The cryptocurrency world has exploded in recent years, completely changing how we think about transactions, investments, and financial systems. But with this rapid growth comes a fair share of risks.
The crypto industry isn’t immune to challenges like fraud, identity theft, and tight regulatory oversight, and businesses dealing with cryptocurrency are feeling the pressure more than ever.
That as of January 24th of this year, the cryptocurrency market capitalization has soared to $3.65 trillion, almost doubling its value from $1.80 trillion in January 2024? How are you addressing security and compliance challenges in this fast-evolving space? Let us know!
If you’re running a business that handles crypto transactions, prioritizing security and compliance isn’t just a “nice-to-have” anymore – it’s a must. Putting strong crypto identity verification processes in place can help protect your business from financial losses, keep you on the right side of regulations, and build trust with your customers.
Not sure where to start? Don’t worry – we’ve got you covered. This blog post will break down everything you need to know about crypto identity verification, why it matters, how it works, and how your business can benefit. Keep reading to stay ahead of the curve!
What Is Crypto Identity Verification?
Before we kick things off, let’s quickly break down what crypto identity verification is and why it’s so important.
Defining Crypto Identity Verification
Crypto identity verification is the process of authenticating the identity of individuals engaging in cryptocurrency transactions. Typically, it involves collecting and verifying personal data such as government-issued IDs, passports, or utility bills. Sophisticated fraud detection tools may also include biometric authentication, such as facial recognition, to ensure a person is present and legitimate during the verification process.
Curious about how biometric authentication can revolutionize security for your business?
How It Differs from Traditional Identity Verification
Traditional identity verification relies on direct relationships with financial institutions, where individuals are easily identifiable. Crypto transactions, on the other hand, are pseudonymous – wallet addresses are used instead of names – which makes them harder to trace. This adds a layer of complexity that requires technology-driven solutions to verify users accurately.
The Role of KYC and AML Protocols in Crypto Identity Verification
KYC and AML protocols play a pivotal role in shaping crypto identity verification.
Here’s how:
KYC (Know Your Customer)
This process involves verifying customer identities to ensure that individuals are who they claim to be. By collecting and validating personal information, such as government-issued IDs and proof of address, crypto platforms can prevent fraudulent activities like identity theft and account takeovers.
Implementing KYC is not just a best practice for increasing platform security; it is also a legal requirement in many jurisdictions, helping platforms comply with regulations and build trust with their users.
AML (Anti-Money Laundering)
AML protocols are designed to combat money laundering, terrorist financing, and other illegal financial activities. These measures involve monitoring transactions, identifying suspicious activities, and reporting them to regulatory authorities.
Businesses in the crypto space that fail to comply with AML regulations not only risk hefty fines and legal penalties but also damage their reputation. By implementing AML protocols, companies create a safer financial ecosystem while ensuring compliance with international standards.
Why Is Crypto Identity Verification Essential for Your Business?
The increasing sophistication of identity theft and fraud in the crypto space makes it critical for businesses to adopt comprehensive identity verification solutions.
Here are some primary reasons why your business needs crypto identity verification systems:
Prevent Fraud and Cyberattacks
Cryptocurrency platforms are prime targets for fraudsters. Identity verification adds layers of security, safeguarding your platform from threats.
Ensure Regulatory Compliance
Failing to comply with KYC/AML regulations could expose your business to significant fines or even shutdowns.
Build Customer Trust
Customers are more likely to trust a platform that emphasizes security and transparency. By implementing verification, you create a safer user environment.
Protect Against Financial Losses
Crypto identity verification helps prevent chargebacks, fraudulent claims, and other financial risks associated with scams.

How Does Crypto Identity Verification Work?
Crypto identity verification is a crucial process designed to ensure the security and compliance of cryptocurrency transactions while protecting users from fraud. Here’s an overview of how it works and the steps involved:
Overview of the Crypto Identity Verification Process
Crypto identity verification involves several layers of checks and authentication to confirm the identity of users and prevent illegal activities like money laundering or fraud. The process typically includes user registration, document submission, KYC (Know Your Customer) and AML (Anti-Money Laundering) checks, biometric verification, and advanced liveness detection to ensure the legitimacy of users.
Step-by-Step Breakdown:
- User Registration and Document Submission: The process begins with users registering on the platform and submitting their personal data and required documents. This typically includes a government-issued ID, passport, or utility bills to verify their identity and address.
- Document Verification: Advanced systems scan and validate the submitted documents to ensure they are legitimate and not tampered with. Any discrepancies are flagged for manual review.
- Biometric Authentication: Users undergo biometric verification, such as facial recognition, to confirm their identity. This ensures that the individual submitting the documents is the same person attempting to access the platform.
- KYC/AML Checks and Compliance Procedures: Know Your Customer (KYC) and Anti-Money Laundering (AML) checks are integral parts of the process. These checks cross-reference submitted data with global watchlists, databases, and risk profiles to ensure compliance with regulatory standards.
- Liveness Detection: To prevent spoofing attempts, liveness detection is employed. This technology confirms that the person verifying their identity is physically present and not using a static image or pre-recorded video.
- AI-Powered Fraud Detection and Risk Analysis: Artificial intelligence tools are used to identify suspicious patterns, detect fraud attempts, and analyze risk levels. This adds an extra layer of protection against identity theft or other malicious activities.
- Real-Time Transaction Monitoring: Transactions are continuously monitored in real time to detect any unusual or high-risk activities. This helps prevent fraudulent behavior and flag potential security threats promptly.
- Multi-Factor Authentication (MFA): Additional security is provided by requiring users to authenticate through multiple methods, such as a password combined with a one-time code sent via SMS or email.
- Data Encryption for Secure Storage and Transmission: All user data is encrypted to protect it during storage and transmission, safeguarding sensitive information from hackers or data breaches.
- Integration with Crypto Wallets and Platforms: The identity verification process is seamlessly integrated with crypto wallets and platforms, ensuring a smooth user experience while maintaining a high level of security.

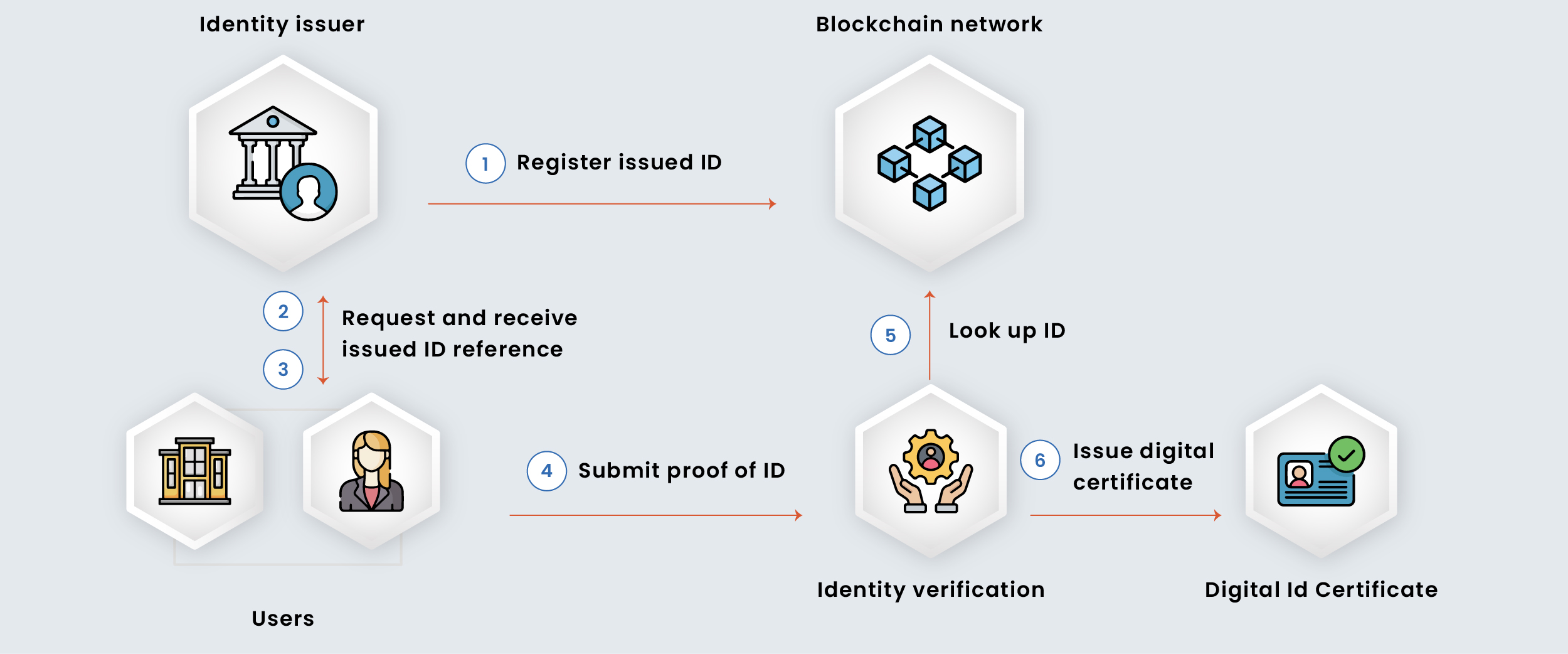
Key Components of a Secure Crypto Identity Verification System
For crypto businesses aiming to ensure robust security and fraud prevention, the following components are essential in identity verification systems:
- Document Verification: This involves authenticating official documents like IDs, passports, and utility bills to confirm a user’s identity. Advanced technology ensures that fake or altered documents are flagged immediately.
- Biometric Authentication: Using features like facial recognition, biometric authentication provides an added layer of security by verifying that the user is who they claim to be. This method also helps prevent identity theft.
- AI and Machine Learning: These technologies play a crucial role in identifying patterns of fraud, analyzing user behavior, and assessing risk profiles in real time. This continuous learning improves system accuracy over time.
- Liveness Detection: Ensures that the user is physically present during the verification process, helping to block spoofing attempts, such as using photos or pre-recorded videos.
- Geolocation and IP Monitoring: Tracks the user’s location and IP address to detect access attempts from suspicious regions or devices, further reducing the likelihood of unauthorized access.
- Data Encryption: Uses advanced encryption protocols to secure all user data, ensuring that sensitive personal information remains private and protected from breaches or leaks.
- Compliance Reporting: Helps crypto businesses adhere to KYC (Know Your Customer) and AML (Anti-Money Laundering) requirements, ensuring a legal and trustworthy operation. Detailed logs and reports can be generated for audits.
- Blockchain Integration: Creates traceable, tamper-proof records of all identity verification and account activities, enhancing transparency and accountability while reducing fraud risks.
- Real-Time Monitoring of Transactions: Tracks all ongoing transactions to identify and flag suspicious activities instantly. This feature helps prevent unauthorized or illegal transactions from being processed.
Benefits of Implementing Crypto Identity Verification for Your Business
Implementing crypto identity verification is essential for businesses navigating the digital age, where security, compliance, and trust are key.
Here are some of the benefits:
Enhanced Security Against Fraud and Cyberattacks
Crypto identity verification helps protect your business from fraudulent activities by verifying users’ identities with advanced blockchain technology. This reduces the risk of unauthorized access and cyberattacks.
Compliance with KYC/AML Regulations
Stay on top of regulatory requirements like Know Your Customer (KYC) and Anti-Money Laundering (AML). Crypto identity verification ensures your business operates within legal guidelines, avoiding fines or penalties.

Improved Customer Trust and Confidence
By implementing secure identity verification, you demonstrate your commitment to safeguarding customer data, building trust and confidence among your users.
Seamless User Experience and Faster Onboarding
Simplify the onboarding process for your customers. Crypto identity verification eliminates unnecessary steps, allowing users to verify their identity quickly and start using your services without delays.
Lower Risk of Financial Losses and Penalties
Fraudulent transactions and non-compliance can be costly. Crypto identity verification minimizes these risks, protecting your business from financial losses and regulatory penalties.
Increased Operational Efficiency
Automating identity verification with crypto technology reduces manual processes, increasing efficiency and allowing your team to focus on other priorities in your business.
Protection Against Money Laundering and Terrorist Financing
Prevent illegal activities like money laundering and terrorist financing by ensuring only legitimate users can access your platform. Crypto identity verification adds a strong layer of security to safeguard your business.
Ability to Scale and Handle Larger User Volumes
As your business grows, crypto identity verification can scale to handle increasing user volumes without compromising speed or security.
Competitive Advantage in a Trust-Based Market
In a market where trust is crucial, offering reliable identity verification gives your business a competitive edge, attracting customers who value security and transparency.
Reduced Risk of Chargebacks and Fraudulent Claims
Verify users before transactions to lower the chances of chargebacks and fraudulent claims, saving your business time and money in the long run.

Crypto Identity Verification: The Challenges You Need to Address
Identity verification in the crypto space is critical for security, compliance, and user trust.
However, it comes with unique challenges that must be addressed to ensure seamless operations:
- Scalability Issues with Increasing User Base: As the number of users grows, the verification system must handle high volumes without delays or crashes, requiring robust and scalable infrastructure.
- Balancing Security with User Experience: Enhanced security measures often result in a more complex user experience, which could lead to user frustration or drop-offs. Striking the right balance is essential.
- High Costs of Implementing Secure Systems: Developing or adopting secure identity verification systems involves significant investments in technology, infrastructure, and expertise.
- Complexity in Complying with International Regulations: Crypto platforms must navigate a patchwork of global regulations, including differing KYC and AML requirements, which can be overwhelming to manage.
- Risk of False Positives or Errors in Verification: Mistakes in the verification process, such as false positives or rejecting legitimate users, can damage user trust and disrupt platform growth.
- Data Privacy and Protection Concerns: Safeguarding sensitive user data is critical, especially in light of increasing concerns about data breaches and compliance with privacy laws like GDPR.
- Handling Non-Standard or Unverifiable Documents: Verifying users with incomplete or non-standard documentation, common in international or underbanked regions, can be difficult.
- Integration with Existing Crypto Infrastructure: Identity verification solutions must seamlessly integrate with existing platforms without disrupting the user experience or underlying architecture.
- Evolving Technology and Fraud Tactics: Fraudsters continually adapt, making it essential to update verification systems to counteract new tactics and ensure ongoing security.
- User Resistance to Extensive Verification Processes: Some crypto users value anonymity and may resist verification processes they perceive as intrusive, requiring platforms to manage this resistance carefully.
Choosing the Right Crypto Identity Verification Software: Features to Look For
Selecting the right software for identity verification can significantly enhance platform security and compliance.
Key features to consider include:
- Automation of KYC/AML Checks: Automated checks streamline compliance processes, reducing manual effort and ensuring real-time verification.
- Scalability: The system must adapt to increasing user numbers without sacrificing speed or accuracy.
- Support for Various Crypto Wallets: Compatibility with different wallet types ensures accessibility for a broader range of users.
- Multi-Factor Authentication (MFA): MFA adds an additional layer of security, protecting accounts from unauthorized access.
- Real-Time Verification and Monitoring: Instant verification processes improve user experience while keeping security intact.
- Blockchain Integration for Immutable Data: Storing verification data on the blockchain ensures immutability, enhancing trust and transparency.
- Compliance Reporting and Audit Trails: Built-in reporting tools simplify regulatory compliance and allow for easier auditing.
- User-Friendly Interface: A simple and intuitive design minimizes friction for users and administrators alike.
- Global Regulatory Support: A system that supports compliance with international laws makes expansion into new markets easier.

How to Integrate Crypto Identity Verification into Your Platform
Integrating crypto identity verification into your platform requires careful planning and execution to ensure a smooth transition.
Follow these steps to implement a robust system:
- Select a Crypto Identity Verification Provider: Choose a provider with a proven track record, robust features, and compatibility with your platform’s needs.
- Ensure API Compatibility with Your Platform: Verify that the provider’s APIs can seamlessly integrate with your existing platform infrastructure.
- Set Up KYC/AML Compliance Protocols: Establish protocols to handle know-your-customer (KYC) and anti-money laundering (AML) requirements efficiently.
- Configure Multi-Factor Authentication (MFA) Settings: Implement MFA to add additional layers of security for user accounts.
- Integrate Biometric and Document Verification Features: Use advanced features like facial recognition and document verification to enhance accuracy.
- Implement Real-Time Verification and Monitoring: Enable systems that can process user details instantly and flag suspicious activity in real time.
- Establish Data Encryption and Privacy Measures: Protect sensitive user data by employing robust encryption and adhering to privacy regulations.
- Test the Integration with a Sample User Base: Conduct extensive testing with a small group to identify and fix any issues before full deployment.
- Create Compliance Reporting and Audit Trail Capabilities: Implement tools to track and document verification processes for regulatory purposes.
- Conduct Regular Updates and System Maintenance: Keep your system updated to counter new fraud tactics and ensure optimal performance.
- Train Support Teams on the New Verification System: Equip your support staff with the knowledge and tools needed to assist users effectively.
Conclusion
The cryptocurrency market moves fast, but it’s vital not to sacrifice security for speed. As this industry continues to grow and evolve, implementing a robust crypto identity verification system is crucial.
Such systems protect your business from fraud by ensuring that only legitimate users gain access to your platform. They also help you stay compliant with regulatory requirements, avoiding costly penalties and legal challenges. Beyond compliance, strong identity verification builds trust with your users, showing that their safety is your priority.
In a rapidly expanding and competitive market, having these measures in place not only safeguards your business but also gives you a significant edge over competitors who fail to prioritize security.
Secure your crypto platform with confidence.
Discover our advanced identity verification solutions designed to shield your business from fraud and enhance security. Don’t wait – contact us today to schedule a consultation and experience the difference with a personalized demo!
