No matter how secure your website’s verification system is, criminals and underage visitors will find ways to get around it. In fact, the methods used to bypass age verification online continue to get more and more sophisticated.
What can your business do to protect itself?
Preventing users from bypassing your age verification system is now more possible than ever. Advanced AI-based verification tools, for example, make it more difficult for users to pass with fraudulent IDs, and next-generation authentication procedures also help to keep the wrong users out.
Ultimately, the best prevention starts with awareness. Learn the most common methods that are used to bypass age verification, and then reinforce your defense to protect your platform.

Understanding the Challenge: How People Bypass Age Verification
Almost all these methods use a similar strategy. They disguise the user’s identity and make it difficult for the platform to verify the user.
Many platforms also suffer from age-gating protocols that are easy to bypass. Here’s a look at the most common ways users get around age verification:
1. Using Fake Information
A common tactic for bypassing age verification online is entering false details during registration. This lets minors create accounts with fabricated birthdates that fulfill age requirements, allowing them access to restricted content. To combat this, businesses can introduce verification steps that cross-check user-provided data against external databases, enhancing verification accuracy.
2. Utilizing Virtual Private Networks (VPNs)
Virtual Private Networks (VPNs) are commonly exploited to evade age verification. By altering their IP addresses and routing internet traffic through servers in different locations, users make it seem as though they’re accessing content from a region with lax age restrictions. To counter this, businesses can incorporate IP geolocation services that compare a user’s claimed location with their actual IP address, spotting any discrepancies.
3. Borrowed Credentials
Minors often misuse the credentials of adults, such as parents or older siblings, to create accounts or gain entry to age-restricted content. This hinges on the expectation that legitimate adult accounts will provide unrestricted access. Addressing this, businesses can promote the adoption of two-step verification, which requires not only a password but also an additional ID verification method, reducing the chances of unauthorized access.
4. Accessing Third-Party Services
Third-party services that claim to facilitate age verification can be exploited by minors. These services are sometimes easily manipulated, allowing users to present falsified documents or information to meet age requirements. Businesses can protect against this by developing their own age verification algorithms that assess the authenticity of submitted data, diminishing their reliance on external services.
5. Manipulating Credit Card Verification
Certain platforms utilize credit card age verification, requiring users to input credit card details. Minors who know how to bypass credit card age verification may attempt to evade this by using adult-owned credit cards or acquiring prepaid cards. To counter such attempts, businesses can introduce multiple verification layers, combining credit card data with other authentication methods, like biometric identification.
6. YouTube Age Verification
With its widespread use, YouTube enforces age restrictions on certain content. Minors may attempt to bypass YouTube age verification by entering false birthdates or utilizing borrowed accounts to access videos not suitable for their age group. Businesses can collaborate with YouTube to bolster age verification mechanisms, leveraging advancements in AI and machine learning to identify anomalies in user behavior and flag potential violators.

What Is YouTube’s Age Restriction System? (And Why It Matters for Online Safety)
YouTube’s age restriction system acts as a critical safeguard to protect young users from inappropriate content while addressing legal and ethical concerns around children’s internet access. Let’s examine how it works and why these protections matter for privacy and security online.
What Content Gets Age-Restricted?
YouTube automatically flags videos containing:
- Nudity or sexual content (including suggestive themes)
- Graphic violence/gore (real or fictional depictions)
- Strong language (excessive profanity or hate speech)
- Dangerous activities (substance abuse, self-harm tutorials)
- Hateful/discriminatory material (targeting groups or individuals)
These restrictions align with global regulations like COPPA and demonstrate YouTube’s commitment to protecting your private information online while maintaining a safer platform.
How Age Verification Works?
When encountering restricted content, users must:
1. Sign in to a Google account
2. Verify they’re 18+ (via account birthdate)
3. Accept responsibility for viewing mature material
This process helps prevent how minors bypass age verification while providing accountability. However, determined users often seek age verification bypass methods – which introduces significant risks.
More importantly, circumventing these protections raises legal and ethical concerns – particularly regarding how to be safe on the Internet while respecting content boundaries. Parents concerned about protecting your private information online should consider monitoring tools rather than bypass methods.
How to Bypass YouTube Age Restrictions (And Why You Should Think Twice)
YouTube’s age restrictions are designed to protect younger users, but some viewers still look for ways to bypass age verification. While we don’t encourage violating YouTube’s policies, understanding these methods helps parents and guardians recognize potential risks.
Below are common age verification bypass techniques – along with their security and legal implications.
1. Set Up Your YouTube Account with the Correct Age
If you accidentally set the wrong birthdate, YouTube may block age-restricted content. To fix this:
- Go to your Google Account settings
- Update your birthdate (must be 18+)
- Refresh YouTube
Risk: Falsifying your age violates YouTube’s terms and could lead to account suspension. It also undermines privacy and security measures designed to protect minors.
2. Sign in with a Verified Google Account
Many age-restricted videos only require a signed-in Google account. If you’re not logged in:
- Click “Sign In” on YouTube
- Use an account with a verified 18+ age
Risk: If the account belongs to someone else, you may be compromising their private information online.
3. Install a Dedicated Browser Extension
Some extensions claim to bypass age verification by masking browser data. These tools often:
- Modify YouTube’s age-check prompts
- Trick the site into loading restricted videos
Risk: Browser extensions can contain malware, steal data, or violate legal and ethical concerns around content access.
4. Use a Third-Party YouTube Player
Websites like BitView or Invidious allow users to watch YouTube videos without age checks. These platforms:
- Strip away YouTube’s restrictions
- Let users watch anonymously
Risk: Unofficial sites may log your internet protocol (IP), inject ads, or expose you to malicious scripts – jeopardizing how to be safe on the internet.
5. Turn Off Restricted Mode
Restricted Mode (not the same as age restriction) filters mature content. This doesn’t bypass age-gated videos but reduces general content filtering. To disable it:
- Scroll to the bottom of YouTube’s settings
- Toggle “Restricted Mode” off
Is Bypassing Age Checks Worth It?
While these methods may work, they often come with security risks (malware, data theft), account penalties (bans for policy violations), and legal concerns (especially for minors).
Instead of trying to bypass age verification, consider safe alternatives like parental controls or discussing content boundaries openly.
Protecting Your Business: Effective Strategies
Today, there are far too many fraud threats online to use ineffective verification protocols. These methods can help you reinforce your system and prevent user ID fraud:
Two-Step Verification
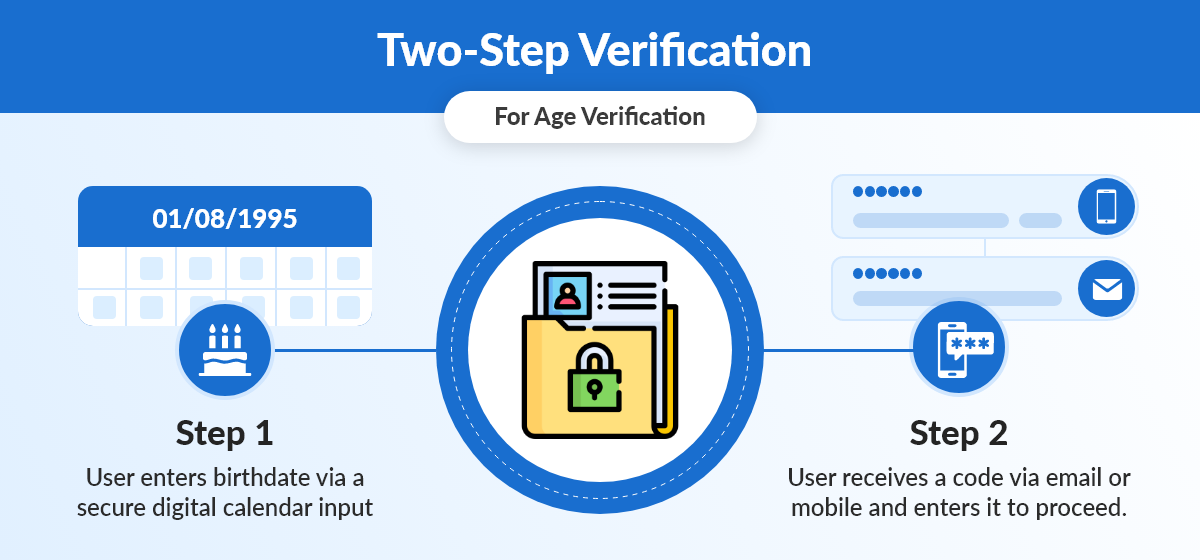
Implementing a two-step verification process enhances age verification. Users should provide their birthdate and complete an additional step, like entering a verification code sent to their email or mobile device. This additional layer of security reduces the likelihood of unauthorized access, even when fake information is provided.
Biometric Authentication
Integrating biometric authentication, such as fingerprint or facial recognition, adds another layer of identity validation during registration and access attempts. By scrutinizing unique biological features, businesses can ensure that users are genuinely who they claim to be, lowering the chances of bypassing verification.
Age Verification Services
Teaming up with reputable age verification services improves accuracy. These services cross-reference user data with official records, making it tougher for minors to manipulate the system. Integrating these services into the verification process allows businesses to benefit from their expertise in identity validation.
IP Geolocation
Leveraging IP geolocation services to identify users’ approximate physical locations can highlight age verification evasion. Inconsistent location data compared to registration information can trigger suspicion. By implementing this technology, businesses can uncover users attempting to exploit geographical inconsistencies.
Behavioral Analysis
Deploying algorithms to scrutinize user behavior patterns can uncover irregular activities or frequent attempts to access age-restricted content. Such anomalies can prompt heightened verification procedures. By closely monitoring user actions and interactions, businesses can swiftly identify and address suspicious behavior.
Regular Audits
Conducting periodic audits to uncover suspicious accounts or patterns is essential. Rapidly removing accounts found to have submitted false information is crucial. Regular audits maintain the integrity of the user base, ensuring the efficacy of age verification over time.
Final Thoughts
Safeguarding your online business from underage users who know how to bypass age verification necessitates a proactive approach. Age verification serves as a pivotal barrier, stopping minors from accessing inappropriate content. By implementing a multifaceted approach that combines advanced verification techniques, businesses can deter attempts to bypass age verification.
Striking the right balance between accessibility and security fuels growth, nurtures reputation, and ensures that underage users who know how to bypass age verification online are shielded from potentially harmful digital experiences. In this ever-evolving landscape, businesses can confidently navigate the challenges and emerge victorious in the fight against underage intrusion.
In the ever-evolving landscape of online security, innovative solutions like FTx Identity are emerging to tackle the challenges of age verification head-on. By harnessing cutting-edge technology and data integration, FTx Identity offers a formidable defense against age verification evasion.
Embracing such advancements empowers businesses to fortify their digital walls, ensuring a safer and more trustworthy online environment for all users. As the digital realm continues to evolve, staying ahead with forward-looking solutions like FTx Identity will be essential to maintaining a secure online presence.
Protect Your Business!
Steer clear of underage sales and avoid hefty fines with AI-based age and identity verifications in-store or online.
