential for ensuring secure access to government benefits and programs. It helps in authenticating identities to prevent fraud and unauthorized access, ensuring that only eligible individuals receive public services, benefits, and assistance. By improving security, it also enhances trust in government services.
Replace Manual Reviews with Instant, Accurate Decisions
Free your team from tedious checks and reduce operational costs. Get a personalized walkthrough of how our
system integrates to automate your entire verification workflow.
Security Layers Required for a Reliable Automated Identity Verification System
A trustworthy automated identity verification system is built like a fortress, not a single wall.
Its reliability stems from multiple, interdependent security layers that protect sensitive data, ensure system integrity, and maintain continuous vigilance.
Each layer addresses a specific vulnerability, creating a comprehensive defense that is critical for maintaining compliance and customer trust in an automated ID system.
1. Encryption & Data Protection
This is the fundamental, nonnegotiable first layer. It ensures that all sensitive data is unreadable if intercepted.
- In Transit: All data moving between the user’s device, your servers, and any third-party databases must be encrypted using strong protocols. This protects personal information throughout the automated ID verification process.
- At Rest: Stored data—whether in databases or backups—must be encrypted. This means even if storage is compromised, the data remains protected, a core tenet of a secure automated verification system.
2. Secure Data Storage Practices
How and where data is stored is just as important as encrypting it. This layer governs data lifecycle and access.
- Principles of Minimization & Segregation: Only the absolute necessary data is stored, and it is often kept in isolated, secure environments. For instance, biometric templates are stored separately from personally identifiable information (PII).
- Governed Access: Strict access controls and authentication are enforced so that only authorized systems and personnel can retrieve specific data elements, preventing internal breaches.
3. Continuous Monitoring & Threat Alerts
Security is not static. This layer provides active vigilance over the entire automated identity verification infrastructure.
Systems are monitored 24/7 for unusual patterns, such as a spike in verification attempts from a single location or repeated failed biometric verification attempts, which could indicate a coordinated attack.
Automated alerts are triggered for security teams to investigate potential threats in real-time, ensuring the automated identity check process cannot be easily exploited.
4. Audit Trails & Logging
For compliance and forensic analysis, every action within the system must be recorded. This layer creates an immutable history.
A detailed log is kept for every verification attempt, including timestamps, decision results, and which security rules were applied. This is crucial for regulatory audits and for investigating any disputed or fraudulent transactions.
This audit trail provides transparency and proof of due diligence, showing exactly how each AI-driven verification decision was reached.
5. Periodic Model Training & Updates
The AI-driven verification engines are living components. This final layer ensures they adapt to evolving threats.
The machine learning models used for document authentication and biometric analysis must be regularly retrained with new data on emerging fraud tactics, such as novel forgeries or deepfakes.
Regular updates to the automated identity verification methods and algorithms close security gaps and enhance accuracy, ensuring the system’s long-term reliability and effectiveness against novel attack vectors.
Challenges in Implementing Automated Identity Verification

Integrating identity verification automation brings numerous benefits, but it also presents several challenges that businesses must navigate.
These hurdles include:
- Balancing rigorous security with ease of use: Companies must ensure their systems are secure enough to prevent unauthorized access while remaining user-friendly to avoid frustrating legitimate users.
- Handling diverse ID formats across countries: With each country having its own unique identification documents, systems must be adaptable and able to recognize a wide range of formats and features.
- Ensuring data privacy and meeting global regulatory standards: Organizations must protect sensitive user information and comply with varying data protection laws worldwide, such as the General Data Protection Regulation (GDPR) in Europe or the California Consumer Privacy Act (CCPA) in California.
- Adapting to emerging fraud threats like deepfakes: As technology evolves, so do the tactics used by fraudsters. Systems need to be constantly updated to detect and counteract new threats, including sophisticated deepfake technologies.
- Integrating solutions with outdated legacy systems: Many organizations still rely on older technology infrastructures that can be difficult to update or replace, posing a challenge when integrating modern identity verification solutions.
How Automated Identity Verification Prevents Modern Fraud
Modern fraud is a moving target, evolving from crude forgeries to sophisticated digital attacks. Manual checks are defenseless against these threats.
A robust automated identity verification system is engineered specifically to detect and neutralize these advanced schemes in real-time. It acts as a multi-layered shield, where each defense mechanism targets a specific vulnerability in the fraudster’s playbook.
These defenses do not operate in isolation. They function as an integrated, intelligent network where the detection of one threat can inform the analysis of another, creating a powerful collective security posture.
1. Detecting Forged & Altered Documents
Fraudsters often start with fake IDs. AI-driven verification is trained to spot what the human eye cannot.
- Pixel-Perfect Analysis: Algorithms examine hundreds of data points—micro-prints, hologram consistency, font alignment, and spectral patterns—to detect even the most sophisticated forgeries.
- Template Matching: The system compares the submitted document against a global database of official templates, instantly flagging discrepancies in layout, security features, or data field placement that indicate a forged or altered document.
2. Stopping Bots & Synthetic Identities
Automated scripts and fabricated identities are used for large-scale attacks. Automated identity verification methods break this model.
- Liveness Challenges: Requires a real-time selfie or video with a prompted action (like a head turn), which bots cannot complete.
- Database Cross-Checks: Extracted identity data is checked against authoritative sources and watchlists to flag mismatches or identify synthetic identities pieced together from stolen data.
3. Preventing Account Takeover Attempts
When fraudsters steal login credentials, they still need to pass identity checks. Automated verification system protocols create a hard stop.
- Step-Up Authentication: Triggers a fresh biometric check for suspicious login activity (e.g., new device, high-value transaction).
- Behavioral Biometrics: Analyzes patterns in how a user interacts with their device during the verification, adding an invisible layer of continuous authentication that impostors cannot replicate.
4. Blocking Deepfake & Video Spoofing
Advanced fraud uses AI-generated faces and videos. The system fights fire with superior AI.
- Active Liveness Detection: Uses challenge-response tests that require natural micro-movements and 3D depth perception, which static deepfakes or 2D video replays cannot mimic.
- Passive Liveness Analysis: Scrutinizes hundreds of texture, lighting, and reflection cues in the selfie/video to detect signs of digital manipulation, effectively blocking deepfake attempts.
5. Identifying Risky Devices and IP Addresses
The “where” and “what” of a verification attempt provide critical risk context.
- Device Fingerprinting: Analyzes the hardware and software configuration of the device used. Repeated failures from the same device, or use of an emulator, raise immediate red flags.
- IP & Geolocation Intelligence: Cross-references the internet protocol (IP) address with known proxy servers, virtual private networks (VPNs), data centers, and high-risk geographic locations associated with fraud, adding a crucial layer of contextual risk analysis.
How FTx Identity Stands Out
FTx Identity leads the pack in offering comprehensive identity verification solutions that prioritize security and user experience.
AI-Driven Verification
Our machine learning algorithms provide advanced pattern recognition to accurately match and verify identities while reducing human errors.
Biometric Authentication
FTx Identity uses cutting-edge facial recognition with 3D liveness detection for robust security, combining document checks with biometrics for multi-factor authentication.
Advanced Document Verification
With features like OCR and automated MRZ (machine-readable zone) scanning, FTx Identity excels at document analysis, making it ideal for verifying passports and government-issued IDs.
Seamless API and SDK Integration
FTx Identity works across mobile, web, and desktop. APIs (application programming interfaces) and SDKs (software development kits) let developers connect and extend functionality securely.
Real-Time Data Extraction

By tapping into global public databases, our automated process ensures quick and accurate validation of ID details.
Proof of Verification
Tools like selfie authentication and detailed back-office reports provide solid proof of compliance and verification processes.
Why Choose FTx Identity?
FTx Identity offers an unparalleled solution by combining the latest technologies with a customer-first approach.
- Advanced Technology: Our platform is continuously updated to ensure that systems remain ahead of rapidly evolving security trends. This commitment to innovation means clients can trust that their data is protected using the most current and effective security measures available.
- Global Reach: FTx Identity supports a wide array of ID documents from over 180 countries, making it suitable for businesses operating on a global scale. It ensures compliance with a diverse range of international regulations, allowing businesses to expand their reach and operate confidently in multiple jurisdictions.
- Customer-Centric Features: We offer simplified user journeys and personalized workflows that are specifically tailored to meet the unique needs of different businesses. This focus on customization ensures that each client can streamline their operations efficiently and enhance their customer interactions.
Wrapping Up
Automated identity verification is no longer just a tool—it’s a strategic necessity in a digital age where trust and security are crucial. From reducing fraud to delivering seamless customer experiences, it offers businesses a competitive edge while ensuring compliance.
FTx Identity stands out as a comprehensive solution that integrates AI-driven precision, biometric capabilities, and real-time data extraction, providing businesses with the tools they need to thrive in a fast-changing technological landscape.
Stop Modern Fraud Before It Starts
See how our AI-powered verification instantly detects deepfakes, synthetic IDs, and forgeries that fool manual checks. Let us show you the real-time defense in action.
