Guest identity verification has become an important aspect of business operations, particularly in the hospitality sector in the fast-evolving digital age.
It’s the bridge that connects security with excellent customer experience. This process goes beyond checking IDs – it’s about building trust and ensuring safety in a world where online bookings are the norm. With increasing instances of fraud, identity verification serves as a frontline defense, protecting both businesses and guests.
This blog post will explore the workings of guest identity verification, its significance, methods, benefits, challenges, and how industries can integrate it into their operations.
What Is Guest Identity Verification?
Guest identity verification is the process of confirming the legitimacy of a guest’s identity using various methods. This typically involves checking personal documents, biometric data, and other identifiers to ensure that the individual is who they claim to be.
In the hospitality sector, this process is crucial for maintaining security and providing a seamless guest experience. With the rise of online bookings, it’s become increasingly important to verify guest identities before they arrive. This preemptive step helps deter potential threats and ensures that all guests have a safe and enjoyable stay.

The Importance of Guest Identity Verification
Guest ID verification is important for several reasons, including the following:
Building Trust and Security
Trust is the foundation of any business-to-customer relationship.
For property owners and businesses in the hospitality sector, guest identity verification is a vital tool for building and maintaining trust. By ensuring that every guest is who they claim to be, businesses can significantly reduce the risk of fraudulent activities. Implementing robust verification processes can greatly mitigate these risks.
Legal and Regulatory Compliance
Adhering to legal requirements for guest identification is not just about avoiding penalties – it’s about upholding the integrity of your business operations. Failing to comply with these regulations can result in heavy fines and damage to your business reputation.
Understanding and implementing the necessary legal protocols for guest identity verification is a critical step for any business in the hospitality sector.
Reducing Risks
Unverified guests pose a number of risks, including fraud, theft, and other security issues. These incidents can result in financial losses and damage the reputation of your business.
By implementing thorough guest identity verification processes, businesses can significantly reduce these risks, ensuring a safer environment for both guests and staff.
Common Methods of Guest Identity Verification
Guest identity verification is crucial for ensuring security and trust in various industries, especially in hospitality.
Here are some common methods used for verifying guest identities:
1) Document Verification
Document verification involves checking government-issued IDs like passports or driver’s licenses to confirm a guest’s identity. This method is straightforward and widely used across various industries.
2) Biometric Authentication
Biometric authentication uses unique biological characteristics, such as fingerprints or facial recognition, to verify identity. It’s a secure method that adds an extra layer of protection against identity fraud.
3) Two-Factor Authentication (2FA)
2FA requires users to provide two different types of information to verify their identity. This could be something they know (a password) and something they have (a smartphone). It’s an effective way to enhance security.
4) Digital Verification Services
Digital verification services use advanced technologies to automate the identity verification process. These services can quickly verify documents and biometrics, providing a seamless experience for both businesses and guests.
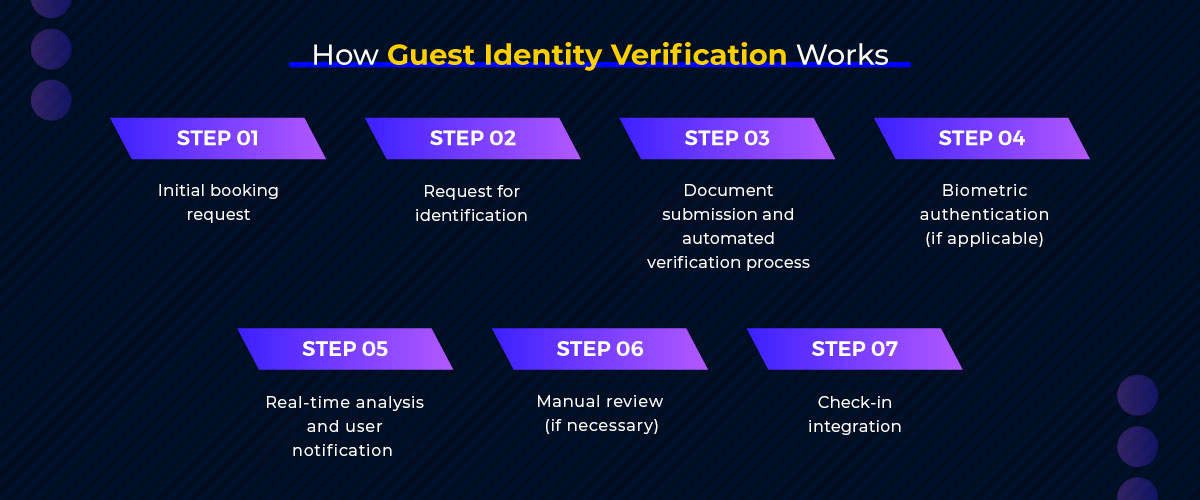
How Guest Identity Verification Works
The guest identity verification process involves several steps, from the initial booking request to secure data storage.
1) Initial Booking Request
The process begins when a guest submits a booking request. At this stage, they are informed about the need for identity verification.
2) Request for Identification
Once the booking is confirmed, the guest is asked to submit identification documents. This can be done online for convenience.
3) Document Submission and Automated Verification Process
Guests submit their documents, which are then automatically checked for authenticity. Advanced algorithms are used to extract relevant data and cross-check it against databases.
4) Biometric Authentication (if applicable)
If biometric authentication is part of the process, guests may be asked to provide additional information, such as a fingerprint or facial scan.
5) Real-Time Analysis and User Notification
The system performs real-time analysis to verify the guest’s identity. Once verified, the guest is notified, and their data is securely stored.
6) Manual Review (if necessary)
If the automated process flags any issues, a manual review is conducted to ensure accuracy. This step helps prevent false positives or negatives.
7) Check-In Integration
The verification process is seamlessly integrated with the check-in system, ensuring a smooth experience for guests upon arrival.
Top 7 Benefits of Guest Identity Verification
1) Enhanced Security and Fraud Prevention
By verifying identities, businesses can prevent unauthorized access and reduce instances of fraud, creating a safer environment for everyone.
2) Improved Guest Experience
Verified identities streamline the check-in process, reducing wait times and enhancing the overall guest experience.
3) Legal and Regulatory Compliance
Staying compliant with identity verification regulations helps businesses avoid penalties and maintain a positive reputation.
4) Increased Operational Efficiency
Automating the verification process reduces the workload for staff, allowing them to focus on delivering excellent service.
5) Enhanced Data Privacy and Security
Securely storing guest data and using encrypted verification methods protect both guests and businesses from data breaches.
6) Better Risk Management
By identifying potential risks early, businesses can take proactive measures to mitigate them, ensuring smooth operations.
7) Competitive Advantage
Offering secure and efficient identity verification can set a business apart from competitors, attracting more guests.
Challenges in Guest Identity Verification
Despite its benefits, guest identity verification comes with challenges, including:
1) Guest Resistance
One of the primary hurdles is guest resistance. Some individuals may be hesitant to provide personal information due to concerns about privacy violations and data misuse. This reluctance can stem from previous experiences or a general distrust in how their information will be handled, making it essential for businesses to communicate the importance and safety of the verification process effectively.
2) Technological Limitations
Another major challenge is technological limitations. Outdated systems or incompatible software can severely hinder the verification process, leading to inefficiencies and errors. Businesses may struggle to integrate new verification technologies with legacy systems, which can slow down operations and frustrate both staff and guests.
3) Variability in Identification Documents
The variability in identification documents can make things tricky. Different countries have a range of ID formats, which can make standardization difficult. This inconsistency can lead to confusion and errors during the verification process, as staff may not be trained to recognize or validate all types of foreign identification effectively.
4) False Positives/Negatives
Automated systems can also present challenges through issues of accuracy, resulting in false positives or negatives. These automated checks may mistakenly flag legitimate guests as potential threats, creating unnecessary delays and inconveniences. Such errors can damage the guest experience and lead to dissatisfaction and distrust.
5) Data Privacy Concerns
Handling sensitive guest information brings about data privacy concerns that must be addressed. Businesses are required to adhere strictly to data protection laws and regulations, which can vary significantly by region. This compliance necessitates robust data management practices and transparency in how guest information is collected, stored, and used.
6) Operational Costs
Implementing a comprehensive guest verification system can incur substantial operational costs, which may be a barrier for some businesses. The investment in technology, training, and ongoing maintenance can strain budgets, especially for smaller establishments.
7) Staff Training and Adaptation
Effective management of the verification process also relies heavily on staff training and adaptation. Employees need to be well-trained not only in the technical aspects of the verification systems but also in handling guest interactions sensitively and professionally. Ongoing training programs can help ensure that staff remain updated on best practices and emerging technologies.
8) Handling Non-Verified Guests
Finally, businesses must establish clear protocols for dealing with guests who cannot be verified. This requires a strategic approach to ensure that non-verified guests are treated fairly while maintaining the integrity of security measures. Having a well-defined process in place can help mitigate potential conflicts and enhance the overall guest experience.
How Industries Take Advantage of Guest Identity Verification
1) Hospitality Industry
Hotels and resorts use identity verification to enhance security, streamline check-ins, and improve guest satisfaction.
2) Rental Industry
Vacation rentals and short-term accommodations use verification to prevent fraud and ensure safe transactions.
3) Healthcare
Medical facilities use identity verification to protect patient data and ensure accurate record-keeping.
4) Retail and Ecommerce
Online retailers use verification to prevent fraud and protect sensitive customer information.
5) Gaming and Entertainment
Casinos and gaming platforms use verification to ensure fair play and prevent underage access.
Integrating Guest Identity Verification into Your Operations
1) Assess Current Processes
Review existing guest identification methods, identify gaps, and determine areas for improvement.
2) Choose the Right Software
Evaluate various identity verification solutions to find one that aligns with your business needs.
3) Develop an Implementation Plan
Outline key milestones, assign responsibilities, and set timelines for the integration process.
4) Set Up Technical Infrastructure
Ensure that the verification software is compatible with your booking system and that cybersecurity measures are in place.
5) Create Standard Operating Procedures (SOPs)
Develop clear protocols for guest verification and handling exceptions.
6) Staff Training
Conduct training sessions to familiarize staff with the new guest verification system and emphasize the importance of compliance.
7) Communicate with Guests
Inform guests about the verification process and provide clear instructions for submitting identification.
8) Monitor and Evaluate Performance
Track the effectiveness of the verification process and gather feedback from staff and guests.
9) Adjust and Optimize Processes
Make necessary adjustments based on performance data and continuously update procedures to address new challenges.
10) Ensure Compliance
Regularly review data protection policies and stay updated on legal requirements related to guest information.
11) Utilize Analytics for Insights
Analyze verification success rates and guest experiences to enhance future operations.
12) Plan for Scalability
Ensure the system can handle peak seasons and increased guest volume and develop strategies for quick adaptation.
Wrapping Up
Incorporating guest identity verification into your business operations is important for boosting security, improving efficiency, and gaining a competitive edge in today’s fast-paced world.
As safety and privacy concerns grow, recognizing the importance of this practice helps businesses build trust and create a safer, more enjoyable environment for guests. By using effective identity verification systems, companies can reduce risks related to fraud and unauthorized access, ultimately leading to a better experience for everyone.
We at FTx Identity invite you to reach out to set up a consultation and explore our solutions with a demo or trial period and see for yourself how we can transform your business operations today!
