Customer identity verification is more than just a protocol; it’s the backbone of secure transactions and trust-based customer relationships in the digital age.
For business owners in 2024 and beyond, accurate identity verification is essential for protecting against fraud and meeting strict regulations.
Business owners need to understand this process to protect their operations and offer smooth experiences for customers. In this blog post, we’ll look at customer identity verification, why it matters for businesses, and the methods and benefits it provides.
What Is Customer Identity Verification?
Customer identity verification is a process that ensures that the person or entity claiming an identity is who they say they are. Its main goal is to prevent unauthorized activities, protect customer data, and ensure compliance with legal requirements.
Unlike authentication, which is about confirming identity using passwords or tokens, and authorization, which determines access rights, identity verification is about proving that the claimed identity is legitimate.
Key terms like KYC (Know Your Customer) and AML (Anti-Money Laundering) have become indispensable in this realm. Understanding these concepts helps businesses develop a solid framework for identity verification, enhancing both security and customer trust.
Why Customer Identity Verification is Important for Businesses
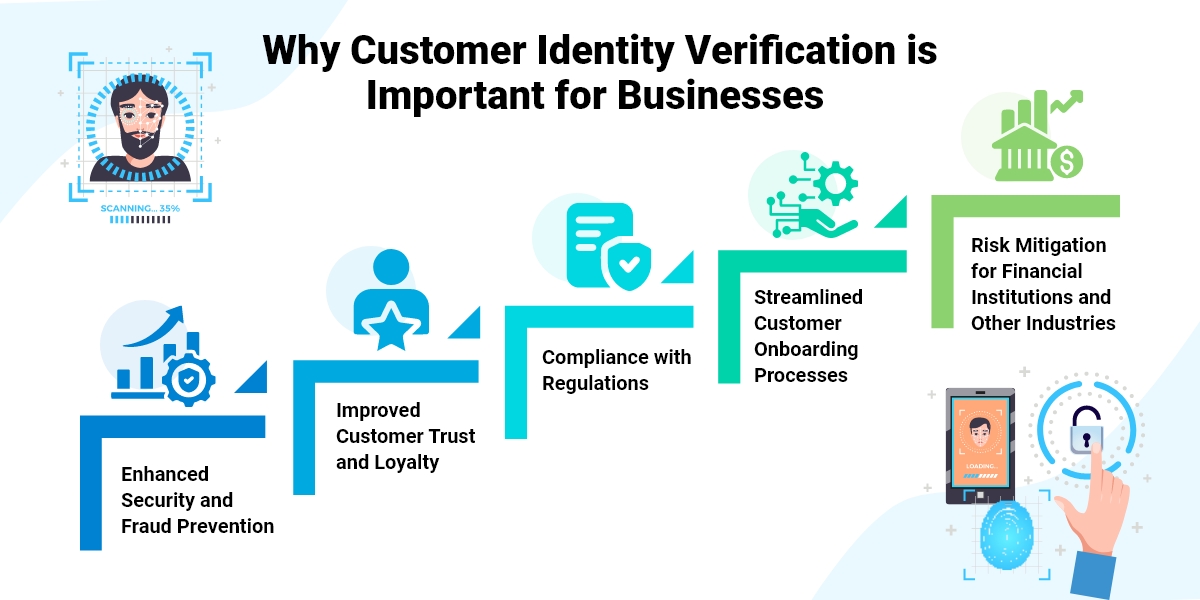
Customer identity verification is essential for a variety of reasons, including the following:
Enhanced Security and Fraud Prevention
For business owners, security breaches can be expensive and cause harm to their reputation. By implementing strong identity verification processes, you can significantly lower the risk of fraud and unauthorized access, protecting your business from major financial losses.
Improved Customer Trust and Loyalty
Customers are more likely to engage with brands they can trust. By ensuring thorough identity verification, you show your dedication to their security, which helps build loyalty and encourages them to return. A secure experience is a positive experience, which is important for keeping customers.
Compliance with Regulations
Following regulations like KYC and AML is not just a legal requirement; it’s also essential for business operations. Compliance helps you avoid legal issues and maintain your business’s integrity and reputation with customers and stakeholders.
Streamlined Customer Onboarding Processes
A smooth onboarding process gives off the right vibe for customer interactions. Effective identity verification can make onboarding easier, ensuring a seamless experience and reducing the time it takes for customers to access your services.
Risk Mitigation for Financial Institutions and Other Industries
Risk is a part of industries like finance and ecommerce, but it can be managed with strong identity verification. By accurately identifying customers, businesses can evaluate potential risks and take steps to minimize them, protecting both their interests and those of their customers.
What Is the Customer Verification Process?

The customer verification process typically involves a series of steps to confirm an individual’s identity.
While specific methods may vary depending on the industry and regulatory requirements, the following are some common steps involved in customer identity verification:
Data Collection and Management
The customer verification process begins with collecting essential data from customers. This data includes personal details such as name, address, and contact information. Proper data management is crucial to ensuring accuracy and minimizing the risk of errors during the verification process. Advanced data collection techniques, including online forms and secure databases, streamline the process while maintaining data integrity.
Identity Verification
Once the necessary data is collected, the verification process is ready to happen. Various methods, including document verification and biometric analysis, are used to validate the provided information. Identity verification makes sure that customers are who they claim to be, reducing the risk of identity theft and fraud. Modern verification tools use advanced technologies to boost accuracy and efficiency.
Risk Assessment and Fraud Prevention
Incorporating risk assessment into the verification process adds an extra layer of security. By analyzing behavior patterns, transaction history, and external data sources, businesses can identify potential threats and take proactive measures to prevent fraud. Risk assessment tools help businesses make informed decisions using data insights, improving security and reducing vulnerabilities.
User Experience and Frictionless Onboarding
Finding the right balance between security and user experience can be tricky. A seamless onboarding process requires minimizing friction while ensuring thorough verification. User-friendly interfaces, intuitive navigation, and clear instructions contribute to a positive experience. Businesses that prioritize user experience during the verification process enhance customer satisfaction, leading to higher engagement and retention rates.
Data Privacy and Security
Data privacy and security are crucial in the customer verification process. Businesses must implement robust encryption protocols to protect sensitive information from unauthorized access. Compliance with data protection regulations, such as GDPR and CCPA, ensures that customer data is handled responsibly. Prioritizing data privacy not only fulfills legal obligations but also fosters trust and confidence among customers.
Methods of Customer Identity Verification
The customer verification process uses a variety of methods to ensure someone is accurately identified.
Some common methods include:
Document Verification
Document verification involves validating the authenticity of government-issued IDs, such as passports and driver’s licenses. This method is widely used due to its reliability in confirming a person’s identity. Advanced technologies can analyze documents for signs of forgery or tampering, ensuring a high level of accuracy.
Biometric Authentication
Biometric authentication leverages unique biological traits, such as fingerprints or facial recognition, to verify an individual’s identity. This method offers a high level of security because biometric data is difficult to replicate. Businesses can enhance security by integrating biometric authentication into their verification processes.
Knowledge-Based Verification
Knowledge-based verification involves asking customers specific questions that only they would know the answers to. Examples include asking the customer their mother’s maiden name or the name of their elementary school. This method is commonly used as an additional layer of security. It’s important to make sure the questions are challenging but not too difficult for the customer.
Behavioral Analysis
Behavioral analysis evaluates user behavior, such as typing patterns and device usage, to detect anomalies that may indicate fraudulent activity. By analyzing behavioral patterns, businesses can identify potential threats and take appropriate action to protect customer accounts.
Digital Identity Verification
Digital identity verification uses online data sources and algorithms to confirm a person’s identity. This method is ideal for remote verification and provides businesses with a comprehensive view of a customer’s digital footprint. It offers a convenient and efficient way to verify identities in the digital age.
Legal and Regulatory Considerations

Compliance with legal and regulatory requirements is crucial for businesses dealing with customer identity verification. Failing to adhere to these regulations can result in major penalties, financial losses, and reputational damage.
Businesses need to stay alert and informed about changing regulations, making sure their identity verification processes comply with the relevant laws and standards.
Overview of Key Regulations
Key regulations like Know Your Customer (KYC), Anti-Money Laundering (AML), General Data Protection Regulation (GDPR), and California Consumer Privacy Act (CCPA) guide identity verification practices. These rules are designed to prevent fraud, protect consumer privacy, and ensure sensitive data is handled responsibly.
For businesses, understanding and following these regulations is crucial to operate ethically and legally, protecting both their interests and those of their customers.
Specific Requirements for Different Industries
Different industries have their own unique requirements and challenges when it comes to identity verification. Financial services, for example, deal with strict regulations due to the high risk of financial crimes, while ecommerce businesses must prioritize secure transactions and customer trust.
By tailoring identity verification processes to meet the specific needs of their industry, businesses can reduce risks and stay compliant with relevant regulations.
Potential Penalties for Non-Compliance
Non-compliance with identity verification regulations can result in severe consequences, including hefty fines, legal action, and reputational damage. Businesses that fail to adhere to these standards risk losing customer trust and facing long-term operational challenges.
By prioritizing compliance and staying informed about regulatory changes, businesses can avoid potential pitfalls and maintain a strong legal standing.
Challenges in ID Verification
While customer identity verification offers significant benefits, it also introduces a complex set of challenges, including the following:
Identity Theft and Fraud
Identity theft and fraud are major concerns in the digital age. Cybercriminals are always coming up with new ways to take advantage of weaknesses in identity verification systems, which puts both businesses and consumers at risk.
To fight against identity theft, businesses need to be on the lookout and proactive, using advanced verification methods and security measures to protect customer data.
Ensuring User Privacy and Data Protection
Protecting user privacy and data is a fundamental challenge in identity verification. Businesses must balance the collection and use of personal information with the need to safeguard it from breaches and unauthorized access.
Adhering to data protection regulations and implementing robust security practices are essential steps in ensuring that customer data remains private and secure throughout the verification process.
Balancing Security with User Experience
Striking the right balance between security and user experience is a challenge for businesses. While robust verification measures are necessary to prevent fraud, they can also introduce friction and inconvenience for customers.
By implementing user-friendly verification methods and optimizing processes, businesses can maintain security without sacrificing the customer experience, ensuring a seamless and satisfying interaction.
Technical Glitches and User Experience Issues
Technical glitches and user experience issues can hinder the effectiveness of identity verification processes. System outages, slow response times, or complex interfaces can frustrate customers and lead to abandonment.
To mitigate these challenges, businesses must invest in reliable technology and conduct regular testing to ensure that their verification systems are robust, user-friendly, and capable of handling high volumes of traffic.
Best Practices for Customer ID Verification

Keep your business and customers safe with these essential verification practices:
Choosing the Right Verification Method
Selecting the appropriate verification method for your business is crucial to achieving a balance between security and user experience. Factors such as industry requirements, customer demographics, and risk levels should inform your decision.
By leveraging a combination of verification techniques, businesses can enhance security while providing a smooth and efficient experience for customers.
Implementing Robust Security Measures
Robust security measures are essential to protecting customer data and ensuring the integrity of identity verification processes. Encryption, multi-factor authentication, and regular security audits are critical components of a secure verification framework.
By prioritizing security, businesses can reduce the risk of data breaches and maintain customer trust, safeguarding their reputation and bottom line.
Providing Clear and Transparent Communication
Clear and transparent communication is vital to fostering trust and ensuring a positive customer experience. Businesses should provide detailed information about verification processes, data handling practices, and security measures.
By being open and honest with customers, businesses can alleviate concerns and demonstrate their commitment to protecting customer data, enhancing overall satisfaction and loyalty.
Continuous Monitoring and Improvement
Continuous monitoring and improvement are essential to maintaining the effectiveness of identity verification processes. Regularly reviewing and updating procedures, technologies, and security measures ensures that businesses stay ahead of emerging threats and evolving regulations.
By adopting a proactive approach to identity verification, businesses can enhance security, improve customer satisfaction, and drive long-term success.
Wrapping Up
Customer identity verification is an essential part of modern business operations. By understanding its importance, methods, and challenges, businesses can carry out effective verification processes that enhance security, build trust, and ensure compliance. In an era where digital interactions are the norm, prioritizing identity verification is important for long-term success.
For business owners, the main point is simple: investing in solid identity verification processes isn’t just about meeting regulations; it’s a smart strategy that helps your business grow and stay competitive. Explore further resources and expert guidance to continue enhancing your identity verification strategies and stay ahead in the digital age.
To get started with FTx Identity, be sure to reach out to us today to schedule a consultation and experience a demo!
