The task of verifying someone’s age is a complex but crucial one for many businesses in this digital world we live in. Whether it’s alcohol, vape sales, online gaming, or video streaming, ensuring users meet the minimum age requirement is needed for legal compliance and a safe online environment.
Business owners need effective and scalable age verification systems, and one method is device-based age verification solutions.
This blog post explores what age verification is on a device, its benefits and challenges, and how it compares to traditional methods.
What Are Device-Based Age Verification Solutions?
Device-based age verification solutions consist of using information or settings stored on a user’s device to confirm their age. Unlike traditional methods that require government-issued IDs or user-declared ages, this approach depends on the device’s data to make the process easier.
How It Differs from Traditional Methods
Traditional age verification methods usually require users to provide their birthdate or upload ID documents. Even though they’re effective, these methods can be inconvenient and invasive, often leading to poor user experience.
Device-based verification solutions can significantly improve user age authentication by simplifying the process. This entails eliminating the need for constant re-verification and reducing the collection of sensitive data.
Potential Benefits
The shift to device-based verification comes with several benefits, including the following:
Streamlined User Experience: Users can avoid repeated age verification across different platforms, making their online interactions more fluid.
Reduced Reliance on Sensitive Data Collection: By not storing birthdates and other sensitive information, businesses can enhance user privacy with an age verification system.
Scalable Solution for Online Platforms: Device-based verification solutions can easily be scaled across various services, making them ideal for businesses of all sizes.
Next, we will explore the practical steps involved in implementing device-based age verification.
How to Do Device-Based Age Verification

Carrying out device-based verification involves a few important steps, from pre-registration to access control, with some challenges along the way.
Pre-Registration Process
Users are asked to set their age during device setup or app installation. This age information may be linked to parental controls or verified through a trusted third-party service. This first step is important because it lays out the foundation for future age checks.
Access Control Mechanisms
Websites or apps can check with the device’s operating system (OS) for verification status once the user’s age is set. Ideally, the OS shares a verification token without revealing the user’s actual birthdate. This means maintaining privacy while ensuring compliance with age restrictions.
Potential Challenges
Despite its promising aspects, age verification on devices does have its challenges.
Accuracy of User-Reported Age: Users may not always report their age accurately during the device setup, which could lead to potential compliance issues.
Lack of Standardization: Different operating systems may handle age verification differently, resulting in complicated implementation across various devices.
Privacy Concerns: Sharing data between devices and platforms raises potential privacy issues that need careful management to guarantee the trust of users.
Advantages and Disadvantages of Device-Based Authentication and Verification
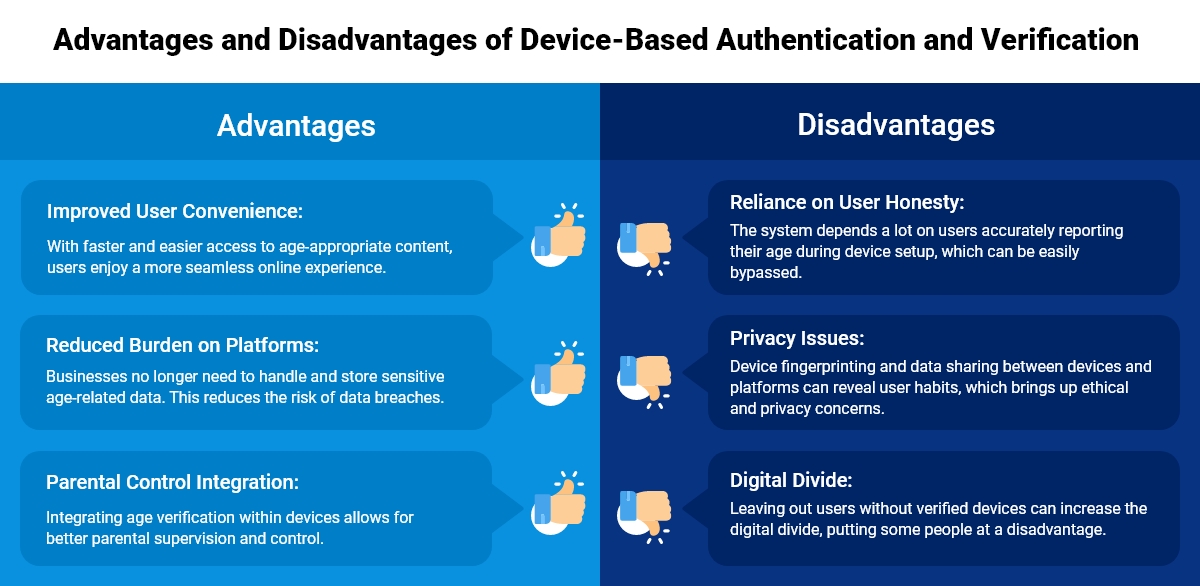
Every technology has its pros and cons, and device-based age verification solutions are no exception.
Advantages:
1. Enhanced Security: Device-based verification ensures that only authorized devices can access sensitive information. It reduces the chances of unauthorized access since the verification process is tied to a specific physical device (e.g., a smartphone or laptop).
2. Convenience for Users: It simplifies the authentication process for users, as they do not need to remember passwords or use additional hardware (e.g., hardware tokens). The device itself acts as a trusted factor for verification, making login faster and more seamless.
3. Reduced Risk of Phishing and Credential Theft: Since the authentication is tied to a physical device, it is more challenging for attackers to steal login credentials or perform phishing attacks. The attacker would need physical access to the specific device to bypass the authentication, which is typically more difficult than stealing passwords.
Disadvantages:
1. Device Dependency: If the user loses or forgets the device used for verification, they may be locked out of their account or system. This could be problematic if the user doesn’t have a backup method for recovery, such as a secondary authentication factor or backup code.
2. Privacy Concerns: ID verification devices often require tracking or storing information about the user’s device, which could raise privacy concerns. Some users may not feel comfortable having their device linked to their identity or actions, especially with increased surveillance or data breaches.
3. Vulnerability to Device Theft or Compromise: If a device is stolen or compromised (e.g., through malware or physical tampering), the security of the authentication system could be at risk. In this case, the attacker could bypass the verification process, especially if the device does not have strong encryption or other protective measures.
Overcome ID authentication challenges with a digital age verification solution!
What’s the Current State of a Device-Based Age Verification System?
Age verification on devices is still in its early stages, with few real-world applications. Important technical and regulatory challenges remain.
Limited Real-World Implementation
Currently, device-based age verification systems have seen limited adoption due to technical and regulatory challenges. Despite this, though, technology is continuously evolving, and several pilot projects are already exploring its potential.
Ongoing Debate
There is an ongoing debate about the effectiveness of device-based age verification technology and the associated privacy risks. Some experts praise its potential to enhance user convenience and security, while others warn about privacy risks from widespread data sharing.
Focus on Parental Controls
Most current implementations integrate ID verification devices with parental control features and content filtering systems. This helps protect minors online, but broader applications are still being developed.
Moving forward, the future of device-based verification solutions looks promising due to the efforts of various stakeholders.
Core Technologies Behind Device-Based Verification
Device-based age verification relies on a layered technology stack rather than a single signal. Each component contributes context, confidence, and fraud resistance to the overall age verification process. When combined correctly, these technologies allow businesses to perform accurate online age verification checks without interrupting the user experience.
Device Fingerprinting
Device fingerprinting analyzes a combination of hardware and software attributes such as operating system version, browser configuration, screen resolution, and installed fonts. Together, these attributes form a persistent but privacy-aware identifier that helps distinguish one device from another.
In device age verification, fingerprinting allows platforms to recognize repeat devices and identify anomalies that may indicate account sharing or manipulation. While it does not directly confirm age, it strengthens the reliability of the overall age verification system by anchoring identity to a consistent device profile.
Behavioral Biometrics
Behavioral biometrics focuses on how a user interacts with their device rather than what they submit. Typing speed, touch pressure, swipe patterns, and navigation behavior are analyzed in real time to assess whether interactions match expected human behavior.
This layer is particularly valuable in digital age verification because minors attempting to bypass controls often behave differently than legitimate adult users. Behavioral analysis adds a passive verification layer that operates silently during age verification checks.

Carrier-Based Verification
Carrier-based verification leverages mobile network data to confirm device ownership and subscriber attributes. Since telecom carriers already verify age at account creation in many regions, this signal can support how to verify age on a device without requiring repeated document uploads.
In online age verification systems, carrier signals help validate whether a device is linked to a verified adult subscriber, strengthening trust while minimizing friction.
AI and Machine Learning Risk Engines
AI-driven risk engines evaluate hundreds of signals simultaneously to assess the likelihood of fraud or misrepresentation. These engines adapt over time, learning from new bypass attempts, emerging fraud patterns, and behavioral shifts.
In modern age verification technology, machine learning allows businesses to move from static, rule-based checks to adaptive decision-making. This is essential for maintaining accuracy as fraud tactics evolve.
Cryptographic Tokens and Digital Identity Wallets
Cryptographic tokens allow age verification results to be stored securely and reused without repeatedly exposing personal data. Once a user completes a verified age verification process, the result can be referenced through a token rather than rerunning checks.
Digital identity wallets extend this concept by allowing users to control when and where age attributes are shared. This approach supports privacy-focused device verification while meeting regulatory requirements.
The Future of Device-Based Verification
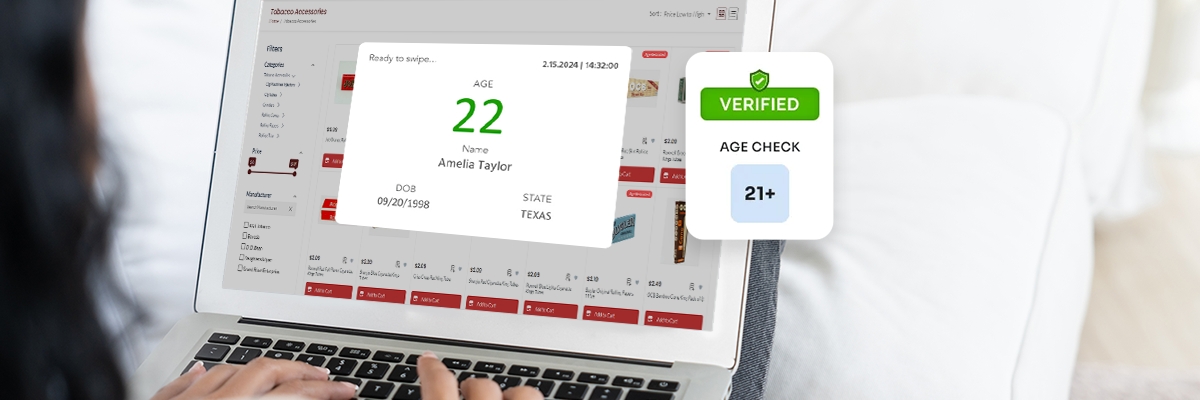
For device-based verification solutions to become common, device makers, online platforms, and regulators need to work together.
Potential Collaborations
Companies could work together to develop secure, privacy-preserving verification methods.
This could involve leveraging advanced encryption technologies and decentralized verification processes, ensuring that user data is protected at all stages. Such collaborations would not only enhance security but also ensure that the age verification technology benefits both users and businesses by providing a seamless and trustworthy verification experience.
Balanced Approach
The future will likely involve balancing user convenience with responsible online experiences. This means creating age verification systems that are easy to use but strong enough to prevent misuse.
Effective ID verification can allow access to appropriate content while protecting vulnerable users from harmful material, ensuring that online platforms remain safe and trustworthy for all age groups.
Continuous improvements and updates to age verification systems will be crucial to maintain this balance as technology and user expectations evolve.
Device-Based Age Verification for Key Industries
Different industries face different risks when verifying age online. Device-based age verification adapts well across sectors because it scales without adding unnecessary friction.
Retail and Ecommerce
Online retailers selling age-restricted products rely on device age verification to ensure compliance without disrupting checkout flow. By validating devices and behavior before purchase completion, retailers reduce failed deliveries and regulatory exposure.
In high-volume environments, digital age verification helps balance compliance with conversion, especially for repeat customers.
Online Gaming and Gambling
Gaming and gambling platforms face constant attempts by minors to bypass age controls. Device verification helps detect shared devices, repeated signups, and emulator usage that often signal underage access.
By combining behavioral analysis with device age verification, platforms can block risky sessions before gameplay begins.
Fintech and Banking
Financial platforms must comply with strict identity and age verification checks. Device signals add an extra layer of assurance by detecting account takeovers, synthetic identities, and unusual access patterns.
In regulated environments, device verification supports stronger onboarding and ongoing risk monitoring.
Ride Sharing and Mobility Services
Ride-sharing platforms use age verification systems to ensure riders and drivers meet legal age requirements. Device-based checks help identify shared accounts and repeated misuse of a single phone.
This approach allows continuous verification beyond initial signup.
Smart Vending Machines
Smart vending machines selling restricted products rely heavily on device age verification tools. Since there is no human oversight, devices act as the gatekeeper for age checks.
By validating the user device before dispensing products, these systems reduce misuse while maintaining fast transactions.
Social Media and Live Streaming Platforms
Social platforms increasingly face scrutiny around protecting minors. Device-based age verification helps identify repeat attempts to create underage accounts and detect manipulation through VPNs or emulators.
Rather than relying only on self-declared age, platforms can apply ongoing device-level checks.
Fraud Threats in Device-Based Age Verification
As adoption grows, fraud attempts become more sophisticated. Understanding these risks is critical to building a resilient age verification system.
Device Cloning
Fraudsters replicate device fingerprints to impersonate verified users. This undermines basic device age verification unless additional signals are layered in.
Advanced systems detect inconsistencies across sessions to flag cloned devices.
Rooted or Jailbroken Devices
Modified devices allow users to bypass operating system protections. These devices are often used to manipulate apps and age verification checks.
VPN and Proxy Masking
Virtual private networks (VPNs) and proxies hide a user’s location and network details, making it difficult to verify device authenticity. These tools are often used by underage users to bypass regional restrictions.
Robust device verification systems can detect unusual network patterns and block high-risk traffic, helping ensure that only legitimate users gain access.
Device Emulators
Emulators simulate mobile devices on desktop systems. They are frequently used to automate account creation and bypass age verification processes.
Behavioral and hardware-level checks help identify emulator activity.
SIM Swapping
Subscriber identity module (SIM) swapping allows fraudsters to take control of phone numbers associated with verified accounts. This can undermine carrier-based age verification if not monitored.
Continuous device behavior analysis helps detect sudden ownership changes.
Shared Device Abuse
Families often share devices, which can lead to minors accessing adult accounts. Device age verification must account for this risk without penalizing legitimate users.
Behavioral differences often reveal shared device misuse.
Bypass Attempts by Minors
Minors experiment with repeated signups, fake credentials, and borrowed devices. Device verification helps identify patterns that individual checks might miss.
This is where layered age verification technology becomes critical.

Best Practices for Businesses Adopting Device-Based Age Verification
Implementing device age verification successfully requires thoughtful design, not blind reliance on technology.
Combine Device Signals with Additional Proof
Device verification works best when combined with document checks, biometric confirmation, or trusted third-party signals. No single method should stand alone in a mature age verification system.
Layering reduces both false positives and compliance risk.
Prioritize Privacy and Transparency
Users should understand what data is collected and why. Clear communication builds trust and supports regulatory compliance.
Privacy-respectful age verification tools are more likely to gain user acceptance.
Educate Users on How the System Works
When users understand how age verification checks protect them, resistance drops. Transparency reduces support friction and improves completion rates.
Education is especially important for repeat verification scenarios.
Use Real-Time Fraud Intelligence
Fraud patterns change quickly. Systems must adapt in real time to emerging threats.
Live risk scoring strengthens online age verification systems against new bypass techniques.
Avoid Overreliance on Device Data Alone
Device verification provides context, not certainty. Overreliance can lead to blind spots, especially in shared device environments.
Balanced systems combine multiple verification methods.
Keep Up with Regulatory Updates
Age verification regulations evolve rapidly across regions. Businesses must regularly review compliance requirements and adjust workflows accordingly.
Staying proactive protects both users and brand reputation.
An Alternative Approach: Online ID Verification
While device-based verification solutions hold promise, other methods, like online ID verification, remain crucial.
For example: FTx Identity provides a strong alternative by offering a more comprehensive age verification technology.
Comparing Device-Based Verification to FTx Identity
Reliability: FTx Identity uses official government-issued IDs for verification, reducing the risk of fraud compared to device-based methods.
Security: By storing consumer information in a cloud-based, secure digital vault, we ensure data security and confidentiality. The data is encrypted and only accessible to the end user.
Compliance: FTx Identity meets strict regulatory requirements, providing peace of mind for businesses.
Until device-based verification solutions is fully reliable, online ID verification, including solutions like FTx Identity, remains the most secure and compliant method for verifying user age.
Wrapping Up
Age verification on a device offers a promising alternative to traditional methods but comes with significant challenges. Implementing this technology requires careful consideration of privacy, accuracy, and ethical concerns. While device-based verification methods have potential, online ID verification remains the most reliable and immediate solution for businesses.
For business owners looking to implement an effective age verification system, it’s crucial to stay informed about new technologies and regulatory changes. This ensures your platform provides a safe and compliant environment for all users.
Discover Smarter Age Verification Solutions for Your Business
Ensure convenience and compliance with cutting-edge verification technology.
Get a demo today and see how our solutions can transform your platform!