Introduction
Identity verification used to be simple. Business was done face-to-face; you asked for ID and made sure the same person on the ID card was standing in front of you.
Now transactions have moved online, and verifications take place instantly. Remote age and identity verification systems make this possible.
And the idea of how they work is simple:
A remote identity verification (RIV) platform electronically verifies a customer’s date of birth, address history, and even social security number. The user uploads documents into the system, and then this information is cross-checked with databases and selfie photos. In other words, with remote identity verification, your business can verify identity documents online, from anywhere.
Remote identity verification (RIV) technology is transforming transactions in financial and banking, government, healthcare, and customer authentication (especially for age-gated content and products). Transactions that weren’t possible just a few years ago can now be processed in seconds. And the process is more secure than ever.
Curious how it works? Read on to learn how websites verify identities online, how it works, and why your business needs it.
What Is Remote Identity Verification?

When you can’t meet face-to-face with customers, your business needs a way to verify that customer’s identity. This is especially true for complex orders or large-ticket purchases.
Remote identity verification systems do precisely this. And the process is simple:
Customers use their phone or computer to “show you” their ID, and the technology then cross-references this with governmental and proprietary data. Additionally, selfie ID verification helps to validate photo IDs.
Here’s a quick overview of what RIV software does:
- The customer starts the RIV process online or via a mobile app.
- The customer takes a picture of their ID document (like a passport) with a smartphone or webcam.
- A quick selfie or fingerprint scan captures biometric data.
- Verification algorithms analyze the captured data against secure databases and employ liveness detection techniques.
- Within seconds, the customer receives a result.
Key Components of Remote ID Verification
To build trust in the digital world, businesses need secure, seamless, and scalable ways to verify customers without physical checks. That’s where remote ID verification steps in.
But what makes remote verification reliable? It’s not just about scanning an ID – it’s a multi-layered process that combines cutting-edge tech with fraud prevention.
Here’s how it works:
1. Document Verification
You can’t fake trust. That’s why remote ID verification starts with validating government-issued documents like passports, driver’s licenses, or national IDs.
How it works: AI scans the document, checks security features (holograms, watermarks), and cross-references data against global databases.
Why it matters: Prevents fake or stolen IDs from slipping through – keeping fraudsters out while letting real customers in.
2. Biometric Checks
A stolen ID won’t help if the system demands your face or fingerprint. Biometric authentication adds an unbeatable layer of security.
- Facial recognition: Matches a selfie with the ID photo in seconds
- Fingerprint scanning: Used for high-security sectors like banking
- Voice recognition: Emerging as a hands-free option
3. Liveness Detection
Sophisticated scams use masks, videos, or AI-generated faces. Liveness detection fights back by confirming:
- Is the person real? Users may blink, smile, or turn their head to prove it
- Is the session live? Detects screen recordings or pre-recorded videos
4. Real-Time Verification
Customers hate delays. Remote verify Know Your Customer (KYC) solutions like FTx Identity deliver results in seconds – not days.
- Instant checks: Cross-references data with global watchlists
- Seamless User Experience (UX): No frustrating hold-ups at checkout
- Higher conversions: Fewer drop-offs = more sales
How Remote Identity Verification Works
With remote identity verification, businesses can confirm a user’s identity in seconds without sacrificing security. But how does it actually work?
Let’s break it down step by step.
1. Identity Document Submission
The process kicks off when a user uploads a government-issued ID (like a passport, driver’s license, or national ID). No more manual data entry – just a quick snap or scan, and you’re on your way.
2. Biometric Capture
This is where remote KYC verification takes a high-tech approach. Users complete a facial recognition scan through a selfie or authenticate with a fingerprint, based on the required level of security.
For extra fraud prevention, FTx Identity uses liveness detection checks – requiring a real-time gesture (like a smile or head turn) to block deepfakes or stolen photos.
3. AI-Powered Analysis
Advanced algorithms instantly analyze the data through:
– OCR (Optical Character Recognition) extracts text from the ID in seconds.
– Document fraud detection checks for tampering, fake holograms, or altered data.
– Data matching cross-references the ID info with the user’s biometrics and global databases.
This step ensures only legitimate, untampered IDs pass through.
4. Verification Decision
In most cases, real-time approval happens instantly. But if something seems off (like a blurry ID or mismatched biometrics), the system escalates to manual review – adding a human layer for tricky cases. Either way, users get a quick resolution.
5. Record Keeping & Reporting
Every verification leaves a secure audit trail, including:
– API logging for seamless integration with your systems.
– Automated alerts for suspicious activity.
– Proof of verification for compliance (crucial for age-restricted industries).
Why Remote Identity Verification Matters
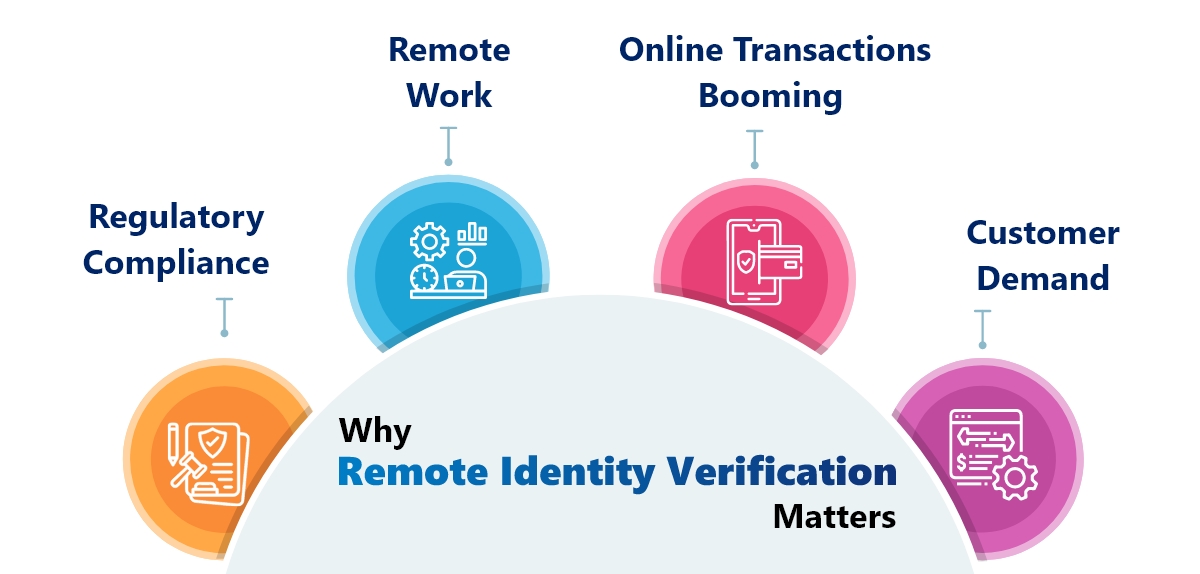
More and more people are moving online to do everything from purchasing their favorite electronics to getting verified for work. This shift means businesses need to prepare, as many customers have come to expect it.
Here are some of the use cases of remote identity verification:
Regulatory Compliance
The digital landscape is rapidly evolving. And so too are the regulations aimed at combatting fraud and protecting customer data. The European Union’s General Data Protection Regulation (GDPR) puts strict requirements on the types of data that businesses can collect and store.
Compliance mandates like Know Your Customer (KYC) and Anti-Money Laundering (AML) are becoming increasingly stringent. Today, the onus is on businesses to perform KYC verification online and authenticate identities accurately and securely.
Remote Work
The lines between physical and virtual workplaces are blurred. Now, businesses have employees scattered across the globe.
RIV software helps businesses seamlessly onboard new employees and perform identity verification (regardless of location).
Online Transactions Booming
According to Shopify, global ecommerce sales are expected to grow from $5.13 trillion in 2022 to an incredible $8.09 trillion by 2028. This surge in online shopping translates to a greater need for secure, efficient ID verifications.
Ecommerce verifications are especially important for high-dollar-amount items, age-restricted items (which are being increasingly sold online), and other products that require secure shipping.

Customer Demand
Today’s customers are tech-savvy. And they’re easily put off by inefficient or seemingly insecure verification platforms. An advanced RIV platform integrates with your existing website and tech environment. Therefore, you can build and deploy these systems faster than ever.
Ultimately, remote identity verifications will be required to sell products online and process transactions. Businesses that don’t integrate these systems will be left behind.
The Rise of Remote ID Verification in Response to Digital Fraud
The digital revolution has brought convenience – but also a surge in identity theft, synthetic fraud, and account takeovers. As more transactions move online, fraudsters are getting smarter.
– $8.8 billion lost to identity fraud in 2022 alone, according to the Federal Trade Commission (FTC).
– Synthetic identity fraud (combining real and fake data) is the fastest growing type of fraud, as reported by TransUnion.
– Account takeover losses increased by 90% year-over-year, according to a 2022 Javelin Strategy & Research study.
The stakes are high – but so are the solutions.
So, does how remote ID verification fight back?
Traditional methods (like manual checks or static passwords) crumble against modern fraud. Remote identity verification acts as a digital shield stopping scams like:
- Fake account creation: A fraudster tries to open a loan using a stolen ID. Biometric liveness detection blocks them.
- Underage purchases: A teen uses a parent’s ID to buy vapes online. AI age verification flags the mismatch.
- Money laundering: A criminal uses a deepfake video to bypass a bank’s KYC.
Regulatory Pressure: KYC & AML Are Non-Negotiable
Laws like GDPR, Financial Industry Regulatory Authority (FINRA), and the Bank Secrecy Act now require:
– Real-time identity proofing for high-risk transactions
– Audit trails for every verification
– Strict age checks in cannabis, gaming, and alcohol sales
Remote verify KYC solutions like FTx Identity turn compliance from a headache into a competitive edge – automating checks while keeping customers moving.
Use Cases of Remote Identity Verification
As digital interactions become the norm, remote identity verification becomes crucial for stopping fraud, streamlining onboarding, and much more. Industries across the board are leveraging this tech to boost security and user experience.

Let’s explore the key sectors transforming their operations with AI-powered verification:
1. Financial Services: Fighting Fraud in Real-Time
Banks, fintechs, and lenders face sky-high risks – from money laundering to synthetic identity scams.
Prevents: Account takeovers, loan fraud, and fake profiles
How it works:
- Remote verification of KYC via document + biometric checks
- Device reputation analysis to flag suspicious logins
- Instant AML screening against global watchlists
2. Online Gaming & Gambling: Keeping Underage Users Out
With strict age-compliance laws, platforms must verify users without killing the fun.
Prevents: Underage signups, multi-accounting, and chargeback fraud
How it works:
- AI age verification scans IDs in seconds
- Continuous authentication monitors for account sharing
- Geolocation checks to enforce regional laws
3. HR & Remote Hiring: Trusting Who You Hire
Global teams need to verify candidates’ identities and credentials fast.
Prevents: Fake resumes, impersonation in interviews
How it works:
- Document + biometric checks for I-9 and background checks
- Educational credential verification via integrated databases
- Secure digital signing for offer letters
4. Healthcare: Securing Patient Identities
From telehealth to pharmacies, patient safety starts with ID checks.
Prevents: Medical identity theft, prescription fraud
How it works:
- Health Insurance Portability and Accountability Act of 1996 (HIPAA)-compliant verification for telehealth logins
- Age checks for controlled substance deliveries
- Single sign-on (SSO) for verified returning patients
5. Real Estate: Closing Deals Securely
Remote property sales require verified identities to prevent million-dollar scams.
Prevents: Title fraud, rental scams, and wire fraud
How it works:
- Biometric notarization for digital contracts
- Tenant screening with instant ID + credit checks
- Document tampering detection for lease agreements
6. Ecommerce & Online Marketplaces: Stopping Fraud at Checkout
Chargebacks, fake accounts, and first-party fraud drain profits. Remote ID verification balances security and speed.
Prevents: Card-not-present fraud, return scams, fake reviews
How it works:
- Age verification for alcohol/vape sales
- Low friction checks for high-risk transactions
- Verified buyer badges to build trust

How Banks Verify Your Identity Remotely: Secure Banking in the Digital Age
Gone are the days of in-person bank visits for identity checks. Today, banks use three layers of remote identity verification methods to onboard customers safely and instantly.
First, document verification kicks off the process. You’ll upload a government ID and proof of address, which AI scans using OCR technology while checking for tampering against global databases. This catches 99.7% of fake IDs by analyzing security features like holograms and micro-printing.
Next comes biometric authentication, where your live selfie gets matched to your ID photo. Advanced liveness detection blocks fraudsters using photos or deepfake videos, while optional fingerprint or voice recognition adds extra security for high-value transactions.
Finally, banks employ ongoing risk assessment through device recognition and behavioral biometrics. This continuous monitoring spots suspicious activity like account takeovers while reducing false declines for legitimate customers – all while maintaining 24/7 compliance with KYC/AML regulations.
The result?
Security meets convenience: customers enjoy minute-long onboarding without branch visits, while banks slash fraud cases substantially. With solutions like FTx Identity, remote verification is transforming banking into a safer, smoother experience for everyone.
Benefits of Effective Remote Identity (ID) Verification
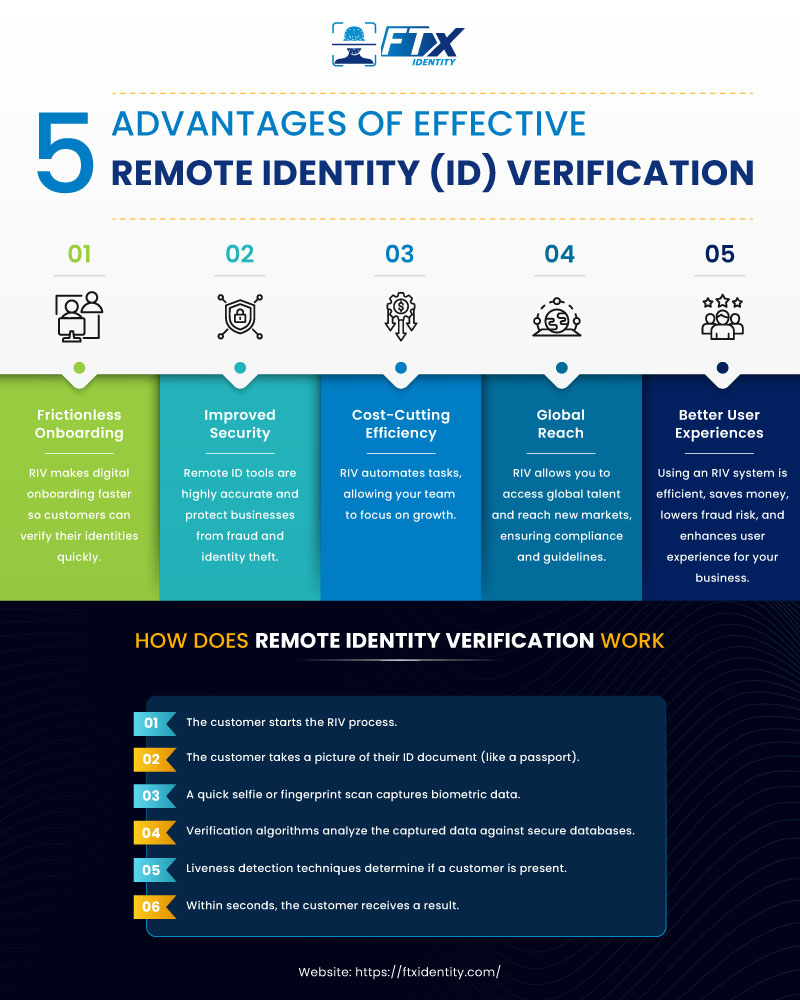
Remote identity verification unlocks a trove of advantages for your business. Say hello to streamlined onboarding, lower fraud risk, and smoother customer experiences.
Here are some key benefits of using RIV to verify someone’s identity online:
Frictionless Onboarding
Traditional paper-based onboarding processes are not only cumbersome for customers. They also create bottlenecks that stifle growth.
RIV streamlines the digital onboarding process, allowing customers to verify their identities in minutes. This translates into higher conversion rates and happier customers.
Improved Security
Fraudulent accounts and identity theft are nightmares that haunt every online business. However, RIV uses a variety of technologies that block fraudsters.
In fact, many liveness detection tools are accurate up to 99%, and the accuracy of analytics and fraud detection systems has greatly accelerated. The result: Better security for your business.
Cost-Cutting Efficiency
RIV automates workflows. This reduces operational costs, processing costs, and frees your team to focus on growth and innovation.
Many businesses reinvest these saved costs in marketing, product development or expanding their services.
Global Reach
With RIV, you can tap into a vast pool of international talent. Or expand your customer base to new markets. This makes it possible to meet international data safety guidelines, no matter where your home base is.
Better User Experiences
Better security and faster onboarding = happier customers. A smoother user experience can make a big difference, boosting your onboarding rates and cutting out those frustrating roadblocks that might turn potential users and customers away from your platform.
Bottom line, identifying customers online with an RIV system is more efficient, it saves costs, and it will lower your business’s fraud risk.
Why Remote Identity Verification is Critical in 2025 & Beyond
The digital world demands smarter security. As technology advances, remote identity verification has become vital – not just for fraud prevention, but for staying compliant and meeting user expectations. Here’s what’s driving its importance:

1. Cybersecurity Threats Are Evolving
Fraudsters now use deepfakes and synthetic identities to bypass traditional checks, while phishing and impersonation attacks grow more sophisticated. Remote verification combats these risks with:
- AI-driven liveness detection to expose fake identities
- Biometric matching to ensure real users are behind every transaction
- Continuous authentication to detect anomalies in real time
Without these measures, businesses leave themselves open to breaches and financial losses.
2. Compliance Requirements Are Stricter
Global regulations like KYC, AML, GDPR, and the California Consumer Privacy Act (CCPA) now enforce stricter identity checks. Companies must:
- Verify identities digitally while maintaining privacy
- Keep audit-ready records for compliance reporting
- Adapt to regional laws as they evolve
Automated remote verification ensures businesses stay compliant without slowing down operations.
3. Users Demand Speed and Security
Modern customers expect instant, hassle-free access – without sacrificing safety. Remote verification meets these demands by offering:
- Quick, document-free onboarding via biometrics
- Seamless authentication across devices
- Global accessibility – no physical checks required
Businesses that fail to deliver risk losing users to competitors with smoother processes.
Challenges and Risks to Consider with Remote Identity Verification
While remote identity verification offers immense benefits, businesses must also navigate potential pitfalls. Understanding these challenges helps in selecting the right solution and optimizing the user experience.
1. False Positives/Negatives
Overly strict verification may wrongly reject legitimate users (false positives), while lax systems approve fraudsters (false negatives). Balancing accuracy with inclusivity is key – AI-powered adaptive checks can help minimize errors.
2. Bias in AI Facial Recognition
Some facial recognition algorithms perform unevenly across demographics, leading to unfair rejections. Choosing bias-tested, diverse training data models ensures equitable verification for all users.
3. Data Privacy Concerns
Storing biometric and ID data raises GDPR/CCPA compliance risks. Solutions must use encrypted storage, zero-knowledge proofs, or decentralized identity to protect sensitive information.
4. Technical Integration with Legacy Systems
Many businesses struggle to connect modern verification tools with outdated platforms. Prioritizing API-first solutions with flexible middleware eases adoption without full system overhauls.
5. User Drop-Off During Verification
Complex or lengthy checks frustrate users, increasing abandonment. Optimizing steps (like single-image document scans) and progress indicators keep completion rates high.
Best Practices for Implementing Remote Identity Verification
Deploying remote identity verification successfully requires balancing security, compliance, and user experience. Follow these key strategies to maximize adoption while minimizing fraud risks.
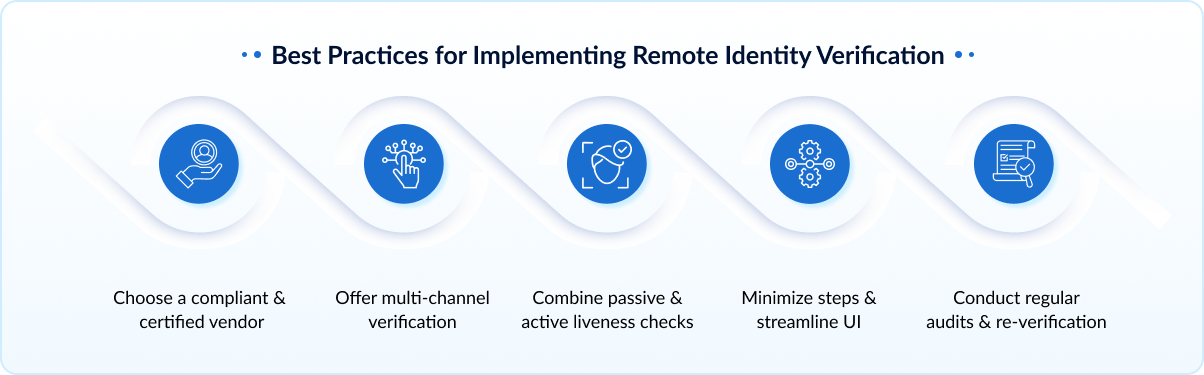
1. Choose a Compliant & Certified Vendor
Partner with providers that meet Organization for Standardization (ISO) standard number 27001 (ISO 27001), System and Organization Controls 2 (SOC 2), or National Institute of Standards and Technology (NIST) standards – ensuring enterprise-grade security and GDPR/CCPA compliance. Third-party audits verify their systems handle data responsibly.
2. Offer Multi-Channel Verification
Support mobile, desktop, and in-app verification to meet users where they are. A consistent cross-platform experience prevents drop-offs and expands accessibility.
3. Combine Passive & Active Liveness Checks
Passive checks (background analysis) reduce friction, while active challenges (smiling/turning) add security for high-risk transactions. Layering optimizes both accuracy and UX.
4. Minimize Steps & Streamline UI
Each extra click increases abandonment. Use auto-capture document scanning, pre-filled fields, and clear progress indicators to speed verification.
5. Conduct Regular Audits & Re-Verification
Periodically re-check user identities and update risk models. Continuous monitoring catches compromised accounts and maintains KYC/AML compliance.
How to Choose the Right Remote Identity Verification Provider?
Selecting a remote identity verification partner is a strategic decision that impacts security, compliance, and customer experience. Use this criteria checklist to evaluate solutions effectively.
1. Regulatory Compliance (KYC, AML, GDPR)
Ensure the provider meets global standards like KYC, AML, and data privacy laws (GDPR, CCPA). Compliance certifications like ISO 27001 and SOC 2 add an extra layer of trust and reduce legal risks.
2. Biometric & Document Verification Capabilities
Look for AI-powered liveness detection, facial recognition, and document fraud checks (holograms, OCR). The best solutions support multiple ID types and adapt to emerging fraud tactics.
3. API and SDK Availability
A flexible Application Programming Interface (API) and ready-to-use Software Development Kits (SDKs) (iOS, Android, Web) ensure smooth integration with your existing systems – cutting deployment time from weeks to days.
4. Support & Onboarding Assistance
Choose a provider with 24/7 technical support and dedicated onboarding teams. Migration guides, sandbox testing, and Service Level Agreement (SLA)-backed response times minimize downtime.
5. Reporting and Analytics
Real-time fraud analytics and customizable reports help track verification success rates, fraud attempts, and user drop-off points – key for optimizing workflows.
Wrapping Up
Remote identity verification systems offer a plethora of benefits. But remember that responsible implementation and a commitment to user trust are the keys to implementing RIV technology. A breach can destroy your reputation and trust.
That’s why it’s important to choose a reputable remote identity verification platform. FTx Identity offers tools to help businesses with a variety of ID checks online. Our platform is ideal for ecommerce, age-restricted content, online-to-offline retail (e.g., liquor stores / vape shops), and other online verification types.
Future-proof your verification process with FTx Identity:
- Omnichannel verification
- Zero compliance headaches
- Easy customer onboarding
