For a growing number of retailers, steering the digital marketplace has become a delicate balancing act. While the opportunity for growth is immense, so are the regulatory challenges. The days of simply adding an “Are you 21?” checkbox at checkout are long gone. Today, online and brick-and-mortar retailers alike face mounting legal obligations to verify customer age, not just to comply with laws, but to maintain good standing with payment gateways, advertising platforms, and brand partners.
From the FDA’s strict regulations on tobacco and vaping products to state-specific cannabis laws, the landscape is complex and unforgiving. This guide highlights the top age verification solutions that go beyond the basics to provide seamless, secure, and legally compliant tools for your business.
What Is Age Verification Software?

Age verification (AV) software is a digital tool designed to confirm that a user or customer is legally old enough to purchase a specific product or access a particular service. For a retailer, this is the digital bouncer at the door, ensuring you don’t serve a minor.
The applications are broad and critical:
- Restricted Goods: This includes online and in-store sales of tobacco, vape products, cannabis, and alcohol.
- Sensitive Content: Access to adult-oriented websites, gaming platforms, and other digital services.
- Financial Services: Opening accounts, applying for loans, or engaging in online gambling.
Modern AV has evolved far beyond a simple date-of-birth input. The technology now incorporates sophisticated methods like AI-powered ID scanning, biometric analysis, and facial liveness detection to deliver irrefutable proof of age while creating a frictionless experience for the legitimate customer.
7 Best Age Verification Companies for Retailers
Finding the right age verification software is a strategic decision that impacts everything from compliance to customer experience. Here is a curated list of the leading solutions for 2026, each with a unique set of features tailored to different business needs.
1. FTx Identity
FTx Identity is a standout solution, particularly for retailers in high-compliance sectors like tobacco, vape, and cannabis. Its core strength lies in its seamless integration with retail operations and its advanced biometric technology. The company’s long-standing expertise in the retail POS space makes it a natural fit for businesses seeking an all-in-one solution.
Key Features:
- Advanced facial recognition to match a user’s face with their ID photo.
- 3D liveness detection to prevent fraud using static photos, videos, or masks.
- Direct POS integration for on-the-spot age verification during in-store transactions.
- Comprehensive audit trail, logging every verification attempt with timestamps and results.
Pros:
- Deep integration with FTx POS and other retail systems for a smooth workflow.
- High accuracy rate to minimize false negatives and block fraudulent attempts.
- Strong focus on fraud prevention through sophisticated liveness detection and real-time scanning.
- Save on customer verification costs by eliminating repeat verification fees.
Industry Fit: High-compliance industries, including tobacco, vape, cannabis, and liquor stores. It also serves gaming, retail stores, ecommerce, etc.
2. Jumio
Jumio offers an identity verification platform that supports a variety of ID types and includes biometric and liveness detection features. It’s used by companies around the world, particularly those needing broad international coverage.
Key Features:
- Includes face biometrics to help match users with their IDs
- Offers liveness detection to help reduce spoofing risks
- Designed for businesses with international verification needs
Pros:
- Fast verification speeds, with many checks completed in seconds
- Helps identify a range of fraud attempts, from simple to more complex
- Generally considered secure and dependable
Industry Fit: Ecommerce, financial services, and online gambling platforms with international audiences.
3. Yoti
Yoti provides a digital identity tool designed to give users more control over their information. Through the app, individuals can create a verified digital ID on their smartphone, helping streamline age verification processes.
Key Features:
- Mobile app for storing a verified identity
- Option to reuse an existing ID to confirm age
- Basic liveness detection to confirm user presence
- Focus on privacy and user consent
Pros:
- Can simplify repeat visits for returning users
- Privacy features may appeal to some customers
- Generally quick for those already using Yoti
Industry Fit: Ecommerce, social platforms, and services that prioritize user-centric identity solutions.
4. Veriff
Veriff offers an AI-supported identity verification solution that emphasizes speed and efficiency. It uses live video to help assess identity in real time and aims to reduce fraudulent activity through automated checks.
Key Features:
- Video-based identity verification that reviews multiple data points.
- Automated decision-making for quicker results.
- Compatibility with a variety of international ID documents.
Pros:
- Offers relatively fast processing and can detect fraud that may be missed in static image reviews.
- Developer-friendly software development kit (SDK) that simplifies the integration process.
- Designed to handle a range of fraud scenarios, including more complex attempts.
Industry Fit: Fintech, gaming, and any online business where high-volume, real-time verification is crucial.
5. Onfido
Onfido offers an identity verification solution that uses document checks alongside facial recognition. It’s a commonly used option for businesses looking to streamline user verification.
Key Features:
- Matches a user’s ID with their facial biometrics.
- Includes liveness detection to help reduce the risk of spoofing or fake identities.
Pros:
- Designed to be scalable and adaptable to different business needs.
- Provides an application programming interface (API) that supports integration into various platforms.
- Emphasizes usability and security in its approach.
Industry Fit: Financial services, mobility services, and online marketplaces.
6. iDenfy
iDenfy provides an identity verification service that combines automated technology with manual review to help reduce fraud. The platform includes several standard features designed to support compliance and accuracy.
Key Features:
- ID verification using AI, supported by human review
- Biometric authentication options
- End-to-end identity verification tools
Pros:
- Balanced approach to accuracy with both automation and human oversight
- Includes tools for detecting potential fraud
- Offers multiple verification functions within one platform
Industry Fit: Fintech, cryptocurrency exchanges, and businesses with strict compliance requirements.
7. AgeChecker.Net
AgeChecker.Net is a commonly used option for ecommerce businesses looking for a basic age verification tool. It offers an automated system designed to simplify compliance with age-restricted sales requirements.
Key Features:
- Database checks using public and internal records
- Optional document upload if initial verification doesn’t pass
- Integrates with platforms such as Shopify and WooCommerce
Pros:
- Relatively easy to set up
- Reasonable pricing structure
- Designed to be customer-friendly
Industry Fit: Ecommerce retailers, particularly those selling tobacco, vape, and alcohol, with a need for a quick, reliable solution.
Why Age Verification Matters for Retailers

The value of age verification software extends far beyond a simple compliance check. It’s a foundational element of a modern, responsible retail business.
- Legal Compliance: Laws like the FDA’s Deeming Rule and state-level cannabis regulations require retailers to verify customers’ ages to prevent sales to minors. Failure to comply can result in hefty fines, license suspension, or even criminal charges.
- Liability and Chargeback Protection: For retailers, selling restricted goods to a minor can lead to significant legal liability. Robust age verification creates an auditable record, which can be critical for defending against chargebacks and legal challenges.
- Advertising & Platform Compliance: Platforms like Meta and Google have strict policies against advertising restricted products to minors. Proper age verification tools can help retailers prove compliance, preventing account suspensions and ensuring their ad campaigns can continue to run.
- Brand Trust and Customer Safety: Consumers today are more conscious of a brand’s ethical standing. By proactively protecting minors, a retailer builds trust and establishes a reputation as a responsible and safe place to shop.
How Minors Try to Bypass Online Age Verification
The digital world is full of loopholes, and minors are often adept at finding them. Retailers relying on outdated or weak systems are particularly vulnerable.
Common tactics include:
- Using a Parent’s Information: A minor might use their parent’s name, address, or even credit card information to appear as an adult.
- Prepaid Cards and Gift Cards: These are often used because they don’t have a linked name or age, bypassing traditional credit card checks.
- Fake IDs and Scanned Documents: In the absence of a proper ID scan a minor might upload a falsified or poorly edited document.
Advanced technology like biometrics and liveness detection solves this by creating a real-time, undeniable link between the person and the document. This prevents static images or fraudulent IDs from being used, effectively shutting down the most common circumvention methods.
Legal Risks of Not Using Proper Age Verification
Ignoring the need for robust age verification is a business risk that is simply not worth taking. The repercussions can be severe and long-lasting.
- State and Federal Fines: Regulators like the U.S. Food and Drug Administration (FDA) and state alcohol commissions have the authority to levy substantial fines for non-compliance. These penalties can run into the hundreds of thousands of dollars.
- Risk of License Suspension: For businesses in regulated industries, a failure to verify age can lead to the suspension or revocation of their operating license, effectively shutting down the business.
- Platform Bans: Ecommerce platforms like Shopify or payment processors like Stripe can suspend or ban retailers who violate their terms of service, which often include strict age verification mandates.
- Reputational Damage: News of a business selling restricted products to minors can cause irreparable harm to its public image, leading to a loss of customer trust and market share.
Choosing the Right Solution: Features to Look For

Selecting the best age verification software requires careful consideration of your business’s specific needs. Look for a solution with these essential features:
- Real-Time ID Scanning: The ability to instantly scan and verify government-issued IDs, like driver’s licenses and passports.
- AI or Biometric Detection: Technology that can confirm the user is a real person and not a bot or a static image.
- Multi-State or Global Legal Compliance: A platform that stays up to date with a changing regulatory landscape.
- POS and Ecommerce Integration: A solution that works seamlessly with your existing point-of-sale system and online store.
- Customer Experience: A tool that is mobile-ready and designed to minimize friction for legitimate customers.
- Comprehensive Audit Log & Reports: A system that automatically creates and stores a verifiable audit trail for compliance purposes.
- Fraud Detection: Robust features to identify and prevent the use of fraudulent IDs or other deceitful tactics.
Retail Use Cases for Age Verification Solutions
Different products, different problems. But one thing is consistent: guessing someone’s age doesn’t cut it anymore.
Here is how real retailers across different sectors actually use age verification solutions to protect their business and keep customers happy.
1. Alcohol Retail & Bars
Friday night. Twenty people are at the register. Someone’s buying a six-pack.
You don’t need a 30-second verification process. You need a beep, a green light, and a completed sale. The best age verification software here is the kind customers don’t even notice. Scan, verify, done.
2. Vape & Tobacco Shops
This one is about paperwork. Not just selling legally but proving you sold legally.
If you’re in tobacco, you know about Electronic Age and Identity Verification (EAIV). You know some manufacturers pay cash back for clean scan data. The right age verification tool doesn’t just check IDs—it builds your audit trail and helps you collect what you’re owed.
3. Cannabis Dispensaries
You don’t just verify buyers. You verify everyone who walks through the door.
That changes the volume game. Handheld scanners at reception, quick queue clearance, and zero room for error. An age verification service for dispensaries needs to handle foot traffic like a nightclub, with records like a bank.

4. Convenience Stores
Here is the trick: most of your customers aren’t buying alcohol or cigarettes.
So why slow them down? A smart online age verification software integration only triggers when a restricted item hits the scanner. No ID check for Gatorade and gum. Just a smooth, fast checkout for the rest who don’t need verifying.
5. Ecommerce
No physical ID. No human to judge. Just a browser window and a shopping cart.
The challenge is keeping verification strict enough to be legal but fast enough that customers don’t abandon the purchase. The winning e commerce age verification setup uses layered checks: database match first; document upload only when needed.
6. Online Gaming & Gambling
You cannot afford one mistake. One underage account and regulators start asking hard questions.
Verification happens at the front door, before a single bet is placed. This isn’t about convenience—it’s about your license. Age checking software in this space needs to cross-reference multiple databases and flag inconsistencies instantly.
Step-by-Step Age Verification Implementation Guide for Retailers
You know you need it. But figuring out where to start—without disrupting your store or confusing your customers—can feel overwhelming.
The truth? Implementing age verification solutions isn’t complicated when you break it down into actual, actionable steps. Here is exactly how to do it, from shelf to sale.
1. Assess Your Age-Restricted Product Categories
Walk your store. Better yet, walk your entire inventory list.
Not everything needs an ID check. Beer? Yes. Lighters? Maybe. Energy drinks? Probably not. Make a clean, honest list of exactly what triggers a verification requirement. This prevents you from slowing down customers who don’t need verifying in the first place.
Quick tip: Check your state regulations. Some products you think are fine might actually require age confirmation.
2. Map Your Customer Journey (In-Store + Online)
Grab a pen. Sketch it out.
Where does the customer first encounter the age check? At the door? At the register? During checkout on your website? Every touchpoint matters.
- In-store: Is it at the counter or on the sales floor?
- Online: Is it before they browse or only when they click “buy”?
Map both paths separately. They are not the same problem.
3. Select the Verification Method That Fits Your Needs
Now match the method to the moment.
- Bars & high-traffic registers: Speed matters. Go with ID scanning + facial matching.
- Tobacco shops: You need EAIV-compliant age verification software with reporting.
- Ecommerce: Start with passive database checks and escalate to document upload only when needed.
There is no single “best” method. There is only what fits your specific sale flow.

4. Integrate the Age Verification System into Retail Operations
This is where most people overcomplicate it.
Your age verification tool should live where the sale happens. Not on a separate tablet. Not on a staff phone. Inside your existing POS system.
- Scans should trigger automatically when restricted items are rung up.
- Approvals should appear on the same screen as the total.
- Rejections should lock the transaction.
If your staff must switch devices to verify, the system will fail on Friday night when it’s busy.
5. Train Your Staff Thoroughly
Here is the truth: your team will figure out how to bypass clunky systems to keep lines moving.
Don’t let that happen.
- Show them how fast the best age verification software actually is.
- Role-play the “sorry, I can’t sell this to you” conversation so it doesn’t feel awkward.
- Explain why it matters—fines, license risk, their own jobs.
Staff who understand the “why” don’t skip the step.
6. Test the System Before Full Deployment
You wouldn’t open a new store without testing the register. The same rule applies here.
Run a soft launch with:
- Real IDs (yours, your staff’s).
- Expired IDs (see what happens).
- Scanned copies, photos of photos (the fakes).
Fix the edge cases before real customers encounter them.
7. Monitor, Evaluate, and Optimize Performance
Go live. Then watch.
- How many verifications per day?
- How many rejections?
- Any bottlenecks forming at certain hours?
Good online age verification software gives you a dashboard. Use it. If you’re rejecting too many valid customers, adjust the sensitivity. If staff is skipping the step, retrain.
This is not a set-it-and-forget-it tool. It’s part of your operations now. Treat it like one.
How FTx Identity’s Age Verification Solutions Help Retailers
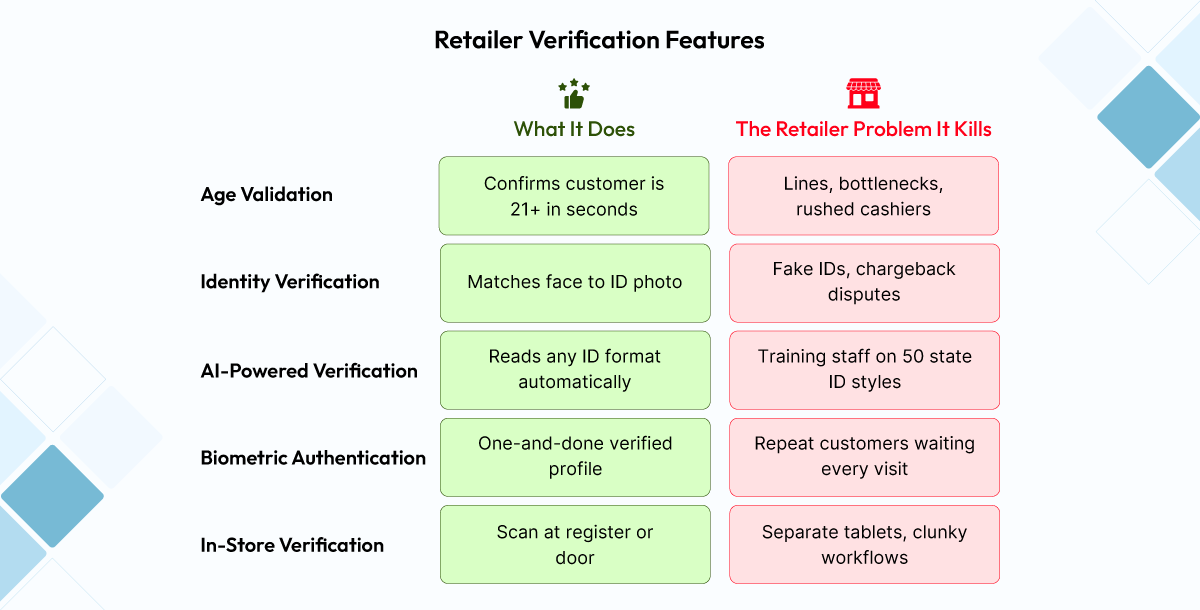
You’ve read about the features. Now let’s talk about what actually matters: what they do for your store, your staff, and your bottom line.
Here is exactly how FTx Identity solves real problems that age-restricted retailers deal with every single day.
1. Age Validation
This is the core. The non-negotiable.
FTx Identity reads the barcode, calculates the age, and returns a green or red light in under two seconds.
No keypad date entry. No mental math on expiration dates. No guessing if that out-of-state license is real.
What this means for you: Faster lines. Happier customers. Zero “I thought they were 21” moments during an audit.
2. Identity Verification
FTx Identity compares the face on the ID to the face standing in front of your cashier. Not later. Not at a separate kiosk. Right there, at the point of sale.
What this means for you: You stop selling to underage customers using someone else’s real ID. And when a parent disputes a charge, you have photo proof of exactly who picked up the order.
3. AI-Powered Verification
The AI doesn’t need to memorize.
Once customers scan their government-issued ID and take a live selfie, the FTx Identity AI cross-checks the data with public records. It reads the document structure itself—the ghost images, the microprint, the barcode placement—and validates it against known security features.
What this means for you: No software updates waiting on ID design changes. No training posters behind the register. It just works on whatever ID walks through your door.
4. Biometric Authentication
With FTx Identity, a verified customer can opt to save their biometric profile. Next visit? They look at the camera. The system recognizes them. Transaction continues.
What this means for you: Loyal customers feel like VIPs. Your line moves faster. And you still have a verified audit trail for every single transaction.
5. In-Store Age Verification
FTx Identity lives inside your FTx POS. No switching devices. No duplicate hardware. The verification window appears automatically when a restricted item is scanned.
What this means for you: Your staff uses one system. Your training is simpler. And on a busy Friday night, nobody is reaching for a second device while the line grows.
Final Thoughts: Protect Your Business with Smarter Tools
The trend is clear: future regulations will only get stricter. For retailers, investing in proper age verification isn’t an option; it’s a critical investment in long-term stability and growth.
For businesses in industries like tobacco, vape, and cannabis, a solution like FTx Identity is designed to meet these specific needs. With its robust facial recognition, 3D liveness detection, and seamless POS integration, it provides an airtight defense against fraud and a reliable partner in maintaining compliance. Protect your business, build customer trust, and secure your future with smarter age verification tools.
Stop Fines Before They Start
One failed age check could cost you thousands. Protect your business, your license, and your
reputation with FTx Identity’s bulletproof verification tools.
