How secure is your customer facial recognition system? What if a bad actor used a photo to “spoof” your customer? Would your system catch it?
Online transactions have come a long way. However, digital thieves have developed sophisticated ways to bypass them, like spoofing. And that’s why liveness detection is necessary.
According to Deloitte, synthetic identity fraud will generate at least $23 billion in losses by 2030. We have a foolproof plan for you. Contact us to get started.
Liveness detection refers to technology that confirms the user is a real, live person. It detects eye movements, head rotation, and uses 3D depth perception to determine that the user is there and not a photograph.
The result: Improved security and a significant reduction in deep-fake and spoofing attacks. For businesses, liveness detection is an important tool for online age verification systems. It builds trust, protects your customers, and is an effective digital fraud prevention tool.
What Is Liveness Detection?
The story of liveness detection, dating back to 1950, is a narrative that’s compelling. Alan Turing first coined the mechanism shaping this process. He conducted an experiment that would test the ability of a machine to exhibit intelligence during an imitation game, later named the Turing test.
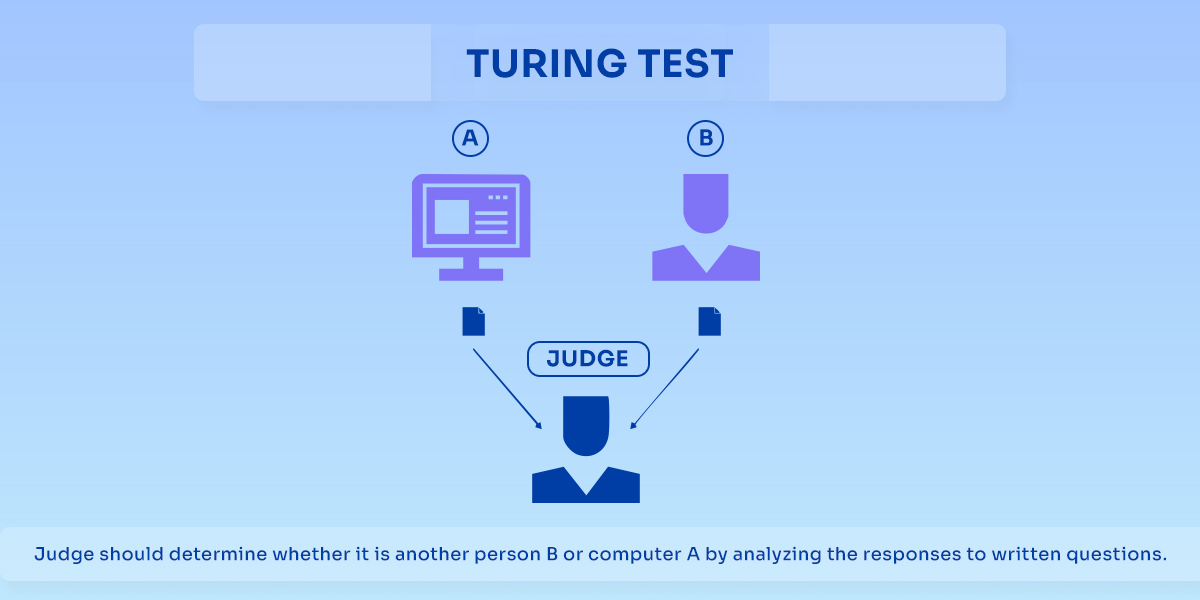
Turing wanted to make a machine so clever that you can’t tell it apart from a person. But how do you put things in motion? Well, you’ve got someone – let’s call them the judge – sitting in a room. They’re typing questions, and they’re getting answers back. Now, on the other side of the wall, there’s a real person and a computer. The judge has to figure out which is which just by reading the answers.
If the judge reads the responses and says that they have been made by a human, and if the judge’s wrong, then the machine has won.
Now, fast forward a few decades. Turing’s approach can now be used on a more serious level. How does one confirm it’s really “you” online? There’s no tricking the judge anymore. We are trying to keep things safe and private.
Many online age verification systems use photo authentication. You provide your driver’s license, and then take a photo, which is verified against your ID photo.
Liveness detection, or spoof detection, systems take this a step further. While taking a photo, a liveness check is performed that uses visual evidence to ensure you aren’t taking a photo of a photo. You might be asked to move the camera, for example, to provide a 3D representation, which helps confirm that you are a real, live person. Some benefits include:
- Combats spoofing: Attempts to catch fake facial representations like photos, videos, or masks.
- Multiple techniques: Analyzes eye movement, head rotation, 3D depth perception, and even subtle facial expressions to verify liveness.
- Safeguards sensitive data: Protects users’ personal information.
Purpose and Growing Need for Liveness Detection

Everything is digital now. But here’s the thing: the more we put our lives online, the more we need to make sure things are secure. And that’s where liveness detection comes in.
1. Rising Security Concerns in Digital Identity Verification
We trust computers to decide if someone’s really them based on a picture and some data. That’s a huge responsibility. And sadly, there are always people out there trying to game the system. You’ve probably heard stories – someone uses a fake ID or holds up a photo of someone else to fool a facial recognition system. That’s not a minor hiccup, it can cause grave problems like identity theft, fraud, and all sorts of illegal activities. This makes digital identity verification all the more important and worth paying attention to.
2. Prevention of Spoofing Attacks (photos, videos, masks)
People are getting really creative with how they try to trick these systems. We’re talking about high-quality printed photos, deepfake videos that look incredibly real, and even masks that are so detailed, they can fool some cameras. It’s like a digital arms race, really. The folks designing these security systems have to keep coming up with ways to tell the difference between a real, live person and a clever fake.
How Liveness Detection Works
Let’s break down the process of how liveness detection works, step by step.

The journey begins with capturing the user’s image. This initial step is critical, as the quality of the image directly impacts the accuracy of subsequent analysis.
Camera Types (2D vs. 3D Cameras)
1. 2D cameras capture flat images, relying on texture and motion analysis. They’re common but can be susceptible to sophisticated spoofing.
2. 3D cameras, equipped with depth sensors, capture detailed 3D representations of the face. This provides a richer dataset, enabling more accurate depth and shape analysis.
Step 2. Data Preprocessing
The captured image isn’t ready for analysis; it needs refinement. This step cleans and prepares the image for feature extraction.
- Noise Reduction: Eliminating artifacts and distortions that can interfere with analysis. This ensures that the system focuses on relevant facial features.
- Image Normalization: Standardizing the image’s lighting, contrast, and orientation. This ensures consistency and comparability across different captures.
Step 3. Feature Extraction
This is where the system identifies and extracts key facial features that differentiate a live person from a spoof.
- Face Shape, Texture, Reflection: Analyzing the contours, surface details, and light reflection patterns of the face. This helps detect anomalies that indicate a spoof.
- Eye Movement Tracking: Monitoring subtle eye movements, including blinking and pupil dilation. This can identify inconsistencies that suggest a static image or video.
- Skin Tone Consistency Check: Assessing the uniformity of skin tone and texture. This helps detect artificial skin or masks.
Step 4. Liveness Analysis Techniques
This is the core of liveness detection, where the extracted features are analyzed to determine authenticity.

2D vs. 3D Depth Mapping
1. 2D analysis focuses on texture and motion.
2. 3D depth mapping creates a detailed 3D model of the face, enabling precise depth analysis.
- AI-Driven Anti-Spoofing Detection: Advanced AI algorithms analyze the extracted features, looking for patterns and anomalies that indicate a spoof. These algorithms are trained on vast datasets of real and fake faces, enabling them to detect even subtle signs of spoofing.
Step 5. Decision Making & Authentication
The final step involves making a decision based on the analysis.
Confidence Scoring in Liveness Detection: The system assigns a confidence score to the liveness assessment. A high score indicates a high probability of a live user.
Machine Learning Model Validation: The decision is validated against machine learning models trained to recognize liveness. This ensures accuracy and reliability. This step is about providing a quantified measure of certainty.
The process of liveness detection is a complex interplay of image processing, feature extraction, and AI-driven analysis.
Key Industries Using Liveness Detection
Liveness detection is something that no industry can afford to sleep on. It’s a security layer that’s becoming a must-have across a spectrum of industries. Forget the generic “digital transformation” buzzwords. This is about real-world, high-stakes applications where identity verification is non-negotiable.
1. Banking & Finance
The financial sector, perpetually under siege from sophisticated fraud, has embraced liveness detection as a core component of its defenses. And it is one of the major industries where frauds occur significantly higher.

2. eKYC
Gone are the days of physically hauling documents to a branch. Opening a bank account online is now a reality, but it comes with inherent risks. Liveness detection ensures the person applying is genuinely who they claim, not an identity thief using stolen credentials. The tech scrutinizes facial features, analyzes micro-movements, and detects subtle signs of spoofing, all in real-time.
3. Fraud Prevention
Beyond account opening, liveness detection acts as a vigilant sentinel against fraudulent transactions. Whether it’s preventing unauthorized access to accounts, detecting synthetic identity fraud, or thwarting account takeover attempts, this technology adds a crucial layer of security. Suppose omeone trying to access your account with a deepfake video—liveness detection can be the difference between a successful breach and a thwarted attempt.
4. Cryptocurrency & Blockchain
The decentralized nature of cryptocurrency and blockchain, while revolutionary, also presents unique security challenges. In a world where trust is often code-based, verifying identities is paramount.
5. KYC and AML Compliance
Regulatory pressures are mounting, demanding robust KYC (Know Your Customer) and AML (Anti-Money Laundering) measures. Liveness detection helps crypto exchanges and blockchain platforms meet these requirements, ensuring compliance and preventing illicit activities.
6. Fraud Prevention and Account Security
Scams, hacks, and fraudulent transactions are rampant in the crypto space. Liveness detection adds a layer of security, verifying users during onboarding and transactions. This protects users from phishing attacks, account takeovers, and other forms of fraud.
Applications & Use Cases
Liveness detection is a practical technology with real-world applications ranging over multiple industries.
1. eCommerce
Selling alcohol, tobacco, or even certain video games online is a tightrope walk. You’ve got to make absolutely sure you’re not selling to minors. A simple “I’m over 21” checkbox just doesn’t cut it. You need real proof. Liveness detection analyses facial features, movement, and other subtle cues to confirm the buyer’s age in real time. It’s about protecting your business from legal trouble and, more importantly, protecting young people.
2. Tobacco Stores
Self-checkout kiosks are a boon for convenience, but they can be a headache for age-restricted sales. You can’t just rely on a customer’s honesty. Liveness detection integrates seamlessly with these systems, adding a layer of automated age verification. It scans the customer’s face, checks for signs of life, and compares it against age databases, all within seconds.
3. Online Gaming
Online gaming isn’t just fun and games. It’s a massive industry with a lot of potential for abuse. Gaming platforms need to keep things fair and safe. Liveness detection helps them verify players’ identities, ensuring that everyone’s playing by the rules. It keeps the game clean and the community protected.
4. Convenience Stores
Quick trips to the convenience store shouldn’t mean bypassing age verification. When customers are buying age restricted goods, it is important to verify their age. Liveness detection can be used at self-service checkouts, to automate this process. This speeds up the checkout process and makes sure that the sales are legal.
5. Types of Liveness Detection
Liveness detection is a nuanced field with various methodologies, each with its own strengths and weaknesses. Understanding these differences is crucial for choosing the right approach for a given application.
Active Liveness Detection
This method demands user participation, requiring specific actions to prove they’re a real person.
Users are prompted to perform tasks like blinking their eyes, turning their heads, or smiling. The system analyzes these actions to confirm liveness. This approach is straightforward and can be effective, but it’s not without its drawbacks.
Active liveness can be cumbersome and frustrating for users. Think about trying to blink precisely on cue while holding your phone steady. It can lead to high abandonment rates and poor user experience. Moreover, it’s susceptible to spoofing if the required actions are predictable or easily replicated. This is where the balance between security and usability becomes a tightrope walk.
Passive Liveness Detection
This method works quietly in the background, analyzing biometric data without explicit user input. It’s the digital equivalent of a seasoned security guard who can spot a fake from a mile away.
Passive liveness analyzes facial texture, depth, and reflections using advanced AI algorithms. It doesn’t require users to perform any specific actions, making it more convenient and less intrusive.
This approach leverages sophisticated AI models to detect subtle cues that distinguish a real person from a spoof. It analyzes the texture of the skin, the depth of the face, and the way light reflects off the surface. This method is more robust against sophisticated spoofing attempts.
More Seamless User Experience: The seamless nature of passive liveness makes it ideal for applications where user experience is paramount. It minimizes friction and enhances user satisfaction.

Hybrid Liveness Detection
This method combines the strengths of active and passive liveness, offering a balanced approach to security and usability. Think of it as a well-rounded security professional who can adapt to any situation.
Hybrid liveness uses active prompts and passive analysis to verify user identity. It might start with a passive analysis and then prompt the user to perform a specific action if the initial analysis is inconclusive.
By combining these methods, hybrid liveness can achieve a higher level of security without sacrificing usability. It provides a robust defense against spoofing while minimizing user frustration. This approach recognizes that security and convenience are not mutually exclusive.
Liveness Detection Techniques
Liveness detection isn’t a singular method; it’s a collection of techniques, each with its own strengths and applications. These techniques work in concert to build a robust defense against spoofing.
1. Computer Vision-Based Techniques
Computer vision forms the foundation of many liveness detection systems. It’s about teaching machines to “see” and interpret visual data.
Facial Recognition & Motion Detection
Facial recognition identifies and verifies a person based on their facial features.
Motion detection analyzes movements in the captured image, looking for natural head movements or blinks.
Texture Analysis
This technique scrutinizes the surface details of the skin, identifying inconsistencies that may indicate a printed image or a mask. It’s about looking at the minute details that a human eye may miss.
3D Depth Sensing
Using depth cameras or structured light, this technique creates a 3D model of the face. It allows for accurate depth analysis, making it difficult to spoof with 2D images or masks.
2. AI & Machine Learning-Based Techniques
AI and machine learning elevate liveness detection to a new level of sophistication. They enable systems to learn and adapt, becoming increasingly adept at detecting spoofing attempts.
Deep Learning-Based Face Analysis
Deep learning algorithms, particularly Convolutional Neural Networks (CNNs), are trained on vast datasets of real and fake faces. They learn to recognize subtle patterns and anomalies that distinguish a live person from a spoof.
Convolutional Neural Networks (CNN) for Liveness Detection
CNNs excel at image recognition. They analyze facial features and patterns, identifying signs of spoofing with high accuracy. They learn from massive datasets, increasing their accuracy over time.
3. Hardware-Based Techniques
Hardware-based techniques add a layer of physical security, leveraging specialized sensors to capture biometric data.
Infrared Sensors for Heat Detection
Infrared sensors detect heat signatures, ensuring that the captured image is of a live person and not a cold, inanimate object.
Depth Cameras & LiDAR Sensors

These sensors provide detailed 3D depth information, making it extremely difficult to spoof with 2D images or masks. LiDAR provides very accurate in-depth information.
4. Behavioral Analysis
Behavioral analysis focuses on analyzing subtle user behaviors that are difficult to replicate.
Micro-expressions
Analyzing subtle facial expressions that are often involuntary. These expressions can reveal underlying emotions and intentions.
Blink Detection
Analyzing the frequency and pattern of blinks. Natural blinking patterns are difficult to replicate in a spoof.
5. Multi-Modal Liveness Detection
Multi-modal liveness detection combines multiple biometric inputs, enhancing accuracy and security.
Face + Voice Authentication
Combining facial recognition with voice analysis. This adds a layer of auditory verification, making it more difficult to spoof.
Fingerprint + Facial Recognition
Combining fingerprint scanning with facial recognition. This adds a layer of physical biometric verification.
These techniques, working in concert, create a robust and multi-layered defense against spoofing. Each technique adds a unique layer of analysis, making it increasingly difficult for fraudsters to bypass the system.
Technologies Used in Liveness Detection
Liveness detection isn’t built on solitary technology; it’s a perfect mixture of cutting-edge innovations.
Artificial Intelligence & Deep Learning

AI and deep learning are the cornerstones of modern liveness detection, enabling systems to learn, adapt, and detect increasingly sophisticated spoofing attempts.
AI algorithms analyze vast datasets of facial images and videos, learning to distinguish between real and fake faces.
Deep learning, particularly Convolutional Neural Networks (CNNs), excels at image recognition and pattern analysis, identifying subtle cues that indicate spoofing.
2. Computer Vision & Image Processing
Computer vision and image processing techniques are essential for capturing, analyzing, and enhancing facial images.
These technologies enable systems to extract key facial features, analyze texture and motion, and detect inconsistencies that may indicate a spoof.
Image processing techniques are used to enhance image quality, reduce noise, and normalize images for accurate analysis.
3. Neural Networks (CNN, RNN)
Neural networks, particularly CNNs and Recurrent Neural Networks (RNNs), are crucial for analyzing complex visual data and detecting patterns.
CNNs are highly effective at image recognition, analyzing facial features and patterns with remarkable accuracy.
RNNs can be used to analyze video feeds, and track subtle changes over time, to aid in detecting replay attacks.
4. Biometric Sensors (IR, LiDAR, 3D cameras)
Biometric sensors provide detailed physical data that enhances the accuracy of liveness detection.
Infrared (IR) sensors detect heat signatures, ensuring that the captured image is of a live person.
LiDAR and 3D cameras capture detailed 3D depth information, making it extremely difficult to spoof with 2D images or masks.
5. Edge Computing for Real-Time Processing
Edge computing enables real-time processing of biometric data, crucial for fast and efficient liveness detection.
Processing data on the edge, closer to the source, reduces latency and enhances responsiveness.
This is particularly important for applications that require immediate authentication, such as online transactions and access control.
6. Blockchain for Secure Identity Verification
Blockchain technology can enhance the security and integrity of identity verification processes.
Blockchain provides a secure and immutable ledger for storing and verifying identity data.
This can help prevent identity theft and fraud, ensuring that identity information is accurate and tamper-proof.
7. Cloud vs. On-Device Processing
The decision to process biometric data in the cloud or on the device is a critical strategic choice.
Cloud processing offers scalability and powerful computing resources, but it raises privacy concerns.
On-device processing enhances privacy and reduces latency, but it may be limited by device capabilities.
Wrapping Up
From safeguarding our financial accounts to improving age verification online, liveness detection is a powerful tool for business. That’s especially true as spoofing and deepfake attacks advance. In fact, according to the South China Morning Post, a company just lost $25 million due to a deepfake attack.
Ultimately, liveness detection systems continue to advance. They’re more user-friendly and seamless than ever. And businesses can incorporate them into onboarding to protect their customers and their bottom line.
