ID authentication is crucial in ensuring the security of digital environments. It serves as a protective measure for business networks, allowing only authorized individuals to access valuable resources such as computer systems, networks, and websites. This is done by requiring users to provide unique information or data that only they possess, therefore enhancing the overall security framework.
But how exactly does ID authentication work? And what are the most common use cases of ID authentication in business?
Ultimately, most businesses already use some form of ID authentication. Basic ID verification solutions like passwords are widely used. However, ID authentication has vastly improved, and now, advanced authentication solutions exist that can best protect businesses from online fraud.
This guide explores the importance of ID authentication, including how it works and major reasons why businesses should adopt a suitable solution.
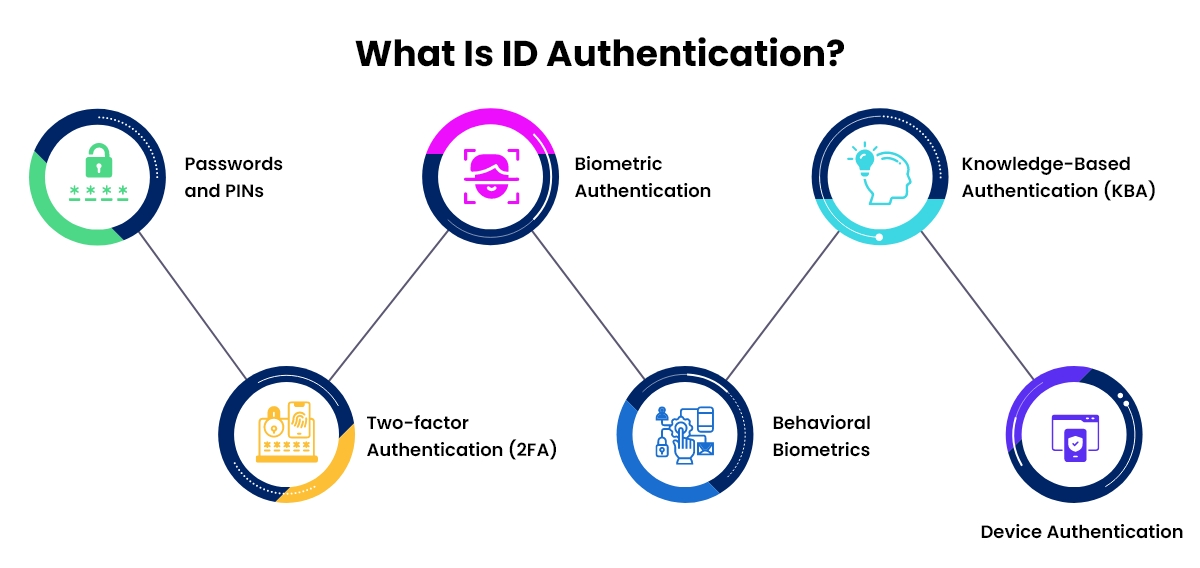
What Is ID Authentication?
Identity (ID) authentication is a process that determines whether users are who they say they are. These systems are used to secure access certain actions or services.
For example, you might need to use ID authentication to access a secure server or to make a credit card payment online.
The process involves the user entering credentials that are compared to saved data in the system to confirm their identity and provide the desired access.
The following are some common authentication methods:
- Passwords and PINs: These two methods are still commonly used for single-factor authentication by users. However, they are susceptible to problems such as weak passwords and simply put, they lack user friendliness and security.
- Two-factor authentication (2FA): By implementing this feature, an additional level of security is incorporated through the use of dual identification methods. These methods involve the input of a password along with a unique code that is sent to a designated mobile phone.
- Biometric authentication: This consists of utilizing the unique physical or behavioral characteristics of a user to confirm their identity. This type of authentication comprises fingerprint scanning, iris scanning, voice recognition, and facial recognition.
- Behavioral biometrics: The process includes studying user behavior patterns, such as keystroke dynamics, gait analysis, cognitive biometrics, and signature analysis.
- Knowledge-based authentication (KBA): This process centers on asking the user a series of questions that only they would know the answer to, such as previous addresses and the last four digits of their social security card.
- Device authentication: This is an important step in ensuring that only authorized devices can access specific resources or partake in specific actions. It serves as a protective measure against unauthorized access from unfamiliar or suspicious devices.

Why Businesses Need an ID Authentication Solution
It’s a necessity for businesses to incorporate an identity authentication solution, and there are a variety of reasons why:
- Enrich the customer experience: Incorporating a solution into your business can play a crucial role in verifying customer identities, thereby preventing fraudulent activities such as unauthorized purchases or the creation of fake accounts. This not only safeguards the interests of both customers and businesses but also upholds the reputation of the business as a trustworthy and secure entity.
- Keep fraud away from customers: Having a solution as part of a business can help them confirm the identities of their customers to prevent them from opening fraudulent accounts or making unauthorized purchases, protecting both the customers and the businesses and helping to preserve the business’s reputation as being reliable and safe.
- Cut back on costs: In addition to cutting down on fraudulent transactions and potential chargebacks, implementing a solution can effectively streamline businesses’ identity authentication procedures, resulting in significant savings in time, effort, and financial resources.
- Fulfill regulations: Many companies must comply with strict regulations and laws. Having an identity authentication solution won’t just protect a business but also prevent them from avoiding any fines associated with not following regulations.

ID Authentication Examples
The implementation of ID authentication has a wide range of applications, some of which include the following:
Online shopping
Affirm, a buy now, pay later service, has joined forces with Amazon. This collaboration enables Amazon shoppers to conveniently make installment payments for their purchases. As part of the finalizing process, users are requested to verify their phone number to ensure the legitimacy of the transaction. Subsequently, a unique 4-digit verification code is sent to the verified phone number, allowing users to proceed with their purchase securely.
Flights
Another important application of identity authentication is in airports. This process occurs when travelers present their ticket and driver’s license at the airport in order to check their bags and obtain their boarding pass.
TSA uses Credential Authentication Technology (CAT) to effectively detect fraudulent IDs and verify the identity and flight details of travelers. When a traveler is asked to provide their photo ID, a TSA officer will insert it into the CAT unit for scanning and analysis.
Use Cases of ID Authentication in Businesses
- Creating a new account: During the registration process for a new account with a company, users are frequently required to undergo an identity authentication process.
- Customer support procedures: Whenever a user communicates with someone based in customer support, the majority of the time they must confirm their identity to prevent any sensitive information being disclosed to the wrong person.
- A secure login and access: In most cases, when using an app or system, users are required to log in before proceeding. This involves providing a password, a verification code, or answering a specific question that only the user knows.
- Shopping and banking transactions: Identity authentication is a crucial requirement for transactions in the banking and online shopping industries, as shown in the Affirm example. Without it, such transactions may not be allowed to proceed.
Wrapping Up
To ensure authentication is run as securely as possible, it’s crucial to choose an ID authentication system that meets a business’s standards for safety and reliability. As technology advances, more robust and reliable ID authentication systems will be available, allowing businesses to stay ahead of security threats, protect their networks, and continue meeting the demands of digital transformation without compromising safety.
If you’re ready to take the leap with FTx Identity, be sure to reach out to us today to schedule a consultation and experience a demo!
